Introduction
There has been much talk lately in the media around Homograph attacks and Punycode domains following the disclosure of a browser vulnerability by Xudong Zheng. The technique itself is not new, as we’ve seen several talks in the past at security conferences from as early as 2012. The good news is most modern browsers have mechanisms to limit homograph attacks, and Zheng’s proof-of-concept exploited a particular vulnerability, as you can read in his post. Here is a punycode domain example:
German city of “München” becomes the Punycode “xn--mnchen-3ya”
A quick primer on Punycode domains before we go further: Punycode is a way to convert Unicode characters to a subset of ASCII – consisting of letters, digits, and hyphens. The encoding is primarily used in creating domain names in non-ASCII characters, also known as Internationalized Domain Names (IDN). As you can imagine, IDNs explicitly let people in different parts of the world register domains with characters in their native languages. As you can also probably imagine, bad actors figured out a way to abuse IDNs by registering very similar-looking domain names to popular websites, mainly to phish unsuspecting users.
As threat researchers, we decided to go hunting for such suspicious domains and document techniques we used along the way. We hope they help other researchers as well.
Searching For Newly-Registered and Punycode Domains
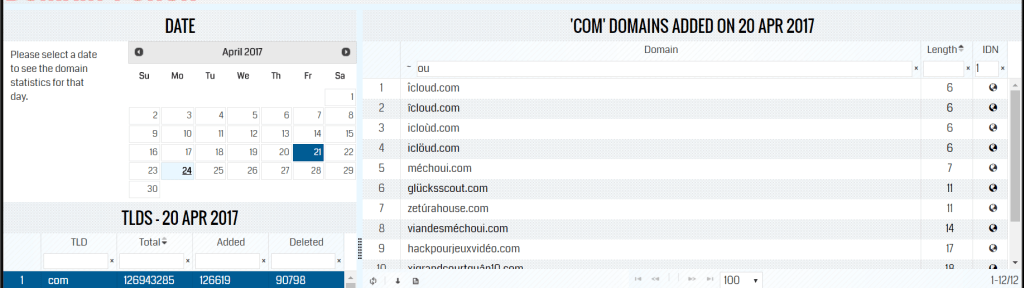
We can find various free and commercial services that update newly added and deleted domains in every zone daily. We use a handy tool from domainpunch.com to search for freshly registered parts in the past 30 days. They also provide an IDN filter or Punycode Domain filter, making searching for our target domains quite simple.
You can see in the image above a few suspicious domains that look like icloud.com (Apple’s popular cloud service). We went ahead and looked for more domains in the past 30 days, and here is a list of what we found searching by two characters “ou”:
There are a few points worth noting from the table above:
- Suspicious domains infringing on popular parts have existed for as long as we search the past. We limited our search to 30 days, but most likely, many domains were registered in the past. This makes it again worth noting that homograph attack techniques are not new.
- We have seen several new icloud.com variants since 15th April- a day after Zheng’s blog post came out. There is a possibility such attacks can increase in the near future as more bad actors get aware or get reminded of the technique.
- Expanding the search based on more combinations of letters will likely lead to more domains as we found 21 parts with just two letters, “ou”.
Digging deeper for Punycode Domainsusing Passive DNS and URL resources
Once we have a list of possibly suspicious domains, we can look for more clues to ascertain the maliciousness of the domain. One such technique is using Passive DNS to discover more evidence of the activities of bad actors. For example, we take the last domain in the list above: ıcıoud[.]com. A quick DNS lookup reveals the A record as 95.46.8.139 (when writing this blog post). When we plug this into VirusTotal’s Passive DNS lookup tool, we find more evidence of domains registered likely for phishing and an associated URL, blocked already by three blacklisting services.
Image2: Passive DNS lookup on Virustotal
Lastly, if we analyze the URL http://icld[.]info, we find more details on the behavior of the website. It just redirects a visitor to www.icloud.com, Apple’s original iCloud website. More details on URL analysis are here: http://urlquery.net/report.php?id=1493029021928. We also see very similar behavior with URL containing IDN: http://ıcıoud[.]com. It is safe to assume that all the domains listed in Passive DNS are part of the same attack – most likely registered for phishing users. It is also worth monitoring all IDN or punycode domains for an extended period, for example, a week or two, as they tend to go online several days after being registered.
We hope the abovementioned techniques help threat researchers uncover more malicious actors and help the security community take them down.
Happy hunting!
Resources
If your brand is facing typosquatting and attacks from punycode domains. Read More here on typosquatting
Scan punycode domains on CheckPhish for phishing and brand impersonation
Punycode Domains Generator to ASCII using https://www.punycoder.com/. It provides a comprehensive list of punycode domains list.