In the previous blog we introduced the elements of an effective Domain Risk Management (DRM) practice. The practice comprises 1.) active management; 2.) proactively acquiring domains to mitigate threats; and 3.) the continual monitoring of domains. Diving deeper into the DRM process, this blog will outline the ongoing need to discover and assess domain threats. The blog will then move into a discussion around the the challenges posed by scaling the DRM process.
Discovering the Threats
Once you have a comprehensive catalog of domains owned and managed by your organization, you can shift your attention to threats created by typosquatters and other cyber criminals. The domain variations that need to be considered for this exerciser extend beyond the simple character replacements, for example “app11e” instead of “apple.” The variants also need to include word combinations such as “apple-support” or “applepasswrd.” Fortunately, this is a discrete problem that can be solved rather than an undefined problem with infinite possibilities.
The objective here is to discover the various (and numerous) permutations that can exist for your organization’s domain names and the likely top-level domains (TLDs) that will be used. To do this, many organizations rely on open-source tools and platforms rather than building such a tool in-house. The output from these tools will need to be tracked in a simple, coherent way to ease ongoing management of this portion of the process. Also be mindful that whatever action you take (i.e. visiting a site) must be performed in a secure, safe manner to avoid a potential cybersecurity incident.
Step 1: Discover the various ways your domain names can be mutated
A popular tool used by many teams for discovery is the open source project “dnstwist” (https://dnstwister.report/). To use this project, go to the URL and enter your domain names in the <name.TLD> format (example: notion.com).

Figure 1. Screenshot: dnstwister
From this you will have two outputs. One is a list of “Found” domains, or domains that are variations of your domain name, currently registered and owned by another party. The other list comprises “Available” domains.
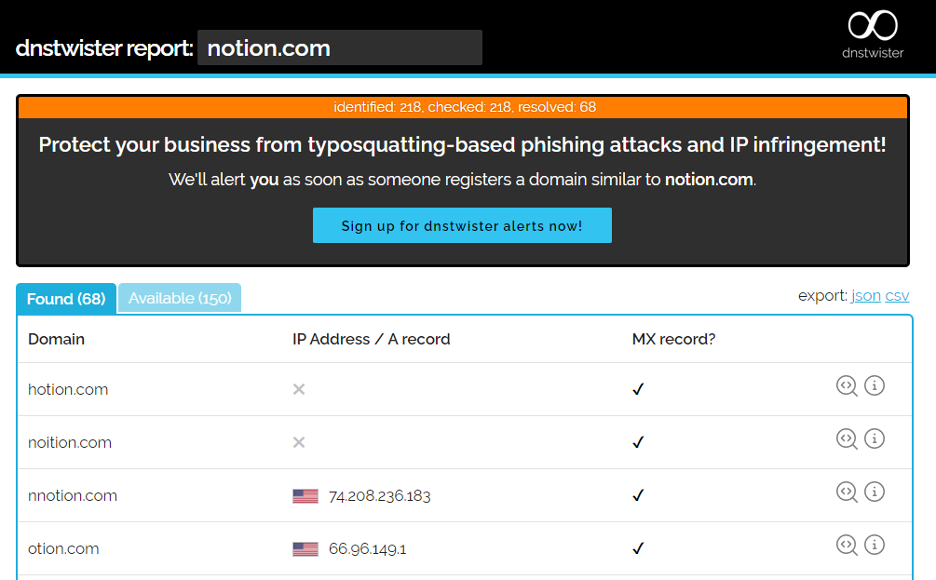
Figure 2. dnstwister sample output
Step 2: You will need to work through the list of found domains and safely identify those that are presenting a risk to your organization. This will take time! Once the threats have been identified, you will need to initiate a takedown request with the registrar that created the domain. This will also take time! Note as well that it is critical that for each threat identified, proper documentation is maintained for future reference. A takedown request can remediate the threat today, but the malicious domain can easily pop back up in the future.
Step 3: Having reviewed and mitigated any threats for the .com TLD, you now need to repeat the same process for every other TLD that poses a potential threat. For example, if notion.com were a retail site, then the TLDs .shop, .biz, .shopping, .store, etc would be likely next candidates for focusing threat discovery efforts.
Step 4: Steps 1 through 3 now have to be repeated daily. This is a critical step since a phishing, fraud, or malicious site can be set up at any time. Continuous monitoring, though demanding, ensures rapid detection and remediation of threats.
Domain Risk Management at Scale
The four steps described above, while simple, are by no means easy. They are extremely tedious and time consuming. As an example, using dnstwister, the domain notion.com generates 217 variations for just the .com TLD. When you consider all of the nearly 3,000 TLDs that exist, that number grows to 651,000 domains that need to be assessed and monitored! Oh and acquiring all of these domains is not a practical option as it would cost roughly $19.5 million per year, assuming an average cost of $30 per domain!
Ultimately, for effective DRM, it all comes down to adopting scalable processes. Domain variations is a discrete problem that can be defined. But, as we’ve discussed, the difficult part is monitoring the 651,000 domains on a daily basis to make sure that they have not been weaponized and activated for cyber attacks. The scale used in this example is for one domain. Multiply this by the number of domains a company has, and this task becomes crippling.
Wrap up & Next Steps
In this blog we discussed practical steps to size up and assess risks to your domain assets. It’s not an easy task as we’ve come to find out, being both tedious and time consuming. However, it can be greatly facilitated with the assistance of a dedicated system designed for this process. The final blog in this series will discuss the pros and cons of building such a DRM process in-house vs procuring a solution from a provider. If adopting a scalable, repeatable solution for DRM is a priority for you business and brand, then be certain to read the final blog!
Previous blog: Elements of an Effective Domain Risk Management Program
Learn more: Bolster Domain Protection solutions
Request your free trial today: Bolster Free Trial