Malicious website domains are a headache for organizations to deal with, mainly because they are easy for hackers to put up, but difficult for security and risk teams to successfully takedown. Conducting a website takedown requires time and resources, not just to contact the right people (whether it’s lawyers, domain registrars, or regulatory groups), but also to detect the threat, and decide whether a fake domain is active and truly in need to takedown efforts.
In the first part of the website takedown blog series, we took you through the five not-so-easy steps required to take down a malicious website manually. If you read the piece, you know manual website takedowns are doable if time and patience are on your side, and if you’re not faced with any of the tricky situations that we outlined. But if you don’t have the time or the patience, or if you simply have too many sites to take down, an easier, more scalable, solution is best.
The 3 Easy Steps to Conduct a Malicious Website Takedown
It’s not only convenient to have a quick and easy process for website takedowns; it can be critical to the success of your business. If malicious domains remain active, they are able to communicate with your employees, prospects, and customers, and scam your unsuspecting audience into divulging sensitive information. The longer a malicious website is up and running, the more damage it can cause to your business (think brand reputation on top of financial headaches).
The manual process behind conducting a website takedown is not your only option. Here are the steps to combating malicious websites, the easy way.
Step 1: Select an automated domain monitoring and takedown solution
This simple first step will fundamentally change everything. We the right domain monitoring technology on your site, your security and IT team can confidently perform their jobs without constantly needing to assess domain risks. Automated domain management technology, when integrated with your network, will assess the domain threats targeting your network, and won’t require internal involvement from your team unless your team requires it.
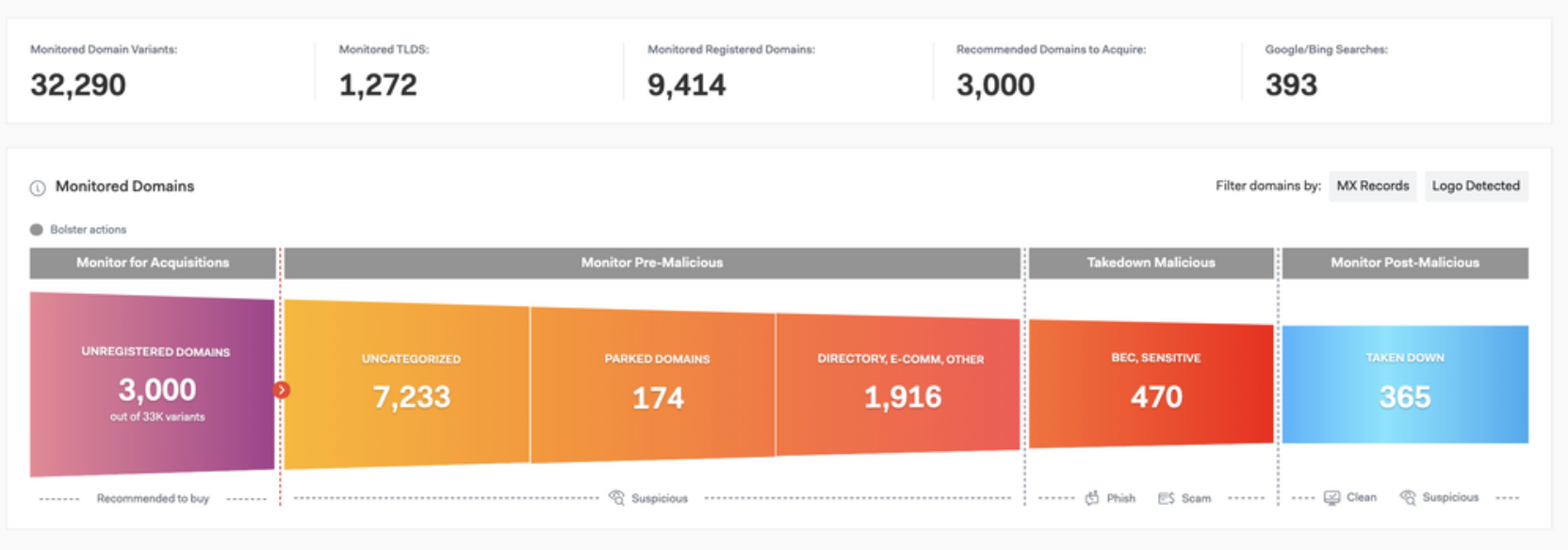
At Bolster, we provide businesses with the technology to manage domain risks without extending your team’s resources. With Bolster on your side, we will scour the internet to find a comprehensive assessment of all threats related to your brand and domains. Results are displayed in a real-time Domain Monitoring Dashboard where all domain variants (aka ‘typosquat domains’ or ‘look-alike domains’) both registered and unregistered are identified.
For all registered domains, the system will make an initial assessment. For a domain with active content, our system will scan it, render a verdict in milliseconds, and if found fraudulent, queue for takedown.
For a domain that’s registered but not yet live with content, our system will continually monitor conditions for changes in status and signs of weaponization. If a site does emerge, it will get scanned, a verdict will be rendered, and if necessary, will be scheduled for a website takedown.
Step 2: Sit back and watch the program conduct website takedowns
Yes really, it can be that simple. With the right domain monitoring technology, your business does not need to expend huge amounts of internal resources to effectively defend against website domain risks.
With Bolster, every site deemed malicious will trigger an automated takedown process. No need to collect info, fill out forms, or submit evidence. Our system does it all for you automatically in minutes. And our system and team have a number of different mechanisms to employ to see sites through to takedown.
API takedowns: We have extensive relationships with hosting providers, registrars, and registries globally. With some, we have API takedown integrations allowing takedown requests to be issued via API. This approach is the fastest, yielding results in minutes when dealing with credential theft sites.
Automated abuse reporting: If there isn’t a takedown API integration, the fallback is an automated submission via email API integration into the hosting provider’s abuse box or simply via an automated email with evidence. Here, automated takedowns are measured typically in hours.
Step 3: Monitor takedown success
After you’ve implemented an effective domain monitoring technology into your security and risk program, the last step is to report out on the success of your program to company stakeholders (and those who have a say in your security team’s budget). It also helps boost brand reputation when your organization has access to data about website takedowns and protecting your network. Bolster has robust reporting technology to help summarize the threats impacting your network, visualize trends, and prevent future security risks.
To date, Bolster has taken down well over 100,000 malicious websites globally. At the core, it’s the combination of the highly accurate evidence collected (our false-positive rate is 1 in 100,000), plus automation, plus our trusted global relationships that makes it all possible.
Note too, that once a takedown is completed, the site will be added to the ‘Monitor Post-Malicious’ category in the dashboard making tracking for re-occurrence a snap.
Scaling Your Website Takedown Process
These 3 simple steps are easily repeated, scaling to however big a problem you may have on your hands.
Our system has notched successes for our customers even when things get tricky. We mentioned in the previous blog that some takedowns are not always clear cut. Websites with active signs of credential theft are the easiest to work with. But sites that are infringing on your copyrights or trademarks are harder to take down, especially automatically.
Here, our detailed evidence, complete with logo abuse detection and screenshots, plus our trusted status globally work to your advantage. We can also issue DMCA Takedown Notices to bolster our takedown case. As discussed in the previous blog, DMCA Takedown Notices are an effective measure but only enforceable in the United States. When dealing with sites infringing on copyrights and trademarks, takedown time is measured typically in a few days.
There are also the cases where we’re dealing with a not-so-cooperative hosting provider or hosting country. Here again, our experience and relationships (especially with anti-abuse authorities) work to your advantage allowing for takedown success where you would otherwise strike out.
Website takedowns: No longer a guessing game
While taking a website down can be tricky, it can be even trickier to keep it down. It’s very easy for a bad actor to simply re-host the website on another provider network. At this point, the endless whac-a-mole™ game is invoked, with the site perpetually being taken down only to re-emerge. Our system puts an end to this game. Full stop. Here’s how:
Continuous monitoring: For every site taken down, the system will continue to monitor the internet for signs of re-occurrence. If the site does re-emerge, anywhere globally, we will invoke our takedown process automatically. This causes bad actors to lose interest, at least with that particular domain, and puts an end to the whac-a-mole™ game.
Submissions to global blocklists: In addition to executing a site takedown, our system also submits the site address to global blocklists including anti-phishing working groups, safe browsing communities, and publicly available threat intel feeds. This serves as added protection, ensuring a site is not reachable at the browser level despite potentially still being up.
Read More: Top Phishing Threat Intel Feeds
Start Utilizing an Automated Domain Management Technology Today
Phishing and fraud happen fast on the internet, and your brand can quickly come under attack. So, do you wait for that day or put in place a program that affords you advanced warning? And when that day inevitably comes when a site (or sites) needs to be taken down, what steps will you take? Are you going to try to do it manually or enlist a professional service? Hopefully this blog series helped to answer these questions for you. And as always, remember we’re here to help you every step of the way!
Learn more about Bolster
- Bolster Auto-Takedown solutions
- Bolster Domain Protection solutions
- Bolster Brand Protection solutions
- Bolster Phishing & Fraud Protection solutions
Request a demo & free trial: Free trial
To learn more about domain monitoring, read our whitepaper: Guide to Domain Monitoring and Remediation
***
Whac-a-mole™ is a registered trademark of Mattel, Inc.









