Account takeovers cause billions of dollars in losses each year. The time to identify compromised users is the key to prevent these losses. There are several ways to identify such users before or during the account takeover via real-time phishing detection. HTTP referrers and phishing pixel beacon are the two such important methods.
HTTP referrers
HTTP referrers provide a wealth of information about where your site visitors are coming from. Found in your web server logs, these referrer URLs can help identify phishing websites targeting your brand in the early stages of an account takeover attack. Bad actors most of the times end up redirecting compromised users to your brand pages, giving them the false impression that were always on the legitimate site. When users come from such compromised site to your site, the URL of malicious website is captured in your web server logs.
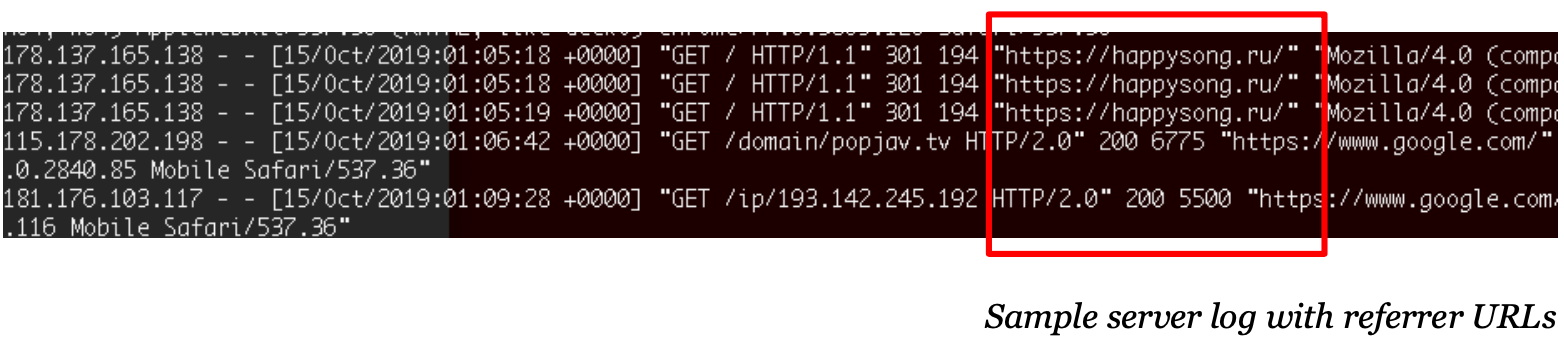
Phishing Pixel Beacon
Often bad actors clone login pages, landing pages of your site and develop phishing kits or phishing pages.
Pixel Beacons are small 1×1 pixel images embedded on your login pages. Anytime such a web asset is called from a domain which is not owned by you, it’s a straight red flag as it indicates someone has copied your login page template.
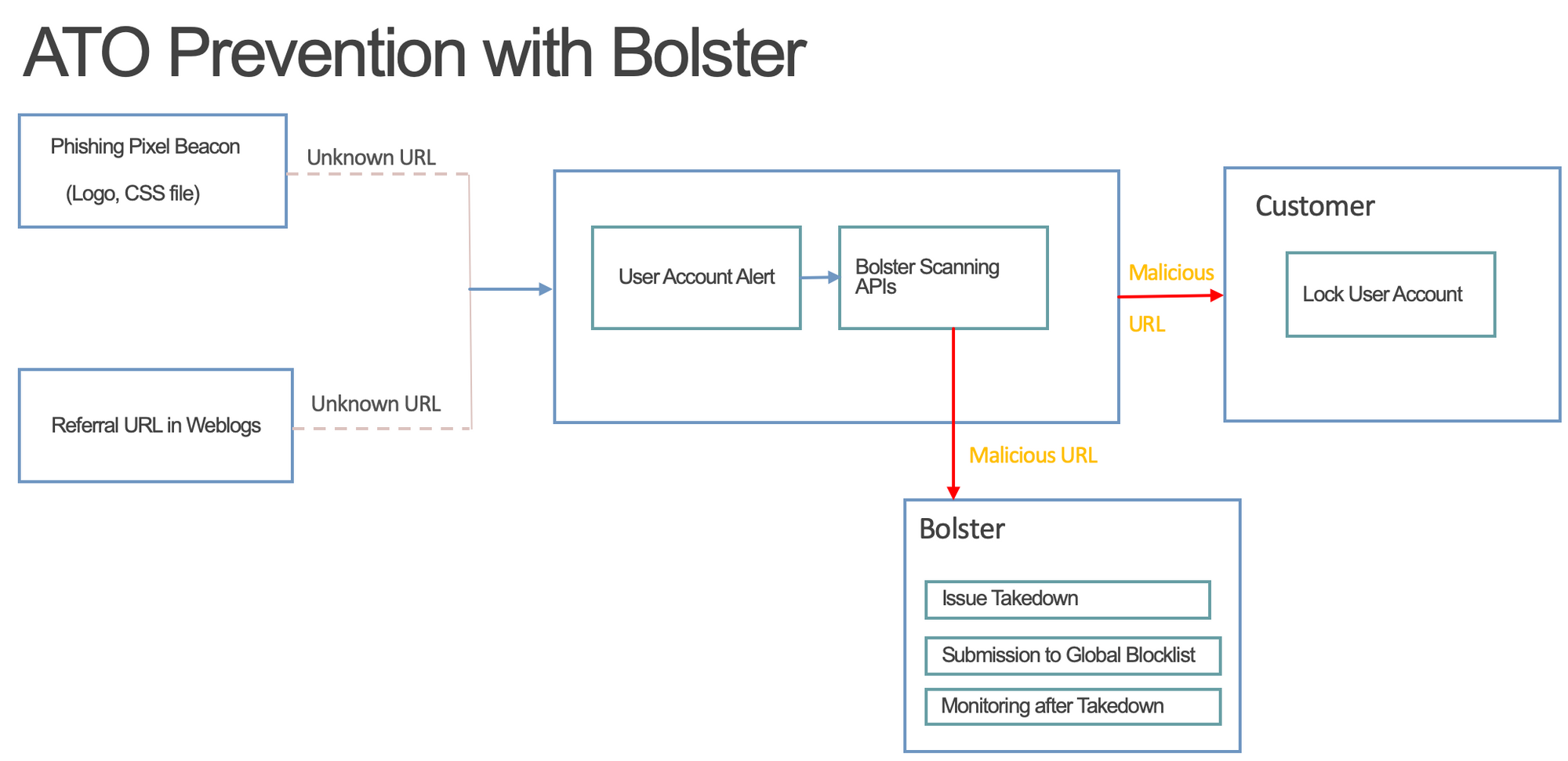
Harnessing URLs from the above techniques gives you real-time insights into phishing pages as they are being used in attacks. Bolster’s engine detects phishing on such URLs in real-time and helps you identify users who might be compromised. In addition to helping you with mitigation on such accounts by restricting access or resetting passwords, Bolster also performs automated takedowns on such sites.
Bolster ATO Prevention Workflow
Protect users from account takeovers before they happen
Instantly identify a compromised user when they get redirected from a malicious site and force a password reset or limit their access immediately. Flag, hide, or verify compromised-account activity to prevent platform abuse.
Automatically take down the phishing site impersonating your brand
Bolster sends takedown notices to hosting providers the moment it identifies a phishing site. This prevents one account takeover from turning into thousands.
Block malicious infrastructure proactively
Bolster’s extensive and rich threat intelligence API can help identify malicious infrastructure based on the domains in your referral logs. This helps you take additional proactive measures like blocking all traffic from such infrastructure.
Easy to integrate
Two simple endpoints to scan and detect phishing URLs from your referral logs.









