When researchers from Armorblox discovered a phishing attack from bad actors impersonating the well-known security company Proofpoint, it set off alarm bells for a lot of organizations and security teams that weren’t actively safeguarding against phishing attacks. These criminals targeted a global communications company with over 1,000 employees with a phishing email containing a link that led to a site that looked like a Proofpoint login page designed harvest credentials for Micorosft Offfice365 and Google email.
What makes this particularly newsworthy is that the attackers were targeting a cyber security company by impersonating their brand. As a cyber security vendor, they have an obligation to have robust security measures in place to instill confidence in their customers.
The CISO’s Role in Preventing Phishing Attacks
After speaking to multiple CISOs, a large number of them consider brand impersonation and typosquatting as a big issue, and teams are looking for tools to provide continuous monitoring and deliver defense-in-depth.
However, many in the security community see brand impersonation and typosquatting as a problem for legal teams or a concern only for enterprises who sell to consumers.
Defining roles to better protect your assets
For many businesses, their cybersecurity teams are focused on protecting the enterprise and its assets, i.e., employees, endpoints, data, infrastructure. They would argue that the Proofpoint phishing attack is not a Proofpoint issue since they cannot control who is targeted, and each enterprise needs to own their own security.
This is an outdated assumption and creates a huge opening for cyber criminals to take advantage of this “not my problem” mentality. Should a company care whether cyber criminals are impersonating the company to perform illicit acts and harm against their customers, employees, partners, and even other vendors? If Proofpoint cyber security does not own the taking down of a site impersonating their brand, then who does?
The point of this blog is not to say that Proofpoint did not care, or that anything specific lead to their phishing attack. But many CISOs believe that this is not a cyber security issue, which is simply wrong. If anything, this example of a phishing attack should solidify to organizations that phishing attacks are a company-wide issue that need to be managed from all sides of the business.
Cyber criminals do not care what your team’s responsibilities are. The most prolific attack is to set up a fake website, send phishing emails, and harvest credentials. It is an extremely simple tactic, and it works.
Detecting phishing attacks
Cyber security teams are the best equipped to detect, monitor, and remediate these sites because they know how to operate at Internet scale. In 2020, Bolster Research data showed that there were 19,000 of these types of pages created every day!
Recent Bolster data detected over 6000+ phishing sites mimicking popular apparel brands around the world. With proper access to cybersecurity data and phishing sites, organizations can detect phishing attacks as soon as fake sites arise, and conduct efficient takedowns before damage is done.
Bad actors do not care what industry you are in or what type of company you are. We have seen small cancer research companies to large, global financial institutions like Blackrock be spoofed. Hackers are just looking for organizations they can gain access to one way or another.
At Bolster, we see typosquating and brand impersonating sites targeting all kinds of enterprises across all verticals. Legal professionals do their best, but their toolsets consist of cease-and-desist letters, temporary restraining orders, or manual takedown requests. Their profession is not designed to solve this problem through AI and automation, which is exactly what is needed to keep up with the bad guys.
Internal legal teams are also not solely focused on cybersecurity issues. When the security team needs help, say with a phishing attack, their request for legal assistance falls in the queue with every other department’s requests, and isn’t necessarily prioritized as it needs to be.
Proofpoint Phish Analysis: The Impact of this Phishing Attack
This Proofpoint phishing attack led us to run a typosquatting report for Proofpoint, and hunt for other Proofpoint phishing attacks. The output of our research can be viewed using our CheckPhish Insights pages, which is free for anybody to use.
We quickly found a typosquat domain https[:]//proofpoint-zak.com. This domain looks highly suspicious, as it hosted behind Cloudflare and the SSL provider is also Cloudflare. Also, Whois information doesn’t reveal much information. There is a slight chance that it is owned by Proofpoint but for all practical purposes it seems like a phishing site.
The domain was created on 2018-10-22 and the domain registrar is Tucows–unlikely Proofpoint’s registrar of choice since the registrar for proofpoint.com is MarkMonitor. Inc. We would expect all Proofpoint domains to be managed by MarkMonitor, which is why from a security professional’s this domain seems like a phish.
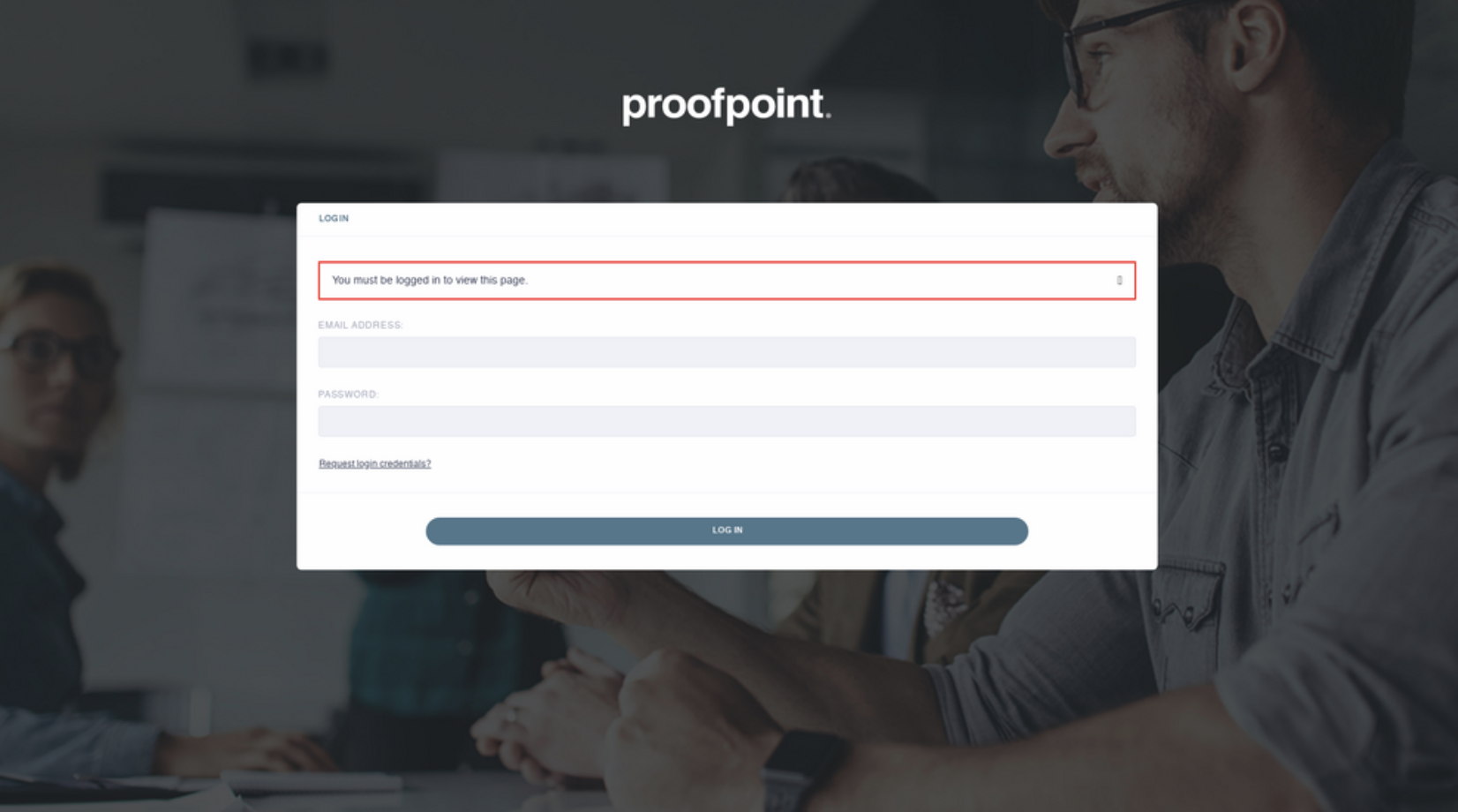
Another example of a Proofpoint phishing site is http[:]//ace-mortgage[.]space/ , which redirects to https[:]//sosmacomsv[.]com.br/sled/proofpoint-RD689-main-virtrudesign. This site is now currently blocked by safe browsing.
Bolster first saw it on October 31st, 2021 when the screenshot below was taken. It looks like the site has since been taken down, most likely by Proofpoint.
How to Protect Your Brand from Phishing Attacks
As previously mentioned, Proofpoint is not alone in attracting the attention of bad actors trying to impersonate their brand for financial and strategic gain. The recent (and historical) phishing attacks demonstrate the need for companies to take ownership of the brand impersonation problem and not leave it to other groups such as legal or brand protection.
Bolster provides organizations with an automated scanning technology to monitor for phishing attacks, as well as takedown services to help automatically remove the dangerous sites before they are used to trick your audience.
See what Bolster can do for your business, and request a demo today.
Learn more:
Bolster Brand Protection solutions
Bolster Phishing & Scam Protection solutions
Best Practices for Modern Brand Protection Whitepaper









