Many threat actors are moving away from utilizing brand logos or impersonating phishing websites as their top phishing tactics. Their methods to steal information in mass quantities is constantly advancing, and they’re learning to operate discreetly to bypass typical AI detection systems.
India’s BFSI sector is a primary target for scammers due to its extensive customer base. The existing knowledge disparity makes this base especially susceptible.
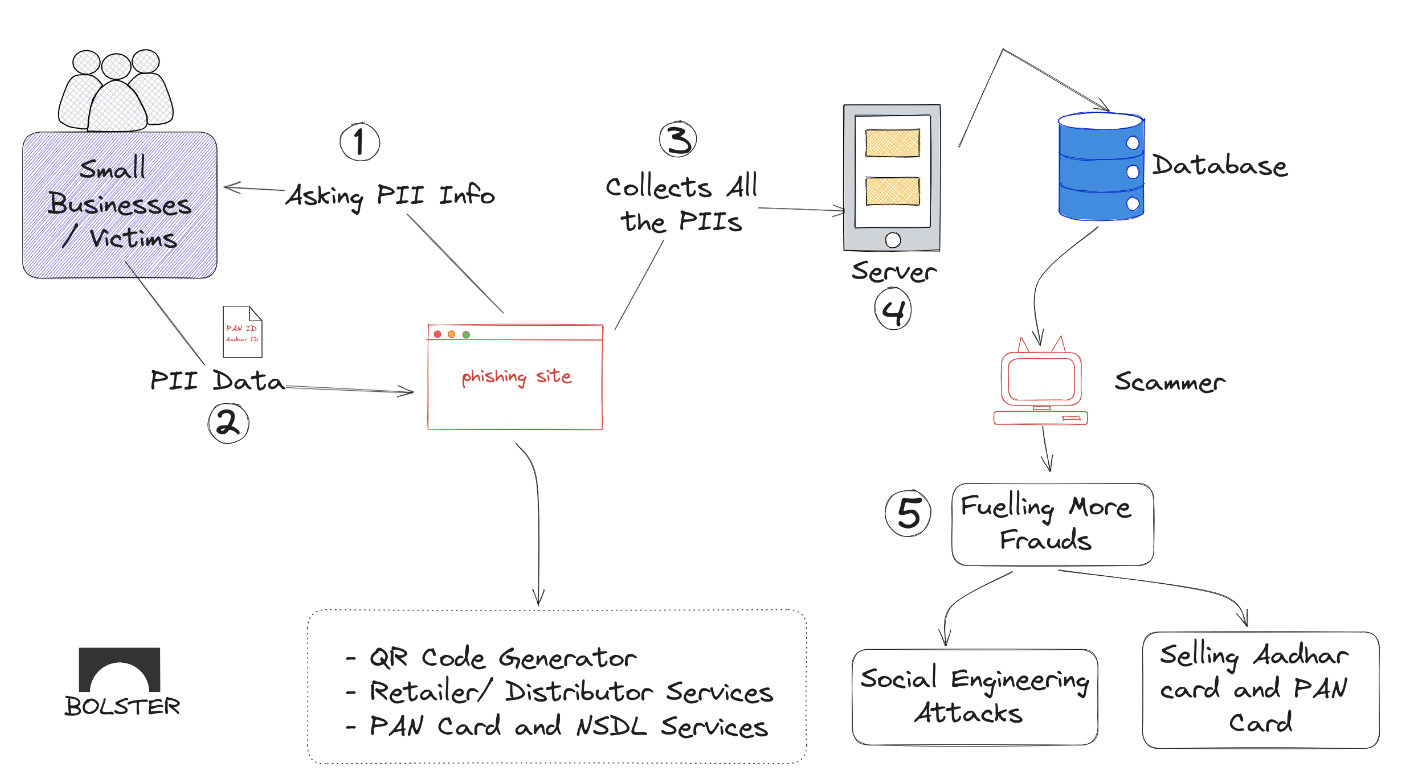
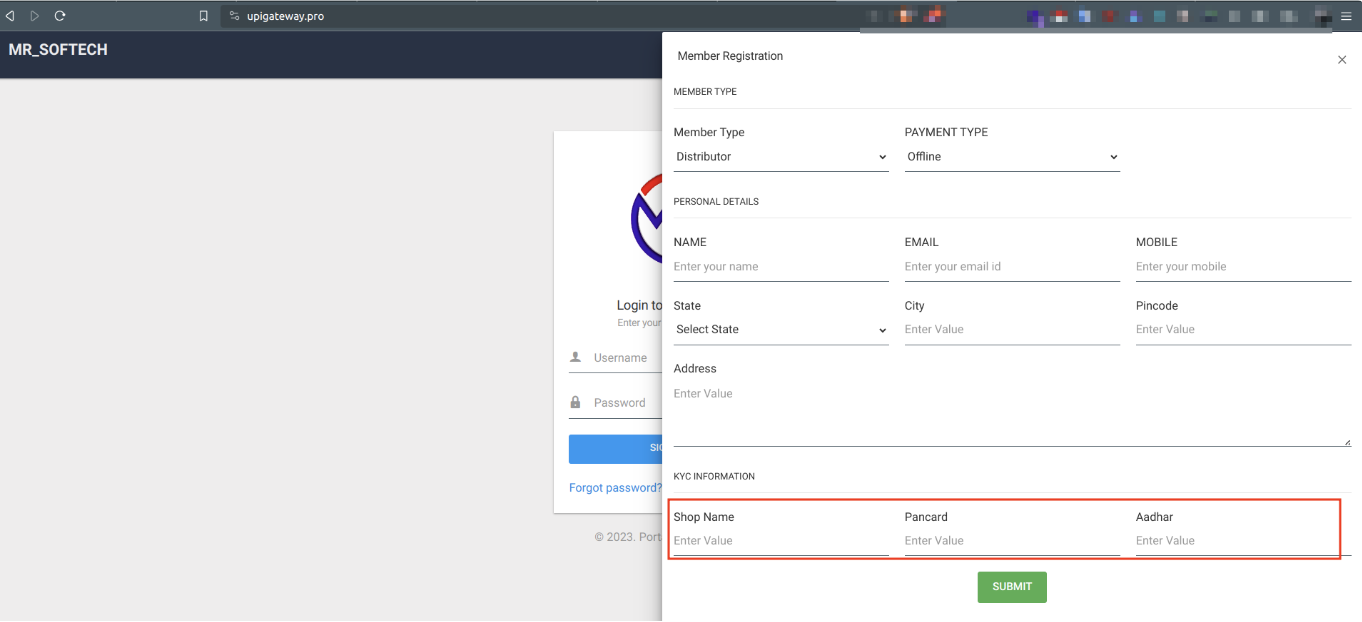
In a study, the Bolster Research team uncovered several phishing pages that appeared similar and offered UPI Gateway and recharge services. These pages also pitched Retailer and Dealership opportunities to Indian clientele. However, the disguised process of account registration included the illicit acquisition of personal details, including email, phone number, PAN, and Aadhaar Card numbers. This data can pave the way for a spectrum of fraudulent undertakings.
In recent reports, several scammers have been caught illicitly acquiring and selling the PAN & Aadhaar cards of numerous users. It’s plausible to believe that this exposed phishing campaign could be one method they utilized to accomplish this.
Under the Radar Phishing Campaign
In the recent wave pf cyber scams, malicious actors have set their sights on UPI payment channels, especially after NPCI unveiled the UPI Plug-in service in July 2022.
This innovation empowered banks to seamlessly connect their apps with merchant interfaces, eliminating the need for intermediary vendors such as GooglePay and PhonePe.
Historically, we’ve seen scammers masquerade by designing fake sites that impersonate logos and brand names from legitimate companies. While these counterfeit sites were identifiable using AI tools that analysed logo patterns, text resemblances, or utilised computer vision hashing, the current widespread campaign is showing a shift in tactics.
Instead of mimicking recognised brands, these threat actors now act directly as businesses, persuading consumers to disclose personal identifiers: Aadhaar Card Numbers (a unique identifier for Indians), PAN Numbers, Business Names, Email Addresses, and Phone Numbers. Once in possession of this information, these fraudsters can launch a series of manipulative social engineering attacks on each individual.
A Deeper Dive into Phishing Websites
The Bolster research team discovered some revealing trends in phishing websites that show evolving scam techniques.
Key findings
We found the following trends in our research:
-
These scams predominantly target small businesses and local vendors who are keen on transitioning to digital transactions but are unfamiliar with payment gateway services.
-
At the time of writing this report, there were over 150 active phishing websites, all using one of three templates, offering similar services.
-
The majority of these phishing websites operate on a subscription model and steals PII information during registration process. Since they’re generated from the same template, their pricing structures are often similar.
-
Some of these sites provide services like QR code generators for digital transactions, requiring the payee’s UPI ID.
-
During the analysis we have discovered a few phishing websites associated with old scam campaigns similar to Aadhaar printing scam and UPI reward scam.
-
We identified a phishing-kit that was employed to craft a specific type of phishing website during our investigation.
Modus operandi
In this campaign, scammers are employing more sophisticated and genuine-looking websites to t users into divulging their personal information, despite the tactic not being entirely new.
Types of Phishing Websites
Our AI-driven brand protection product, Checkphish, has unearthed over 400 such phishing sites (most of them were still live while writing this blog) that cleverly disguise themselves as non-registered enterprises, baiting unsuspecting individuals into revealing confidential details.
During our investigation, we analyzed 3 primary phishing kits hosted across various domains & TLDs, with keywords such as “upigateway”, “pgservice”, “recharge”, “digitalupi“ and “onlineupi”. Even some of the sites used “bank” in their domain to make it more trust worthy to victims.
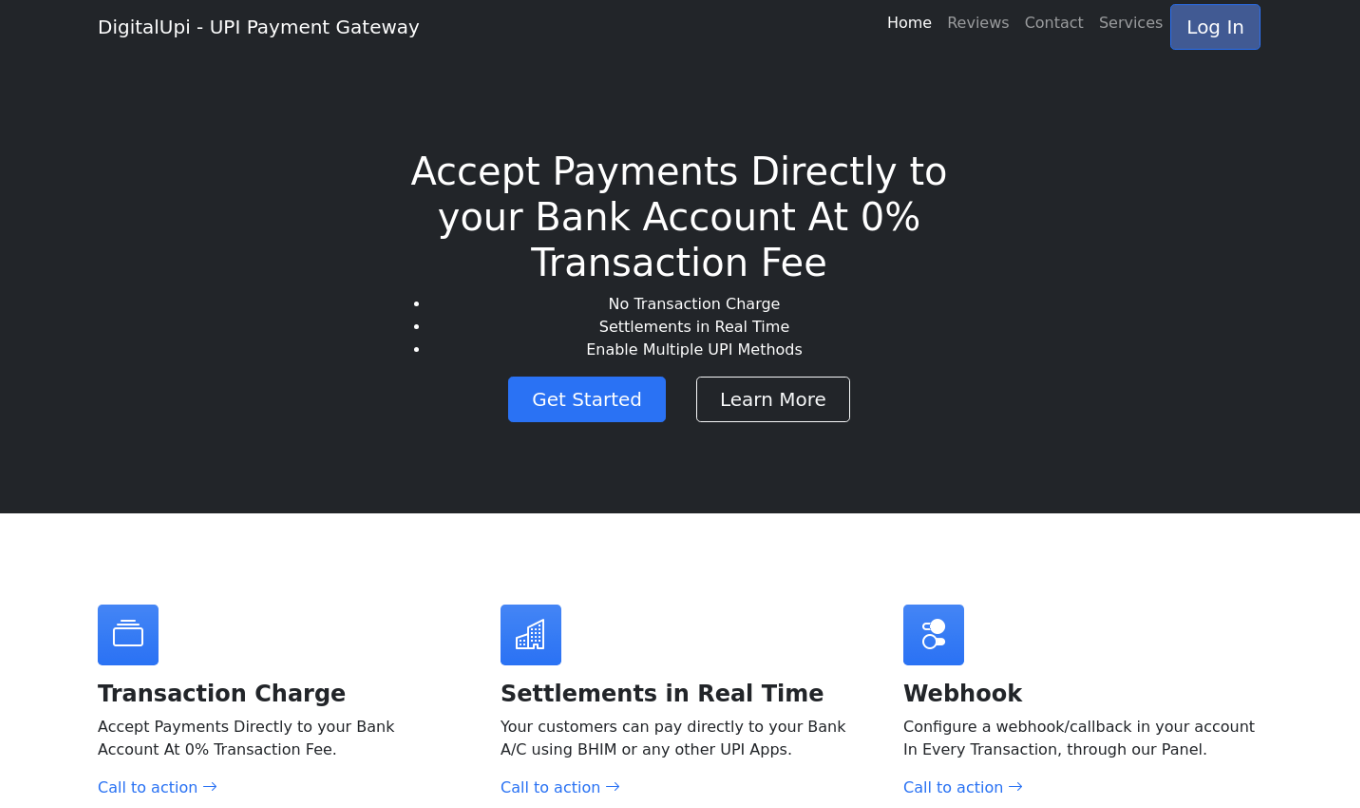
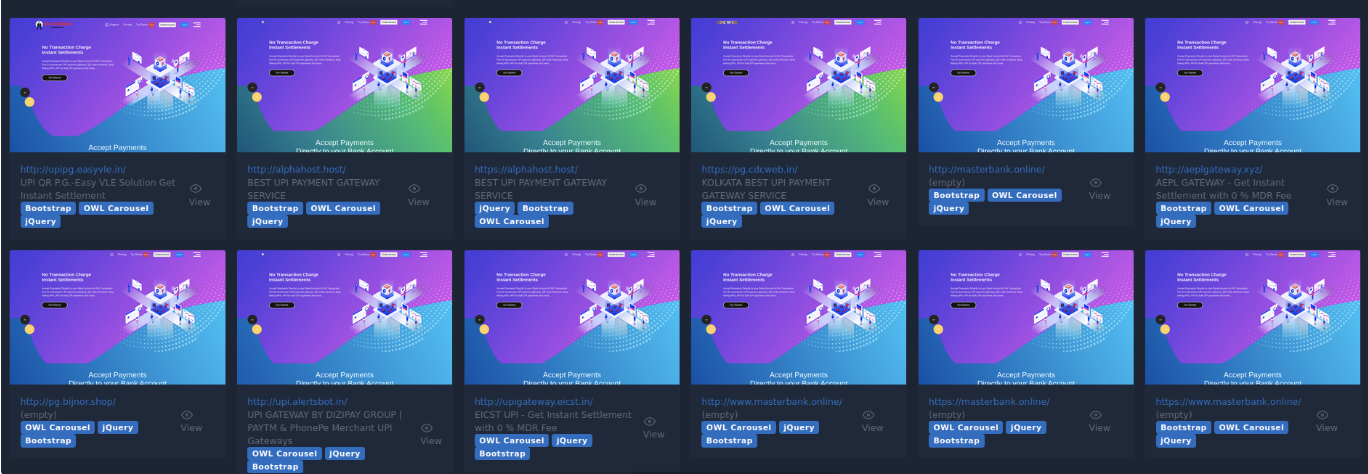
Type 1: Impersonating UPI payment gateway
In this version, the site claims to offer services such as webhook integration, UPI, and bank transactions using a subscription-based model.
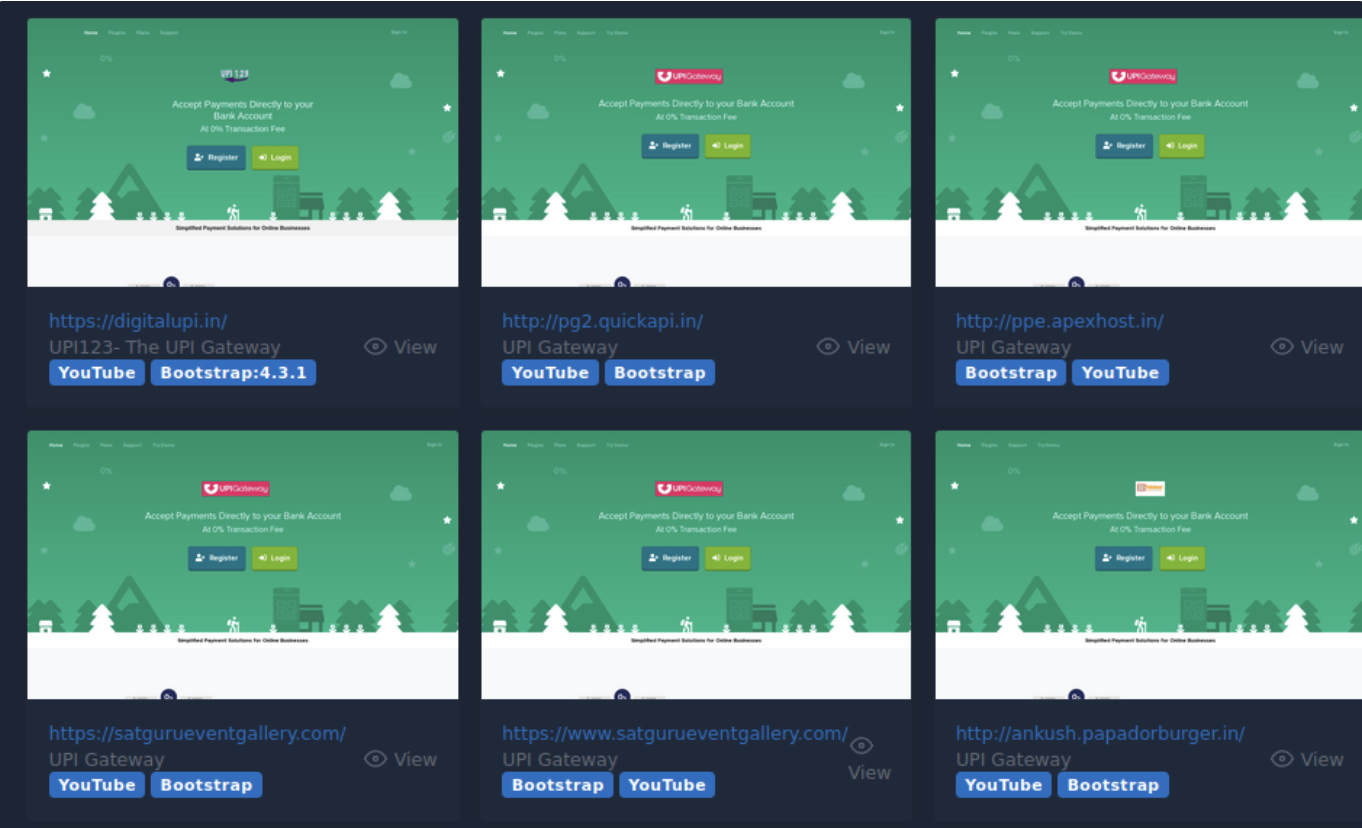
Type 2: Impersonates UPI123
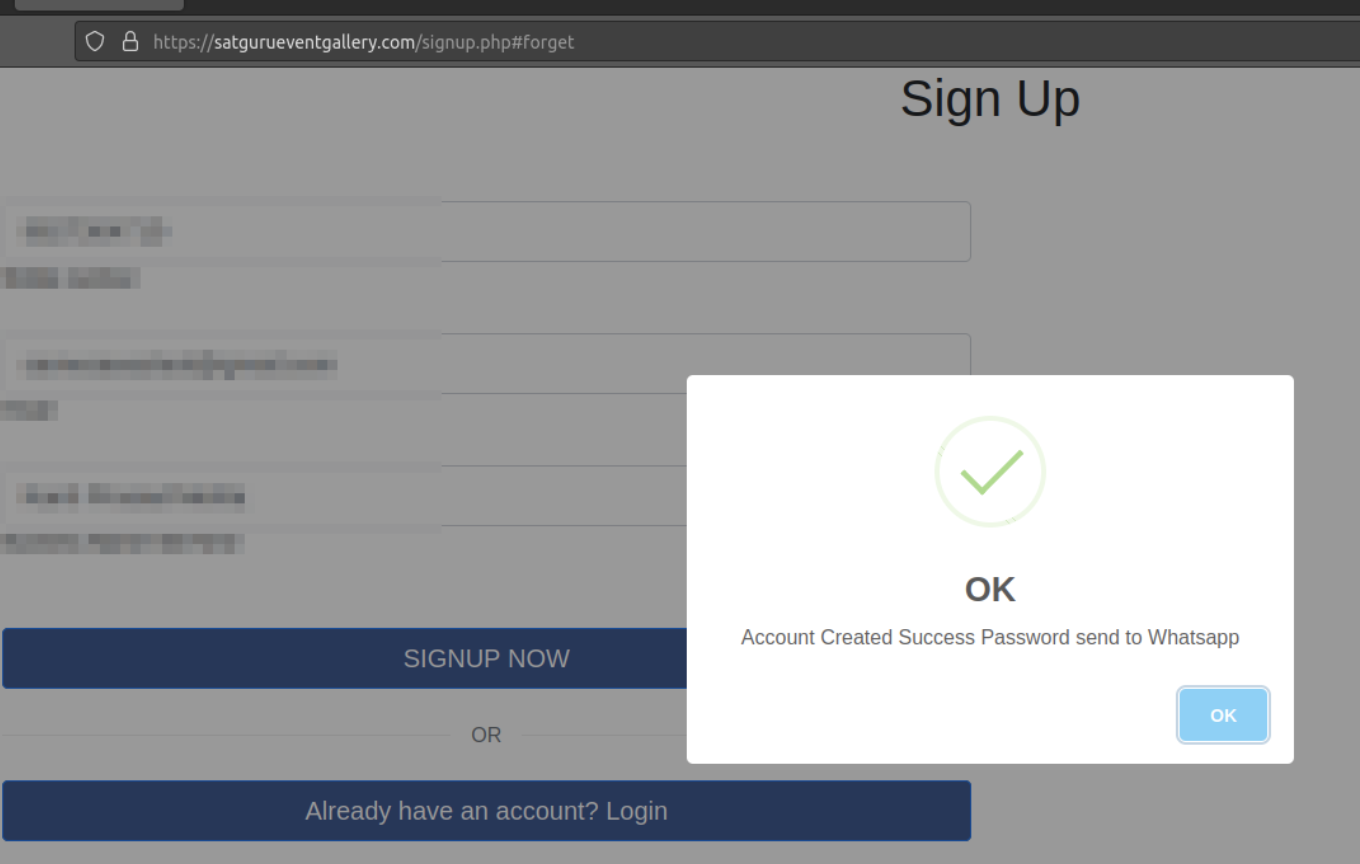
This type of sites initially does not ask for the PIIs like other phishing site, once you create account it will send password via WhatsApp on the registered number and then ask for a payment of Rs. 29 or Rs. 199 based on subscription model.
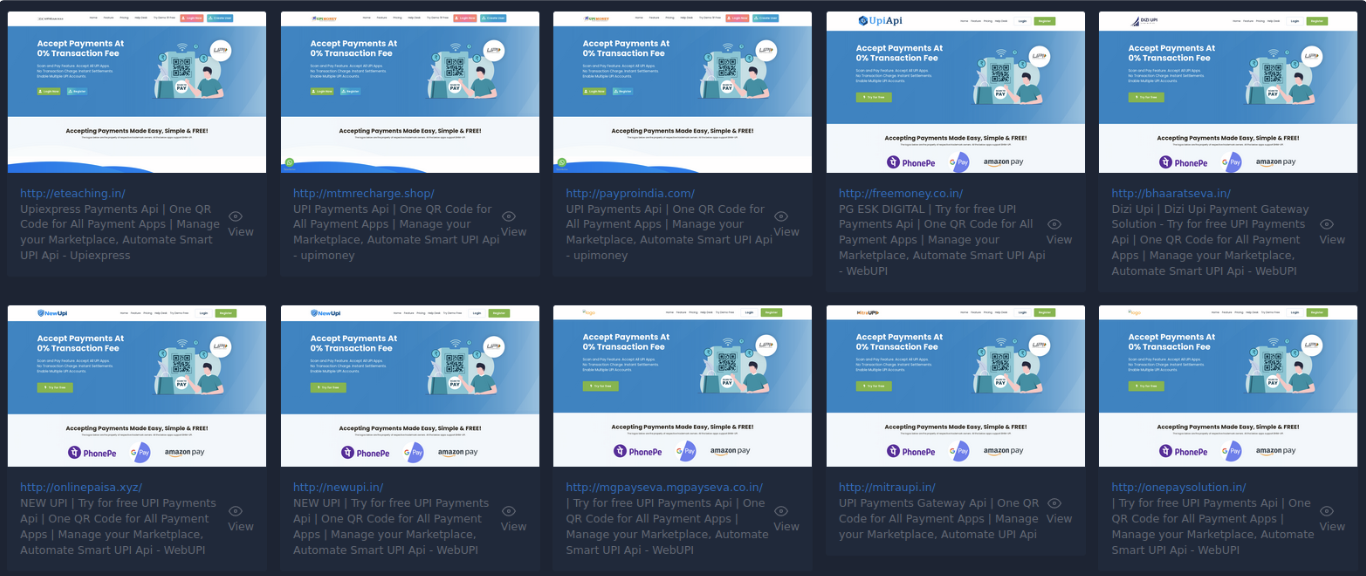
Type 3: Mentions trusted brands to build trust
These types of sites used the brand name of popular (which is common among fraudsters) UPI wallet and gateway vendors to build trust among the victim and lure them to create account into the phishing portal.

Stealing of PIIs
All types of phishing sites collect PII data in various form.
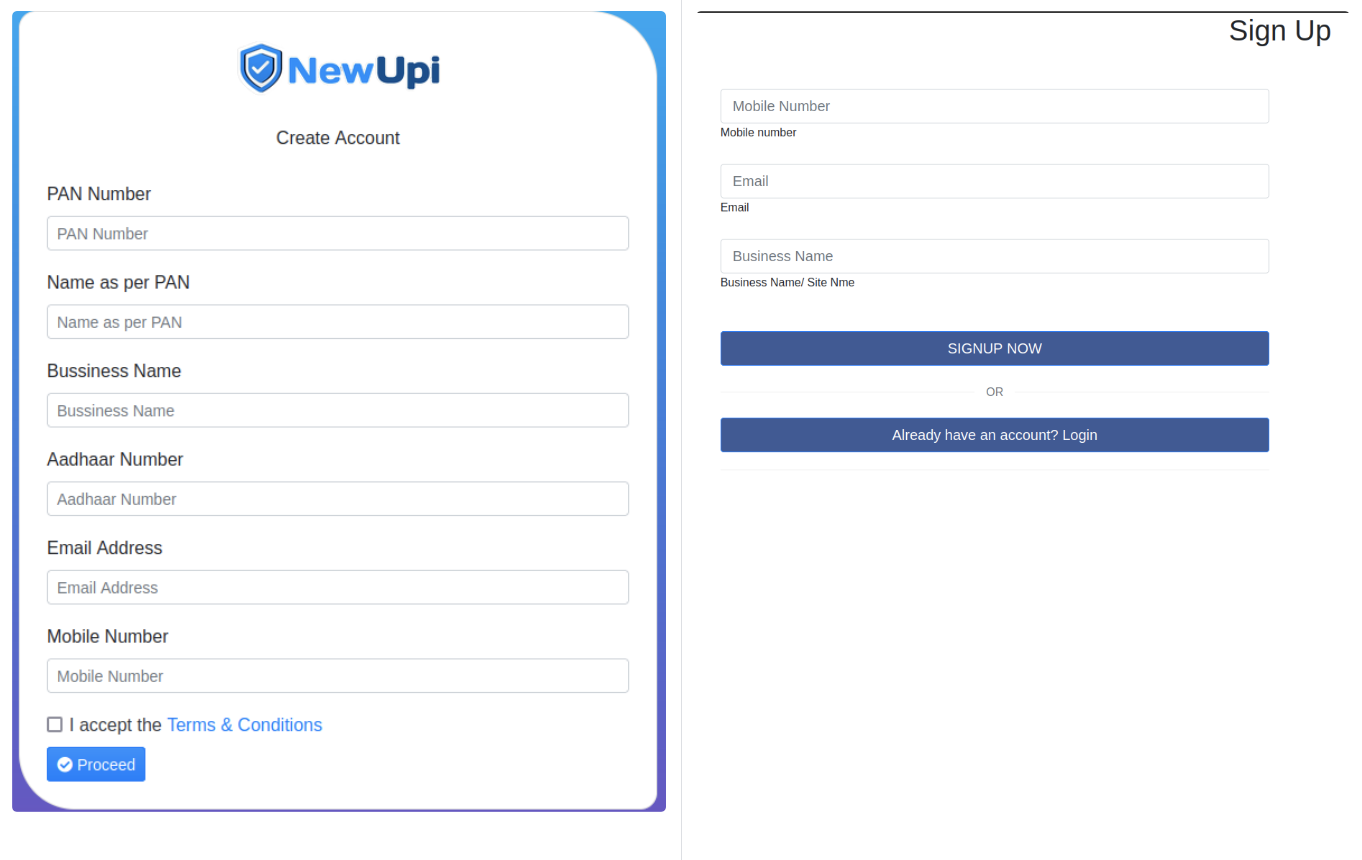
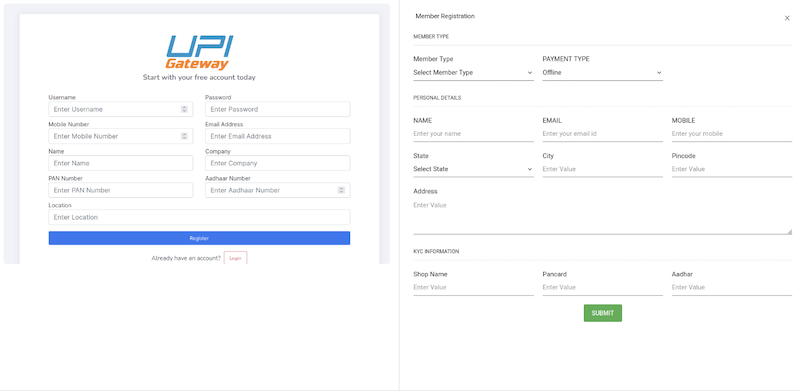
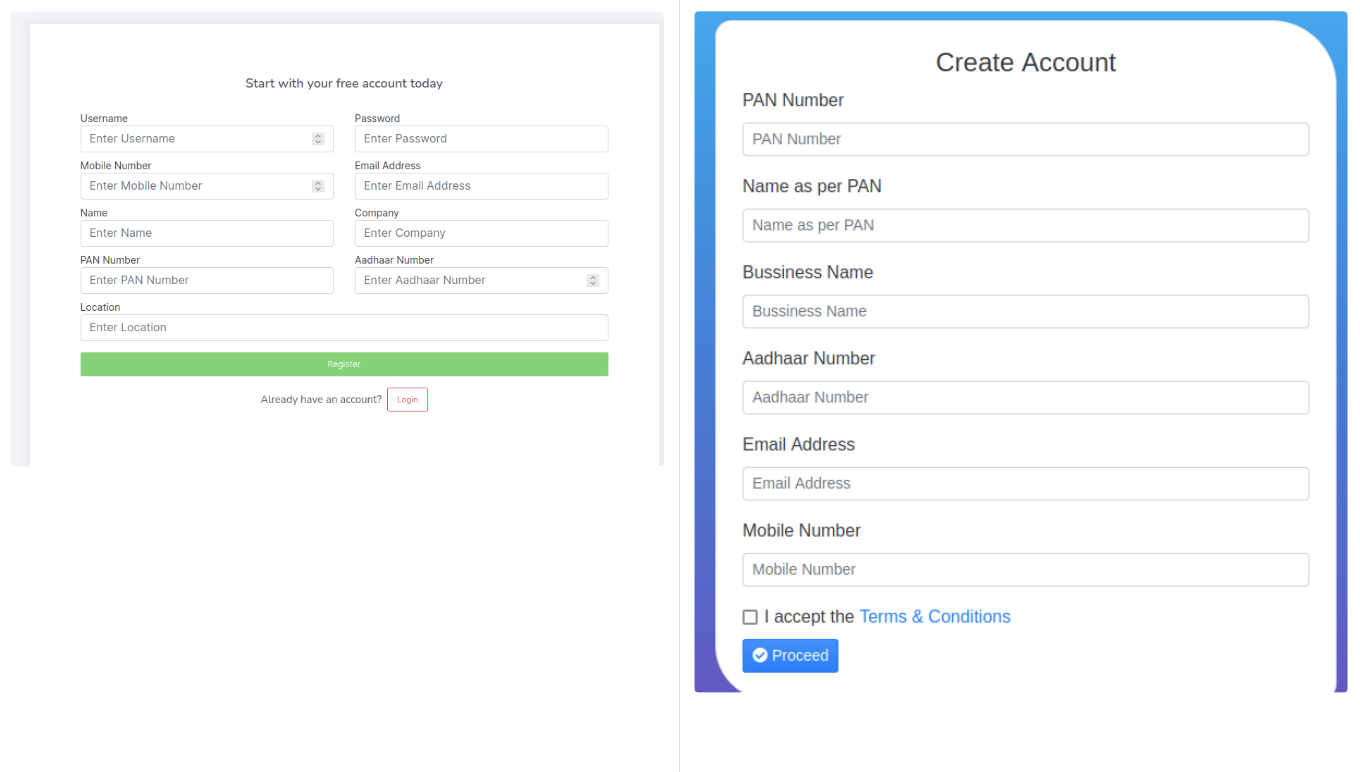
Discovering the Phishing-Kit
While analyzing a list of similar phishing websites, we fortuitously discovered a newly registered domain in preparation. We were able to download the phishing kit from it.
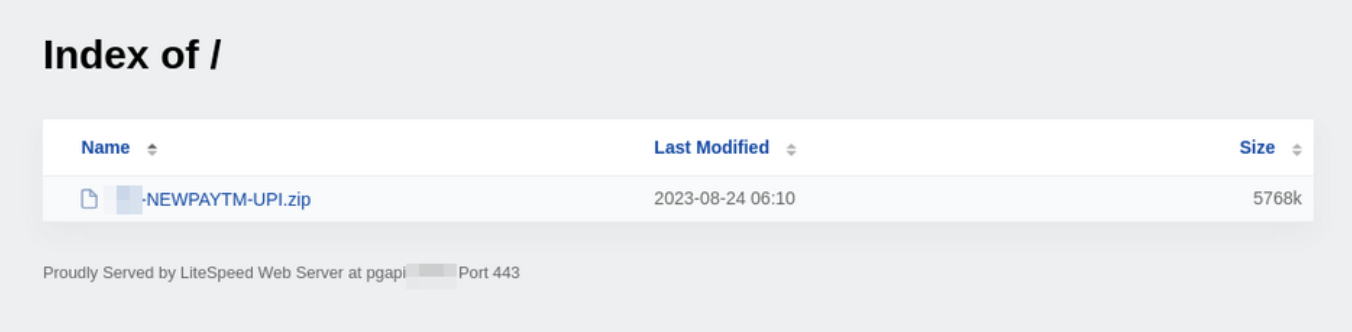
Upon examining the phishing kit, we discovered that it can generate sites similar to those shown in the following screenshot:
How to Safeguard Your Assets Against New Phishing Websites Techniques
As phishing techniques are evolving to try and outsmart our industry anti-phishing techniques, it’s important to continue to implement strategies to stay ahead of threats:
- Avoid sharing your Aadhaar number (both 12-digit and 16-digit virtual versions) and PAN number with unfamiliar or unauthorised parties.
- When providing a photocopy of your Aadhaar & PAN, always specify the purpose and date on the copy, and ensure it’s self-attested.
- Secure your Aadhaar by visiting https://myaadhaar.uidai.gov.in/lock-unlock-aadhaar to first generate a 16-digit virtual ID and then lock/unlock your Aadhaar details.
- Ensure your mobile number or email ID is registered with UIDAI. This registration will notify you if someone attempts to use your Aadhaar for verification.
- For updates or changes to personal details, such as name, address, DOB, gender, phone, or email, only approach an official Aadhaar & PAN enrolment center.
Using Bolster to Protect Your Business
The rapid transition to digital transactions, while offering numerous benefits, has also presented opportunities for cybercriminals to exploit the unsuspecting.
Small businesses and local vendors, eager to embrace digital payments, become prime targets due to their limited familiarity with secure payment systems. As these scams evolve and employ techniques reminiscent of past frauds, like the Aadhar printing and UPI reward scams, it becomes even more imperative for businesses and individuals alike to stay informed and vigilant.
Our findings also highlight the need for continuous monitoring and research in the realm of phishing site hunting to preemptively identify and combat such threats.
Bolster’s anti-phishing and domain monitoring technology protect your business from evolving phishing threats. With continuous scanning technology that quickly identifies threats and misuses of your branded assets, you can trust Bolster will protect your business.
See Bolster in action when you request a demo.