Bolster is excited to share a major landmark in our path to making the internet a safer place…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
The Click That Stole Holidays: Black Friday and Cyber Monday Scams Unmasked
Introduction The onset of Cyber Monday and Black Friday deals is something we all stay up for. Whether it’s discounted vacation travel packages, instructional offers.
Exploring the Risks of IPFS in Phishing Attacks
Introduction The InterPlanetary File System (IPFS) is a cutting-edge technology designed to revolutionize how we store and share data across the internet. It offers a.

Phishing in Focus: Bolster's 2024 Mid-Year Phishing and Online Scam Update
With the unprecedented surge in phishing attacks sparked by AI, protect your business with data into key phishing and scam trends including election fraud, industry-targeting, and consumer interest scams.
Understanding Domain Reputation Attacks and How to Protect Your Brand
Without even defining the term, you could probably guess that…
The Full Guide to Protecting Yourself from Fake Sale Websites
Online shopping is no longer a hot trend or something…
Digital Risk Monitoring Importance is Growing Faster Than Ever
In a digital landscape that seems to be changing daily…
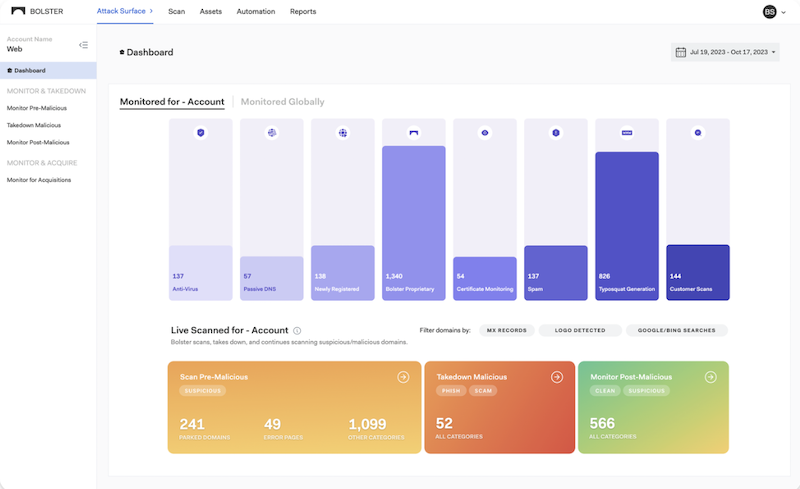
A Visual Journey: Exploring the Redesigned Bolster Dashboard
One of the top challenges that security practitioners often…
Cybersquatting: A Growing Threat in the Digital Age and How to Combat It
In today’s interconnected world, cybersquatting has become a prevalent…
The Power of Automated Domain Monitoring
Today, business owners around the world understand that digital…
Domain Risk Management - The Build vs. Buy Dilemma in 2023
Domain risks are growing increasingly aggressive, and detrimental to businesses…
Evaluating Web Scraping, Crawling, and Automation with NodeJS Libraries
This blog is part 1 of a web scraping…
How to Conduct a Website Takedown In 3 Easy Steps
Malicious website domains are a headache for organizations to…
How to Conduct a Website Takedown (The Hard Way), and How to Improve
If you have an online presence, chances are your…
What Are Lookalike Domains & How to Detect Them
Lookalike domains are fraudulent domains that mimic legitimate ones…
The Most Critical Domain Security Risks & Five Ways to Prevent Attacks
Security professionals are concerned about the security of their…