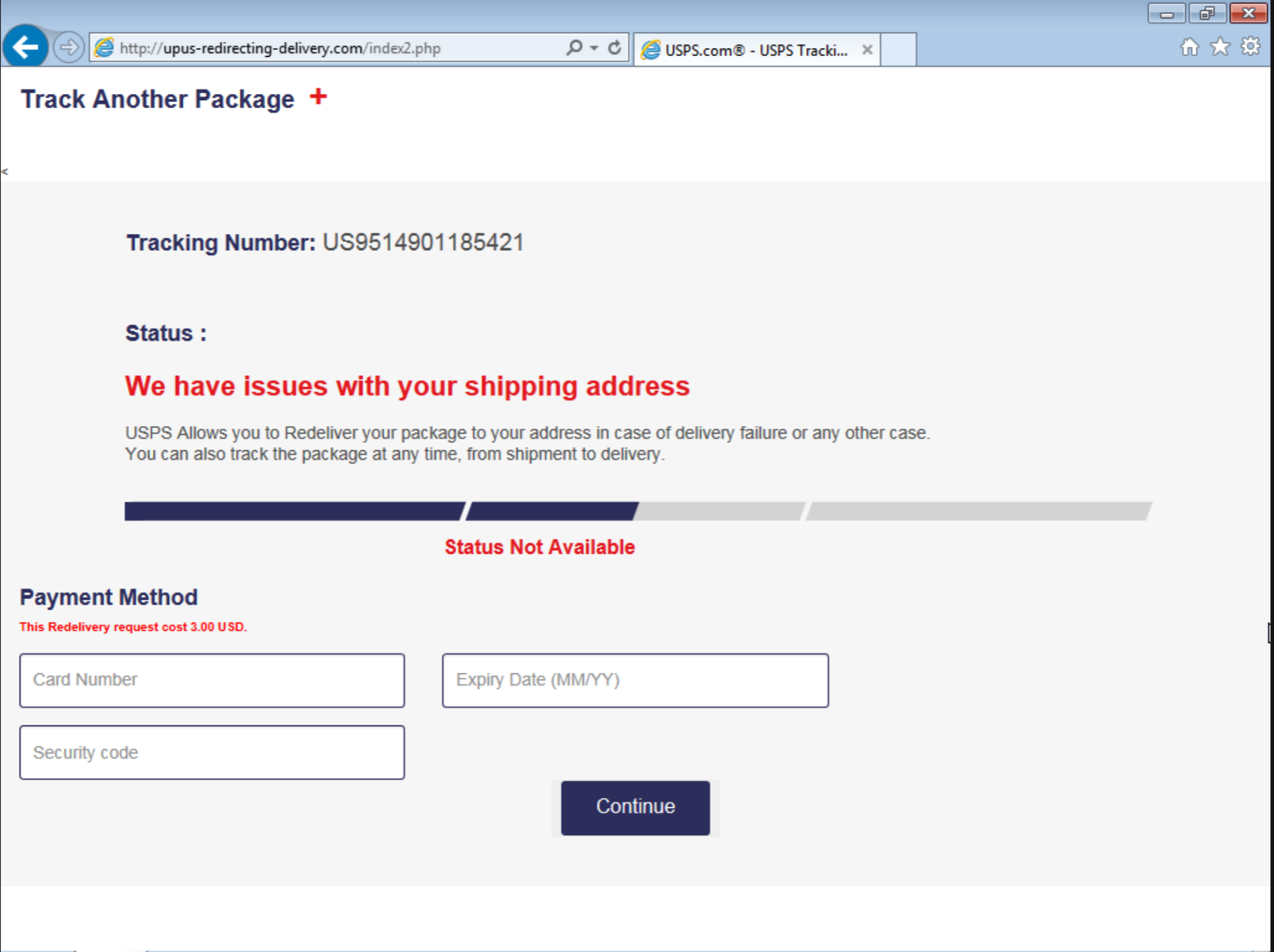
Phishing attacks continue to be a major threat to businesses, with cybercriminals becoming increasingly sophisticated in their methods. Phishing tracking is an essential tool for IT security and risk management professionals to identify and mitigate these risks. In this blog post, we will explore what phishing tracking is, the various techniques used, recommended tools for tracking, and best practices for effective implementation.
What is Phishing Tracking?
Phishing tracking is a cybersecurity technique used to detect and monitor phishing attacks. It involves creating a baseline of what normal activity looks like within an organization’s network, and then using this information to identify abnormal or suspicious behavior that may indicate a cyber attack. By tracking the source of suspicious emails and websites, IT security professionals can quickly address potential threats before they cause significant damage.
To avoid abuse from cybercriminals who use phishing attacks as their entry point into organizations’ networks, businesses need to implement effective phishing tracking measures. With continuous monitoring in place, organizations can proactively detect and respond to potential threats before they have the opportunity to inflict damage on their systems or data. In today’s ever-evolving threat landscape, investing in robust cybersecurity solutions such as phishing tracking is crucial for protecting sensitive information and maintaining business continuity.

Definition of Phishing Tracking
Understanding what phishing tracking is crucial in the fight against cyber attacks. Phishing tracking involves monitoring and collecting information on phishing scams to identify trends, patterns, and potential threats. Unlike other forms of cybersecurity tracking that focus on detecting abuse or anomalies within a baseline, phishing tracking targets specific malicious activities aimed at stealing sensitive information through social engineering tactics.
Phishing tracking is a crucial tool in the fight against cyber attacks, helping security professionals detect new emerging threats quickly.
The types of data collected in phishing tracking may include email addresses of victims and attackers, spoofed website domains used in the scam, IP addresses associated with the attack, and any malware or links embedded within emails. By analyzing this data over time, security professionals can detect new emerging threats quickly and avoid falling prey to them while strengthening their defenses against future attacks. Phishing Tracking is an essential tool for all IT security and risk management professionals who want to stay ahead of cybercriminals’ ever-evolving tactics.
Why is Phishing Tracking Important?
As the threat of phishing attacks continues to grow, it is crucial for organizations to implement effective anti-phishing measures. One key component of this strategy is phishing tracking. By monitoring and analyzing suspicious emails, organizations can identify potential cyber attacks before they occur and take action to avoid abuse or data breaches.
Early detection through phishing tracking also provides a baseline for measuring the effectiveness of an organization’s cybersecurity measures over time. By identifying patterns in attack attempts and successful breaches, IT security professionals can make informed decisions about how to improve their defenses against future threats. Overall, investing in robust phishing tracking capabilities helps mitigate risks and protect sensitive information from falling into the wrong hands.
Phishing Tracking Techniques
Phishing attacks are becoming increasingly sophisticated, making it harder to identify and track them. However, with the right tools and techniques, IT security professionals can still effectively track phishing attempts. Email header analysis is a useful technique that helps identify the source of an email and trace its path through different servers. By analyzing URLs in emails, IT security professionals can detect potential phishing sites before they cause harm.
Content analysis involves examining the content of an email or website to determine if it contains any suspicious elements such as misspellings or requests for sensitive information. Finally, IP address analysis is another important technique that helps track down the location of a phishing site or sender’s system. By combining these approaches with other security measures like user education and multi-factor authentication, organizations can protect themselves against increasingly sophisticated cyberattacks.
Email Header Analysis
The sender’s email address, subject line, and message ID are critical elements when analyzing the header of an email. By examining these components, IT security professionals can identify potential phishing attacks. The sender’s email address is particularly important as it helps determine the authenticity of an incoming message. In some cases, attackers may use a spoofed or fake email address to deceive unsuspecting users into clicking on malicious links or downloading infected files.
Another crucial element in header analysis is the subject line. Cybercriminals often use attention-grabbing and urgent subject lines to trick recipients into opening emails that contain malware or other threats. Examining the message ID also provides valuable information about the source of an email and whether it has been tampered with since its creation.
Overall, taking a deep dive into an email’s headers can provide valuable insights for detecting potential phishing attempts and protecting against cyber threats. Security teams should prioritize training employees on how to analyze headers as part of their overall strategy for mitigating risks associated with phishing attacks.
URL Analysis
When analyzing URLs for potential phishing attempts, it is important to consider the domain name in the link. Malicious actors often use similar-sounding domains or slight misspellings to trick users into clicking on a fake link. Additionally, tracking the URL redirect path can reveal any suspicious redirects that could lead to a phishing site.
Another crucial aspect of URL analysis is checking for HTTPS encryption status. A lack of encryption indicates that unauthorized parties may intercept sensitive information transmitted through this website. It’s important to educate employees and implement security measures such as SSL certificates and browser warnings when accessing non-encrypted sites to prevent falling victim to phishing attacks.
Content Analysis
Grammar and spelling errors in message body text can be a telltale sign of phishing emails. In order to appear more legitimate, attackers may attempt to mimic the writing style and language of a company or individual; however, these errors can reveal that the email is not actually from a trusted source. Additionally, urgent language such as “Action required” or “Urgent” is often used by phishers in an attempt to create panic and pressure the recipient into responding immediately.
Another common tactic used in phishing attacks is using a ‘From’ email address that does not match the actual sender identity. For example, an attacker might pose as someone from within your organization but use an external email address. It’s important for IT security professionals to thoroughly analyze all aspects of suspicious emails including grammar/spelling errors, urgent language, and discrepancies in sender information when tracking potential phishing attacks.
IP Address Analysis
Geolocation data of IP addresses from which suspicious emails were sent is a crucial aspect of phishing tracking. By analyzing the location information, security teams can determine whether the source of an email aligns with the targeted audience and identify potential areas or groups that are being targeted.
Investigating whether an IP is listed on known spam blacklists is another critical component when conducting phishing tracking. If an IP address has been flagged for sending spam emails in the past, it’s more likely to be associated with further malicious activity, including phishing attempts.
Furthermore, determining if the same sender has been associated with phishing attempts before helps track and monitor repeat offenders who might start attack campaigns under different names or domains. By identifying patterns and links between attackers’ tactics and behavior across various channels, IT security professionals have a better chance of preventing future attacks through early detection.
Tools for Phishing Tracking
Phishing tracking is an essential component of IT security and risk management. Open-source tools like OSSEC and Suricata are widely used for detecting phishing attempts by monitoring network traffic in real-time. These tools can be easily integrated with other security software to provide a more comprehensive defense against phishing attacks.
Commercial tools, such as Barracuda PhishLine and Ironscales, offer advanced features for tracking phishing campaigns across multiple channels. These solutions provide detailed analytics on user behavior, enabling organizations to identify trends and patterns in their susceptibility to phishing attacks. The use of these commercial tools often results in higher detection rates compared to open-source alternatives while providing additional layers of protection against sophisticated threats.
Open-Source Tools
Phishing attacks can be a major threat to any organization’s security. Fortunately, there are several open-source tools available that can help in tracking and preventing these attacks. PhishMe, Gophish, and SocialFish are three such tools that are widely used by IT security professionals.
PhishMe is an open-source phishing platform that allows organizations to send simulated phishing emails to their employees to test their awareness levels. Gophish is another tool that enables the creation of realistic phishing campaigns using pre-built templates or custom designs. Finally, SocialFish is a social media-based phishing toolkit capable of targeting individuals on platforms like Facebook and Twitter.
By leveraging these open-source tools, IT security teams can stay ahead of potential threats by detecting and reacting quickly before they cause significant damage. Using such tools helps organizations build more resilient defenses against cyber-attacks while providing valuable insights into employee behavior around potential threats in real-time.
Commercial Tools
When it comes to commercial tools for phishing tracking, there are several options worth considering. KnowBe4 is a popular choice that offers a range of features including simulated phishing attacks and training modules. IronScales provides automated incident response and real-time intelligence gathering to help detect and prevent phishing attacks. Proofpoint provides email security solutions, including advanced threat protection against business email compromise (BEC) and spear-phishing attacks.
Here are some key features offered by these three commercial tools:
- KnowBe4:
- Simulated phishing attacks
- Customizable training modules
- Automated reporting
- IronScales:
- Real-time intelligence gathering
- Automated incident response
- Smart inbox management
- Proofpoint:
- Advanced threat protection against BEC and spear-phishing
- Email encryption
- Security awareness training
Phishing Tracking Best Practices
To improve your phishing tracking efforts, focus on educating employees. Share examples of common phishing tactics and how they can identify them. Additionally, implement multifactor authentication to add an extra layer of security and reduce the chance of successful attacks.
Regularly testing and evaluating your phishing tracking system is also crucial to ensure it remains effective. Conduct simulated phishing attacks and analyze results to identify areas for improvement. By following these best practices, you can enhance your organization’s defenses against malicious actors attempting to trick employees into divulging sensitive information or downloading malware.
Educate Employees
Identifying and preventing phishing attacks is crucial to maintaining the security of your organization’s sensitive information. Educating employees on how to recognize and avoid these fraudulent emails can help prevent a potential data breach. Here are some tips to share with your team:
- Be cautious of unexpected or suspicious emails that urge you to take immediate action.
- Look out for any grammatical errors or spelling mistakes in the email, as these can be signs of a phishing attempt.
- Hover over any links in the email before clicking on them to make sure they lead where they claim to go.
- Avoid downloading attachments from unknown sources.
If an employee suspects a phishing attempt, it is important for them to report it immediately so that IT can investigate and take appropriate action. By training employees on best practices, you can strengthen your organization’s cybersecurity defenses against phishing attacks.
Implement Multifactor Authentication
Using multifactor authentication is crucial in today’s world where hackers are becoming increasingly sophisticated. Implementing hardware tokens or biometric authentication methods can add an extra layer of security to protect against unauthorized access. All remote access to company systems should require multifactor authentication, and sensitive data access should have this feature enabled.
Here are some ways that implementing multifactor authentication can help improve your organization’s security:
- Using hardware tokens or biometric authentication for added security
- Requiring multifactor authentication for all remote access to company systems
- Enabling multifactor authentication for sensitive data access
By taking these steps, you can significantly reduce the risk of a successful phishing attack on your employees. In addition to education and regular testing, using multiple layers of protection will make it much more difficult for attackers to gain unauthorized access and compromise your system.
Remember that cybersecurity is an ongoing process that requires constant vigilance and effort – staying up-to-date with new threats and implementing the latest best practices is critical in keeping your organization safe from cyber attacks.
Regularly Test and Evaluate Your Phishing Tracking System
Regularly testing and evaluating your phishing tracking system is crucial to combat phishing attacks. Simulating real-world phishing attacks can help assess employee readiness and the effectiveness of your system in detecting and preventing such threats. In addition to conducting tests, monitoring metrics such as click-through rates and reporting rates over time can provide insight into the overall success of your anti-phishing program.
Collaborating with third-party vendors, industry groups, or government agencies with expertise in effective anti-phishing measures could also benefit additional resources. Regularly assessing your phishing tracking system’s performance through various methods ensures that it stays up-to-date with evolving tactics used by cyber attackers.
Resources
Bolster Brand Protection Free Trial