Bolster is excited to share a major landmark in our path to making the internet a safer place…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
The Click That Stole Holidays: Black Friday and Cyber Monday Scams Unmasked
The onset of Cyber Monday and Black Friday deals is something we all stay up for. Whether it’s discounted vacation travel packages, instructional offers to.
Exploring the Risks of IPFS in Phishing Attacks
Introduction The InterPlanetary File System (IPFS) is a cutting-edge technology designed to revolutionize how we store and share data across the internet. It offers a.

Phishing in Focus: Bolster's 2024 Mid-Year Phishing and Online Scam Update
With the unprecedented surge in phishing attacks sparked by AI, protect your business with data into key phishing and scam trends including election fraud, industry-targeting, and consumer interest scams.
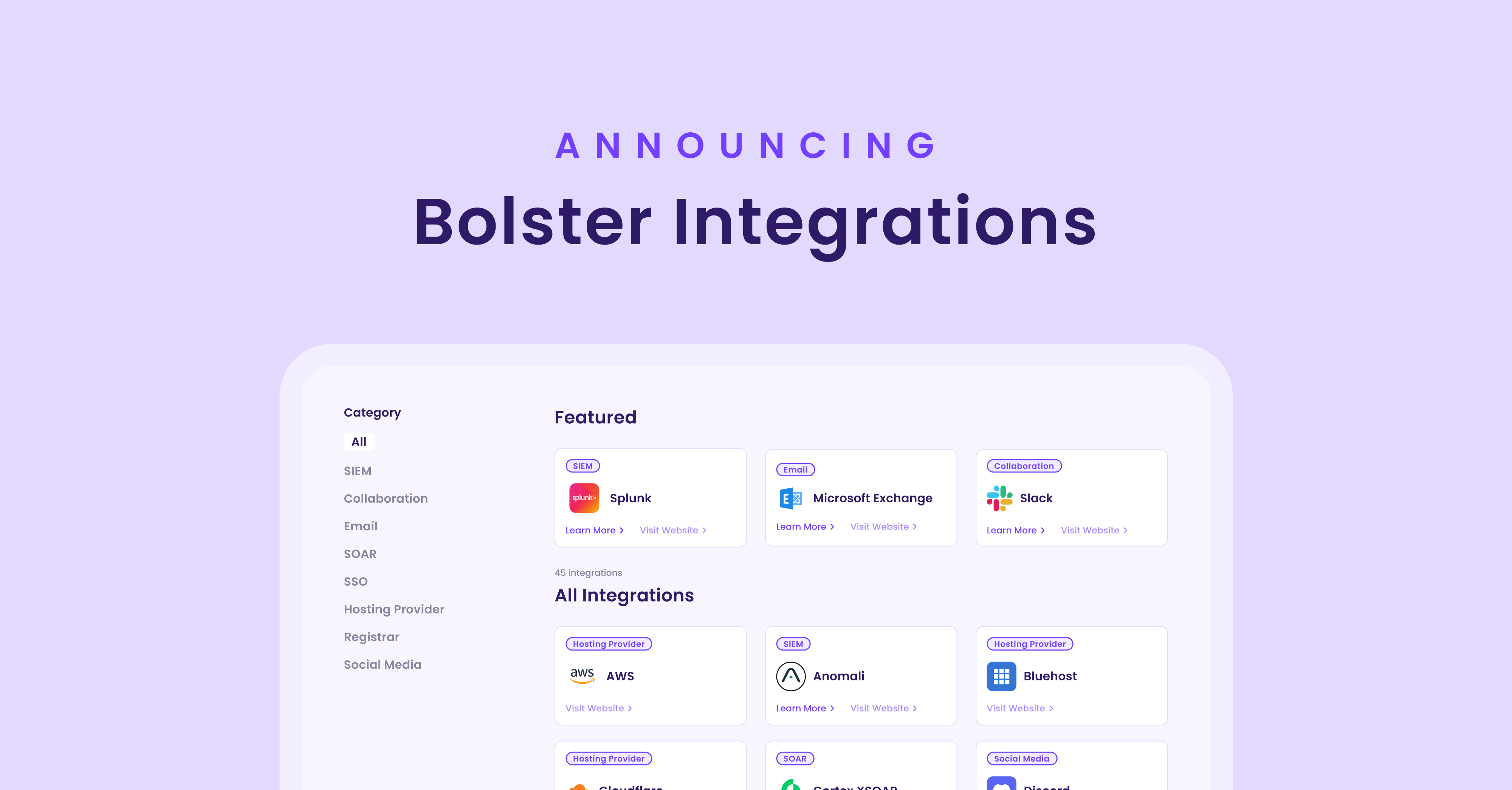
"Bolster Data Everywhere": Integrations to Protect Customers and Employees
Today we are introducing “Bolster Data Everywhere”, a rapidly expanding…
Introducing NEW Starter Plan from CheckPhish
Since launching an introductory version of our CheckPhish Typosquat Monitoring…
Introducing Managed Service Providers Partner Program, Bolster's Newest Product Offering to Combat Online Threats
We are thrilled to announce the launch of our new…
Proactive Defense Against BEC Attacks: How to Stay Ahead of the Scammers
Business Email Compromise (BEC) has become a significant threat to…
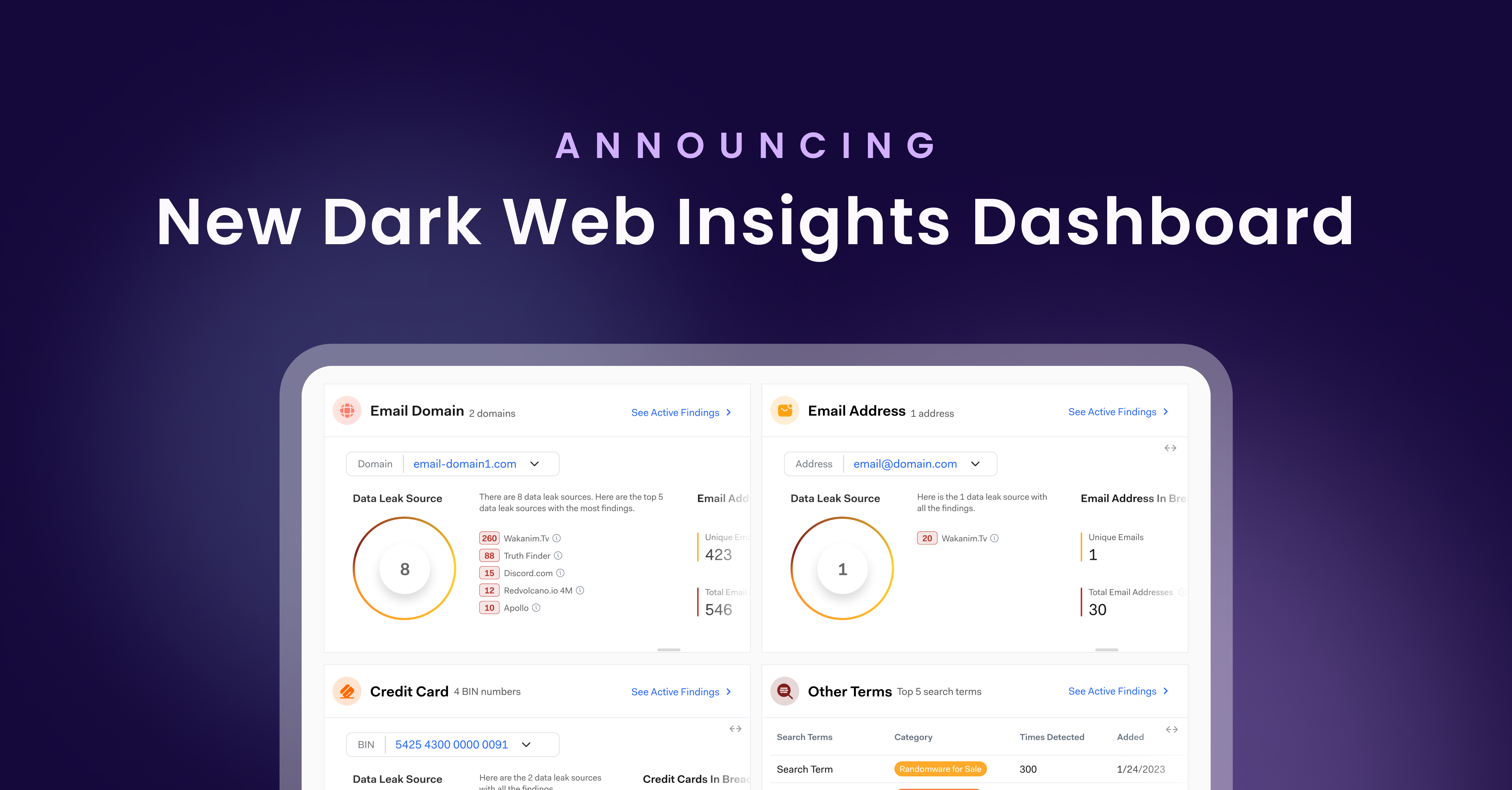
Discover the Bolster Dark Web Monitoring and Insights Dashboard: Fast-Track Visibility of Credential Threats
The dark web poses a complex and pervasive threat environment…
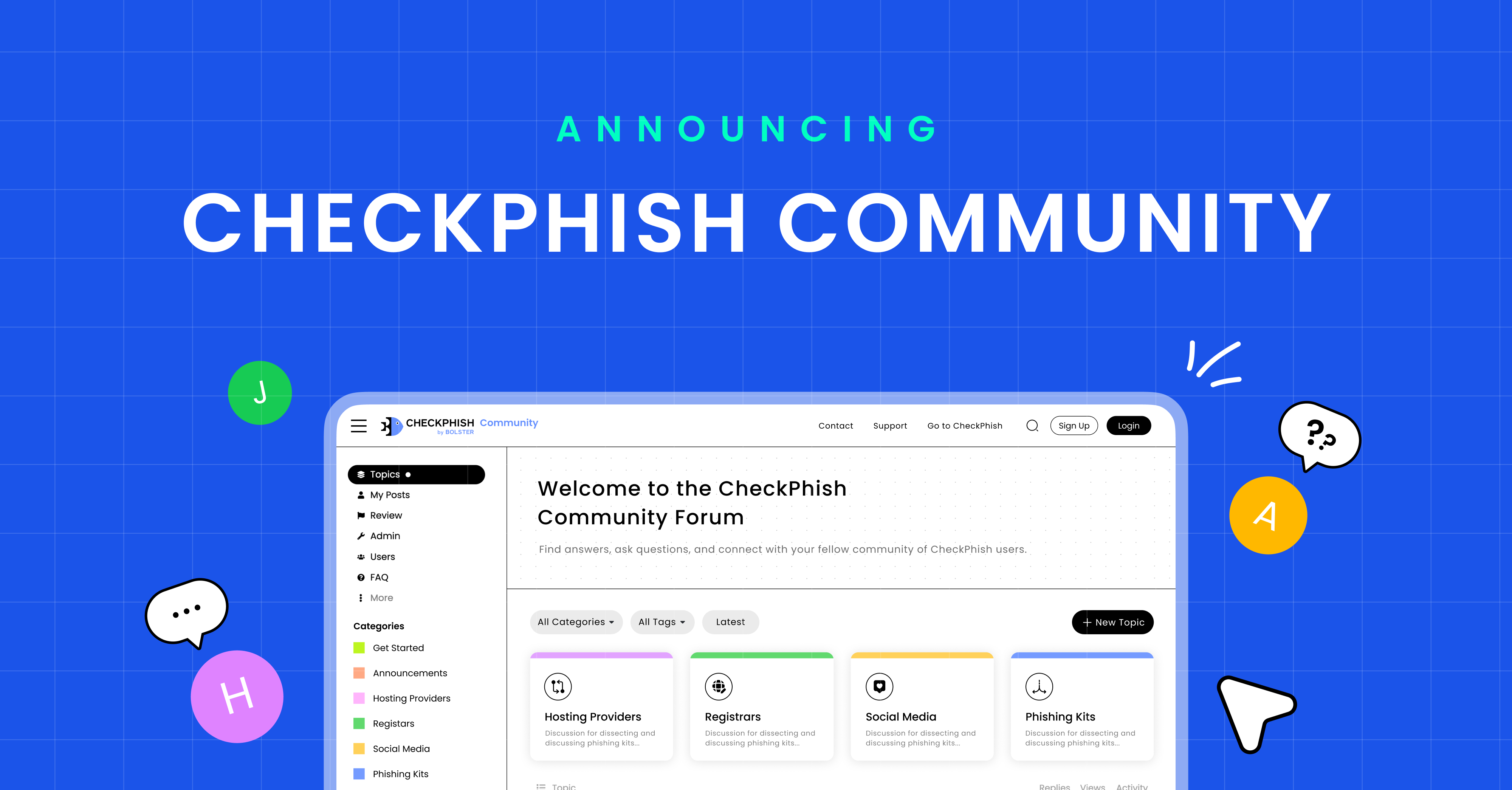
Announcing Bolster Community Forum
In the rapidly changing digital landscape, the cybersecurity community confronts…
Introducing Bolster’s Fully Customizable Table
Bolster, a leading provider of AI-powered phishing detection and response,…
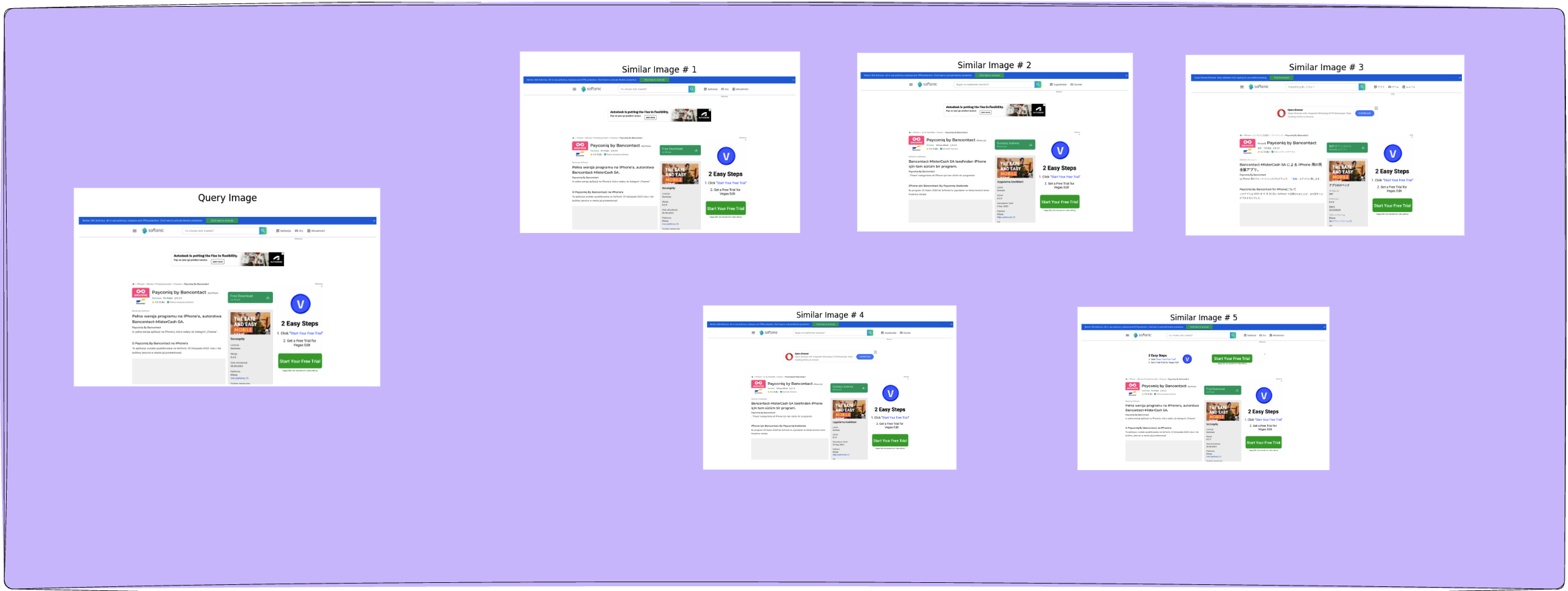
Beyond Hashing: The Future of Anti-Phishing is Image Similarity Search
Computer vision modules are a critical component in a cybersecurity…
A Visual Journey: Exploring the Redesigned Bolster Dashboard
One of the top challenges that security practitioners often…
Top 4 Features of a Dark Web Monitoring Tool
The term “dark web” often gives off an ominous…
The Power of Automated Domain Monitoring
Today, business owners around the world understand that digital…
Domain Risk Management - The Build vs. Buy Dilemma in 2023
Domain risks are growing increasingly aggressive, and detrimental to businesses…