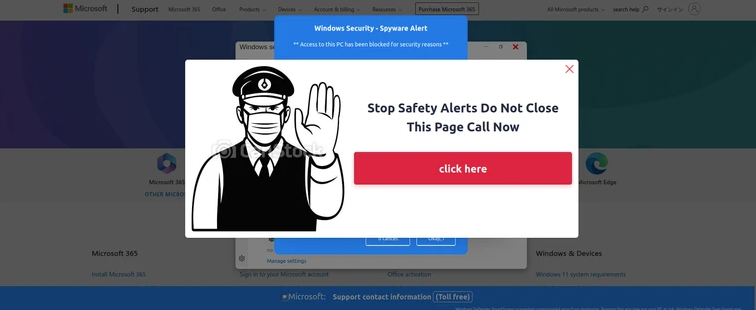
The Tech Support Scam consistently remains in the spotlight due to the substantial fraud involved, where victims are tricked into surrendering vast sums of money. To fuel such scam campaign threat actors/ scammers create various type of phishing websites based off of tech support phishing kits meant for impersonating tech support for big brands like Microsoft, Apple and famous brands.
A recent study by Bolster Research Labs has revealed over 300 phishing sites specifically crafted to intimidate victims and prompt them to contact the scammers who are impersonating as the tech support team, to further entice them into parting with their money. Majority of the phishing site was targeted to Microsoft and Apple Supports and was using similar phishing-kit.
Exploring Call Back Scams
This scam begins with a fake tech support phone number given out on phishing websites. These websites scare people and an AI-recorded voice intensifies the urgency by repeatedly urging them to call the provided tech support number.
Subsequently, the scammer on the phone social engineers the person into paying money to renew security services or remove a fake virus that appeared while they were on the bad website.
Such type of scam is termed as “Call Back Scam”; unlike traditional phishing, callback phishing doesn’t include a malicious link in the email. Instead, it features a prominent phone number, urging the recipient to call for an urgent matter.

Analysis of Malicious Sites
CheckPhish.ai has classified several similar looking pages are being hosted in various ways, but the key characteristic of the websites promoting call back scams include:
- While browsing these websites and then hovering over any part of the webpage it opens the webpage in full screen mode and blocks all kind of keyboard input or mouse clicking expect the
Esckey from the keyword, which can only option to get out of the full screen mode. - In the background a voice will play asking to contact the fake support on the mentioned support number on the webpage along with an alarm sound making the situation more intensifying.
Distinct features of the tech support phishing kits
CheckPhish.ai has discovered several websites with similar appearances, hosted in various manners.
- These types of websites have a unique characteristic in that, when a user hovers over or clicks any section of the webpage, it automatically switches to full-screen mode, disabling all keyboard and mouse inputs except for the
Esckey. The only way to exit the full-screen mode is by pressing the Esc key. Moreover, while in this mode, a pre-recorded message plays in the background, compelling the user to call a fake support number displayed on the webpage. To add to the urgency, an alarm also sounds in the background. - Furthermore, these phishing sites have the ability to retrieve the victim’s geographical location and incorporate it into their display, intensifying the sense of fear and urgency for the victim.
- Most of these discovered websites were hosted on various freemium SaaS platforms (most of them using Digital Ocean, Amazon, and Azure hosting services) including Cloudflare’s pages.dev & r2.dev, varcel.app and bunny.net, etc.
Reasons behind the abuse of SaaS platforms
In our last couple of blogs, we have identified that threat actors are inclined towards creating various ‘freemium’ SaaS (Software as a Service) platforms to host phishing and scam sites. The following are the reasons:
- Simple Deployment: Many services that are prone to abuse offer a straightforward setup for launching numerous phishing websites.
- Cost-Effective: The majority of these services are available at no cost, providing high returns for malicious actors with minimal or no investment.
- Evasion Capabilities: These services have the ability to circumvent endpoint detection systems, as they are originally designed for legitimate development purposes.
Hunting for Malicious Sites in the Wild
In our analysis, we found that the majority of these phishing sites utilized the same phishing kit. This similarity simplifies the process of tracking down related sites by identifying unique filenames, site titles, , specific text renderings or DOM texts.
Filename used in the phishing-kit:
ai2.mp3[unable to retrived]nOxp-sett.png[setting icon image]_Fm7-alert.mp3[Backgroud voice]f24f24.png[ this is the background image]msmm.png[microsoft windows favicon]

Site titles to identify more similar sites:
Computer Error 2V7HG0TVBWindows Help Support Assistance Er#0Y0dv14007
The investigation reveals that the phishing websites have been widely distributed, targeting customers worldwide, ranging from those who speak English to speakers of German, Japanese, and Chinese.

Additional Findings
While conducting an analysis of tech support phishing pages classified by CheckPhish, we coincidentally came across an additional website designed to replicate the Apple Tech Support Page, exhibiting a congruent modus operandi.


Be Wary of Opening Suspicious Links
Considering the nature of this scam, it’s crucial to keep in mind the following key points to steer clear of similar scams in the future:
- Don’t trust unsolicited calls: Do not trust unsolicited phone calls claiming to be from tech support, especially if they ask for remote access to your computer.
- Don’t click on suspicious links: Avoid clicking on links or downloading attachments from unknown or suspicious sources.
- Don’t give out personal information: Never share personal or financial information with anyone claiming to be from tech support unless you are absolutely certain of their legitimacy.
- Don’t engage with pop-up messages: Do not interact with pop-up messages claiming your computer is infected or in need of immediate support. Close such windows and ignore them.
- Don’t rush decisions: Scammers often pressure victims to make quick decisions. Take your time to verify the legitimacy of the tech support request.
- Don’t make payments to unknown sources: Never make payments to individuals or entities that cannot be verified as legitimate tech support services.
- Don’t rely solely on caller ID: Scammers can spoof caller ID information to appear as if they are calling from a legitimate source.
- Don’t download remote access software: Do not download remote access software suggested by unsolicited callers or from unverified sources.
- Don’t assume familiarity: Just because a website or caller mentions a well-known brand like Microsoft or Apple doesn’t guarantee their legitimacy. Always verify independently.
- Don’t hesitate to disconnect: If you suspect you are dealing with a scam, don’t hesitate to disconnect the call, close the browser, or shut down your computer to prevent further access by the scammers.
Conclusion
This blog aims to provide a comprehensive understanding of threat actors’ capabilities and their methods of scamming individuals. It highlights the evolving nature of scam campaigns, underscoring the importance of cautious behavior. It is crucial to exercise vigilance while clicking links or divulging personal information.
Appendix
Sample Phishing Sites from Phishing_kit_1:
hxxp[://]befress[.]azurewebsites[.]net/win08shdmeer0887/index[.]html
hxxp[://]helpift[.]azurewebsites[.]net/
hxxps[://]preservesupport[.]azurewebsites[.]net/
hxxp[://]subjecthelp[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]bondsstrongs[.]azurewebsites[.]net/
hxxp[://]seahorse-app-7dpsm[.]ondigitalocean[.]app/
hxxp[://]superlative-muffin-569c7e[.]netlify[.]app/
hxxp[://]alwaysasise[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]lookoyt[.]azurewebsites[.]net/
hxxp[://]com-request-review[.]info/
hxxps[://]enableleass[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxps[://]rescuease[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]main[.]d2l63hpp7rt89s[.]amplifyapp[.]com/
hxxp[://]dailysupports[.]azurewebsites[.]net/
hxxp[://]gyrosupport[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxps[://]gyrosupport[.]azurewebsites[.]net/
hxxp[://]greatsupport[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]learnov[.]azurewebsites[.]net/
hxxp[://]main[.]d26x9n1qx3pjl7[.]amplifyapp[.]com/
hxxp[://]lookoyt[.]azurewebsites[.]net/win08shdmeer0887/index[.]html
hxxps[://]dailysupports[.]azurewebsites[.]net/
hxxp[://]alwaysasise[.]azurewebsites[.]net/win08shdmeer0887/index[.]html
hxxp[://]hyperisegv[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]growthvine[.]azurewebsites[.]net/
hxxps[://]sirenexus[.]azurewebsites[.]net/
hxxp[://]main[.]d3cr39fgetfmr3[.]amplifyapp[.]com/
hxxps[://]afganjalebii[.]pages[.]dev/
hxxp[://]hjudtap[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]enableleass[.]azurewebsites[.]net/
hxxp[://]main[.]d3an5px9346clo[.]amplifyapp[.]com/
hxxps[://]highelp[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]bixso[.]pages[.]dev/
hxxp[://]ondwqiehgwqgbxsaudiwqu[.]s3[.]amazonaws[.]com/newthenPicture/0784[.]html
hxxps[://]supportlove[.]azurewebsites[.]net/
hxxps[://]helpop[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxps[://]optionalsupports[.]azurewebsites[.]net/
hxxps[://]helpift[.]azurewebsites[.]net/
hxxp[://]gratitudegear[.]azurewebsites[.]net/
hxxp[://]rescure[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]supportifymes[.]azurewebsites[.]net/
hxxp[://]betterright[.]azurewebsites[.]net/
hxxp[://]subjecthelp[.]azurewebsites[.]net/
hxxps[://]surepillar[.]azurewebsites[.]net/Mac08ShDMeEr0887/index[.]html
hxxps[://]befress[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]highelp[.]azurewebsites[.]net/
hxxp[://]lightingharmony[.]online/
hxxps[://]surepillar[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxps[://]alwaysasise[.]azurewebsites[.]net/Win08ShDMeEr0887/index[.]html
hxxp[://]a3-9n2[.]pages[.]dev/
Sample Phishing Sites from Phishing_kit_2:
hxxps[://]ambitious-pond-0291d5b03[.]4[.]azurestaticapps[.]net/Tokd02xFSD/index[.]html/
hxxps[://]www[.]security-tool-free[.]info/
hxxps[://]ceuz6yitkm9o0y[.]azureedge[.]net/0940/?edfgsddsad
hxxps[://]support[.]harmonyfit[.]shop/
hxxps[://]vicwir7eeaxhim[.]azureedge[.]net/2687/?Asfasdf
hxxps[://]96o2dxfreplj9k[.]azureedge[.]net/1938/?Adsfff
hxxps[://]b4pqvtrk3d223[.]azureedge[.]net/0166/?sdfdsda
hxxp[://]assistance[.]harmonyfit[.]shop/
hxxps[://]mx53v725zjhe[.]azureedge[.]net/
hxxps[://]vicwir7eeaxhim[.]azureedge[.]net/2376/?Afadf
hxxps[://]security-tool-free[.]info/
hxxps[://]ambitious-pond-0291d5b03[.]4[.]azurestaticapps[.]net/Tokd02xFSD/index[.]html
hxxps[://]b4pqvtrk3d223[.]azureedge[.]net/0166/?sdfdsdafgfg
hxxps[://]ceuz6yitkm9o0y[.]azureedge[.]net/0940/?edfgsd
hxxp[://]armorsecurity-tool[.]com/Win033Er00170ddx033/index[.]html
hxxps[://]9mhbtjl7367f[.]azureedge[.]net/
hxxps[://]iixmr32zpx8hvsm[.]azureedge[.]net/0166/
hxxps[://]security-tool-free[.]info/Win033Er00170ddx033/index[.]html
hxxp[://]security-tool-free[.]info/Win033Er00170ddx033/index[.]html
hxxps[://]vicwir7eeaxhim[.]azureedge[.]net/1680/?Asdadddv
hxxp[://]www[.]security-tool-free[.]info/
hxxp[://]www[.]security-tool-free[.]info/Win033Er00170ddx033/index[.]html
hxxp[://]faq[.]configwin[.]shop/
hxxp[://]service[.]harmonyfit[.]shop/
hxxps[://]ceuz6yitkm9o0y[.]azureedge[.]net/0940/?edf
hxxps[://]b4pqvtrk3d223[.]azureedge[.]net/0166/?sdfdsdafgfgasdasfdasd
hxxps[://]w3ym36rioq8884[.]azureedge[.]net/2687n/?ASFafadf
hxxps[://]armorsecurity-tool[.]com/Win033Er00170ddx033/index[.]html