Phishing continues to be one of the most popular ways for attackers to obtain unauthorized access to sensitive data in the digital era, where cybersecurity threats are getting more complex. A more sophisticated type of phishing is called Man-in-the-Middle phishing (MitM), which differs from typical phishing techniques in that it involves tricking users into entering their credentials on fake websites.
Evilginx is a framework that elevates phishing to a new level and is one of the most noteworthy tools in this field. This comprehensive guide will explore how MitM phishing works, dive into the specifics of Evilginx, and provide insights into how to protect yourself from such attacks.
What is Man-in-the-Middle Phishing?
Man-in-the-Middle (MitM) phishing is a sophisticated active attack technique where an attacker intercepts the communication between a user and a legitimate service to steal sensitive information.
Unlike traditional phishing, where the victim is tricked into entering their credentials on a fake login page, MitM phishing involves an intermediary that captures the data exchanged between the victim and the real service. This allows attackers to bypass advanced security measures, including two-factor authentication (2FA).

How Man-in-the-Middle Phishing Differs from Traditional Phishing?
To understand the significance of MitM phishing, it’s essential to compare it with traditional phishing methods:
1. Traditional Phishing:
- Mechanism: In traditional phishing, attackers create a fake website that mimics a legitimate service (e.g., a bank or email provider). They trick victims into entering their credentials on this fake site.
- Limitations: Traditional phishing is limited by the ability to capture only what the user directly inputs. If the target has 2FA enabled, the attacker still needs the second authentication factor to gain full access.
2. MitM Phishing:
- Mechanism: MitM phishing uses an intermediary server to intercept and relay communication between the victim and the legitimate service. The attacker captures not only the user’s credentials but also authentication tokens and session cookies.
- Advantages: By capturing session tokens and cookies, attackers can bypass 2FA and gain persistent access to the victim’s account without needing the second factor.
How Evilginx Operates?
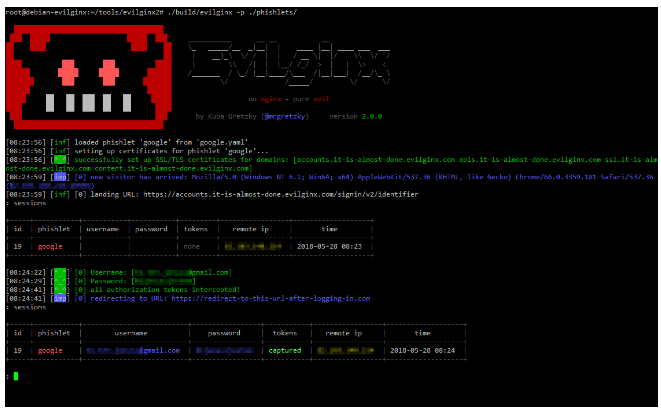
Evilginx is a powerful tool specifically designed for MitM phishing attacks. It works by creating a proxy between the victim and the real service, enabling attackers to capture authentication tokens and session cookies. Here’s a detailed breakdown of how Evilginx functions:
1. Phishing Attack Execution
Target Engagement: The attacker needs to lure the victim to the phishing site. This can be done through various methods, including phishing emails, social engineering, or malicious links shared via social media.
Learn more about social engineering and phishing
User Interaction: When the victim navigates to the phishing site and attempts to log in, Evilginx proxies the request to the actual service. The victim enters their username and password on the phishing page, which Evilginx forwards to the legitimate service.

2. Data Capture
Credential Harvesting: As the victim submits their credentials, Evilginx captures and logs the username and password.
Token Interception: More critically, Evilginx intercepts and captures authentication tokens and session cookies that are sent by the legitimate service. These tokens are essential for maintaining a logged-in session and can be used to bypass 2FA protections.
3. Session Hijacking
Access Gained: Using the captured session tokens and cookies, the attacker can access the victim’s account without needing the second factor of authentication. This allows them to perform any actions that the victim could, effectively taking over their account.
Persistence: The attacker can maintain access as long as the session remains valid. This can potentially give them extended periods of unauthorized access if the victim does not detect and mitigate the breach.
The Impact of Evilginx
Evilginx represents a significant leap in phishing sophistication due to its ability to bypass advanced security mechanisms.
Here’s why it’s so impactful:
Bypassing Two-Factor Authentication: Many organizations and individuals use 2FA to enhance security. However, Evilginx can capture the authentication tokens used by 2FA systems, allowing attackers to bypass this layer of security. This is particularly concerning for high-value targets like financial institutions or email accounts with sensitive information.

Real-Time Data Capture: Evilginx operates in real-time, capturing credentials and tokens as they are transmitted. This dynamic approach makes it harder for users to detect that their information is being intercepted, as the phishing site can closely mimic the legitimate service’s appearance.
Advanced Evasion Techniques: Evilginx’s use of a proxy server means that the phishing site doesn’t have to store credentials or tokens directly. Instead, it relays information to the legitimate service, reducing the risk of detection by traditional security measures that might look for phishing sites hosting stolen data.
How to Protect Yourself from Evilginx and MitM Phishing
While Evilginx and similar tools pose a significant threat, there are several measures you can take to protect yourself:
Be Cautious of Phishing Links: Always verify the URL before entering any credentials. Ensure the site uses HTTPS and look out for any discrepancies in the domain name. Hovering over links in emails to check their destination can also help identify malicious links.
Use Strong, Unique Passwords: Employ a password manager to generate and store strong, unique passwords for each of your accounts. This reduces the risk of credential reuse, making it harder for attackers to exploit compromised credentials.
Implement Robust Multi-Factor Authentication: Use multi-factor authentication (MFA) methods that don’t rely solely on SMS or email, as these can be intercepted. Consider using hardware-based tokens (like YubiKeys) or authentication apps (like Google Authenticator) that provide a higher level of security.
Monitor Account Activity: Regularly review your account activity for any unusual actions. Many services offer alerts for login attempts from unfamiliar devices or locations. Enabling these notifications can help you quickly detect and respond to unauthorized access.
Keep Software Up-to-Date: Ensure your operating system, browser, and security software are up-to-date. Software updates often include patches for known vulnerabilities that could be exploited by attackers.
Employ Network Security Measures: Using network security tools such as VPNs and firewall configurations can help protect against some phishing attacks. These tools add layers of security by masking your IP address and blocking suspicious traffic.
Conclusion
Evilginx uses Man-in-the-Middle tactics to depict a sophisticated and dangerous advancement in phishing assaults. You may protect yourself from these advanced threats by learning how Evilginx works and putting in place strong security measures.
Vigilance, education, and proactive security procedures are critical for protecting your digital presence. In today’s digital landscape, staying up to date on emerging risks and always upgrading your security posture are critical.