Threat actors use a wide array of techniques in order to restrict researchers and automated crawlers from finding their hosted phishing websites. The earlier a phishing website is found and flagged as malicious by various scan engines like VirusTotal, and Google Safe Browsing, the sooner that website goes down.
A phishing website is rendered almost ineffective once browsers start showing the malicious website warning before visiting that website. To prevent early detection, and protect their cover from blowing up, threat actors use a wide variety of TTP (Tactics, Techniques, and Procedures), from geo restricting users based on the browser time zone to filtering specific IP ranges and User Agents.
Different TTP Used by Threat Actors for Restricting Access to Their Phishing Pages
- Filtering By Time Zone: By using the JavaScript functions like getTimezoneOffset() phishing sites are able to get the time zone of a visitor and are able to guesstimate the location of a user. If the visitor’s machine’s timezone offset isn’t in a specific range then the phishing kit might show them a different non-malicious webpage.
- Filtering User Agents: User-agent is a string that is sent with request headers to let the server know, which browser, and operating system the request is coming from. So that server can serve the content accordingly. This feature is also abused by phishing kit developers to selectively allow access to their phishing pages only when the user’s browser has a specific user-agent string. For e.g. a phishing kit might only show the phishing page to a user when their browser is Chrome running on Android OS otherwise the user is shown some random clean page.
- Filtering IPs, IP ranges: Threat actors usually block IPs or entire IP ranges from specific data centers, organizations, Threat intel services, or ISPs to avoid their phishing websites being found. They use various techniques for blocking the IP ranges, the most common being explicitly defining the IPs, and IP ranges in the .htaccess file’s deny list.
What is .htaccess File
.htaccess file is a high-level configuration file used in apache servers. It allows you to set up access rules at directory levels. It’s commonly used in websites hosted on shared hosting servers where the global rule file for the server can’t be accessed. Shared hosting providers are also very commonly used by phishing threat actors.
<Files 403.shtml>
order allow,deny
allow from all
</Files>
ErrorDocument 403 http://chasebank.com
ErrorDocument 404 https://mypdatemyprofilzsnowuses.buzz
Deny from 80.178.178.167
Deny from 80.178.164.36
Deny from 63.173.190.19
Deny from 212.73.246.73
Deny from 212.73.246.71
Deny from morgue1.corp.yahoo.com
Deny from 216.55.128.47
Deny from crawl8-public.alexa.com
Deny from 209.247.40.99
Deny from wfp2.almaden.ibm.comThe easiest approach to finding blocked IPs/IP ranges from phishing kits would be to scan the deny list in the .htaccess file of the phishing kit.
Bolster Phishing Kit Collection
At Bolster, we actively scan & collect phishing kits from threat actors-owned infrastructure.
For this analysis, we took the most recently collected 19000 phishing kits and scanned them for .htaccess files for the denied IPs, and IP ranges. A total of 3926 collected phishing kits were utilizing .htaccess files using deny rules for filtering visitors. Total 74257 unique IPs & IP ranges were found to be on deny list from all scanned .htaccess files.
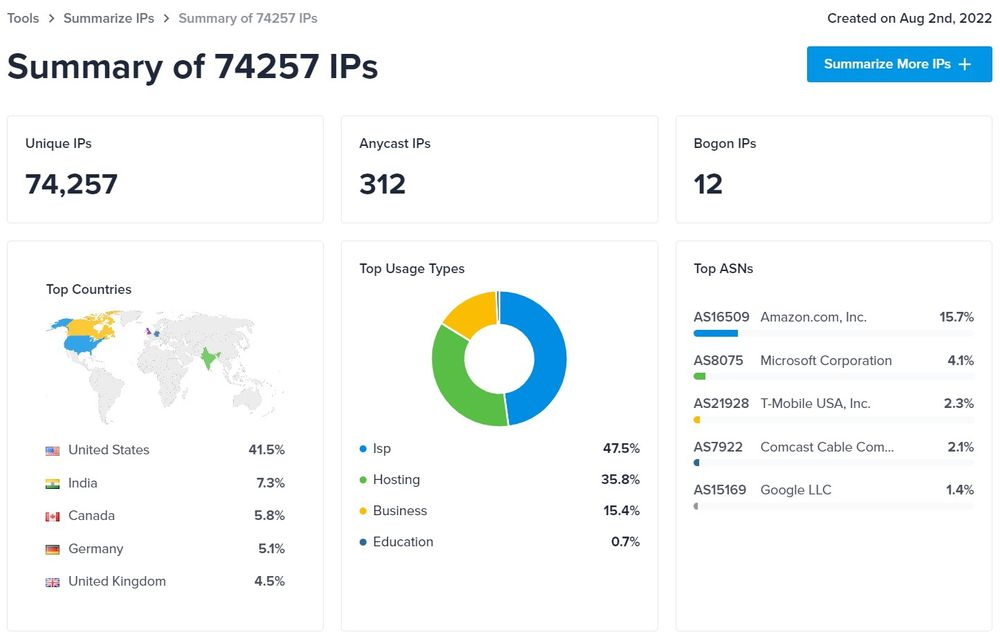
Blocked Countries
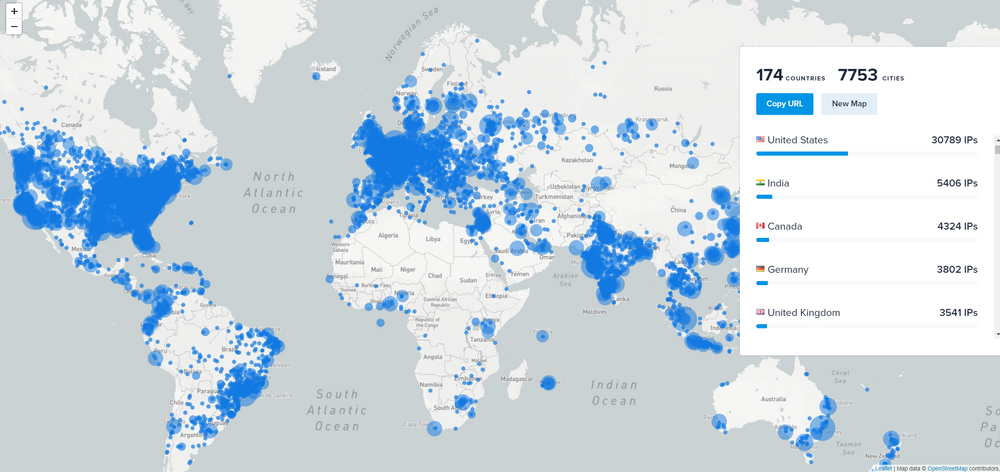
Blocked Organizations & ISPs
From the data in our dataset most commonly blocked IPs/IP ranges were from Amazon AWS, followed by the Microsoft data center IP ranges.
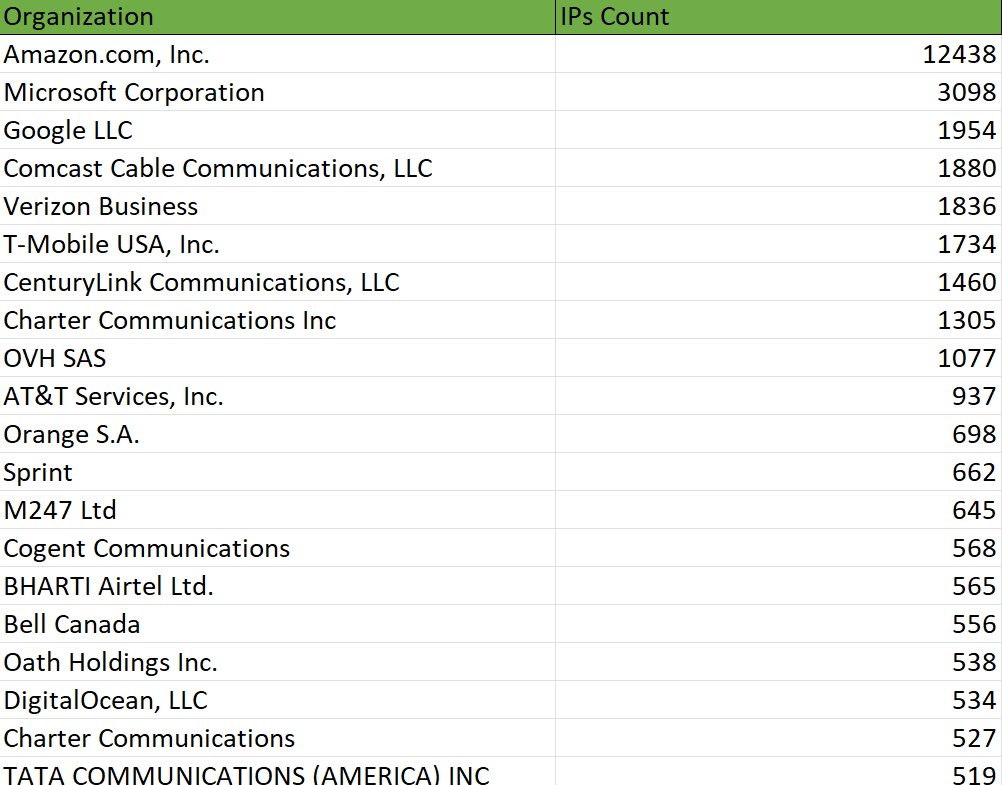
For the full list see the raw data in the GitHub repo.
Limitations
- As mentioned before using .htaccess isn’t the only method that is used by threat actors for geo-blocking visitors. There are other more effective and stealthy ways as well that are harder to detect & scan for.
- Each phishing kit has a different target audience, so threat actors will use the block lists accordingly. For e.g. if threat actors are targeting banking customers in the US they’d try to block access to the site from IPs outside of the US. But if threat actors are targeting banking customers of a bank in Malaysia, then they’d only whitelist Malaysian IPs.
At Bolster, we are aware of such blocking TTP used by threat actors and we use residential IP scanners and offer to scan using various user-agents of various browsers and devices to avoid such blockers.
Get your free trial for Bolster Platform here
About Us
This blog is published by Bolster Research Labs. We are also creators of https://checkphish.ai – a free URL scanner to detect phishing and scam sites in real-time.









