Many companies use social media platforms as an outlet to manage their relations with customers, troubleshoot user problems, and answer their queries.
Twitter is one of the key platforms where users can tag the brand’s handle with the troubles they’re facing or feedback about the services. The brand’s Twitter handle tries to troubleshoot the problem or refers the user to a support page or link where the user can raise requests.
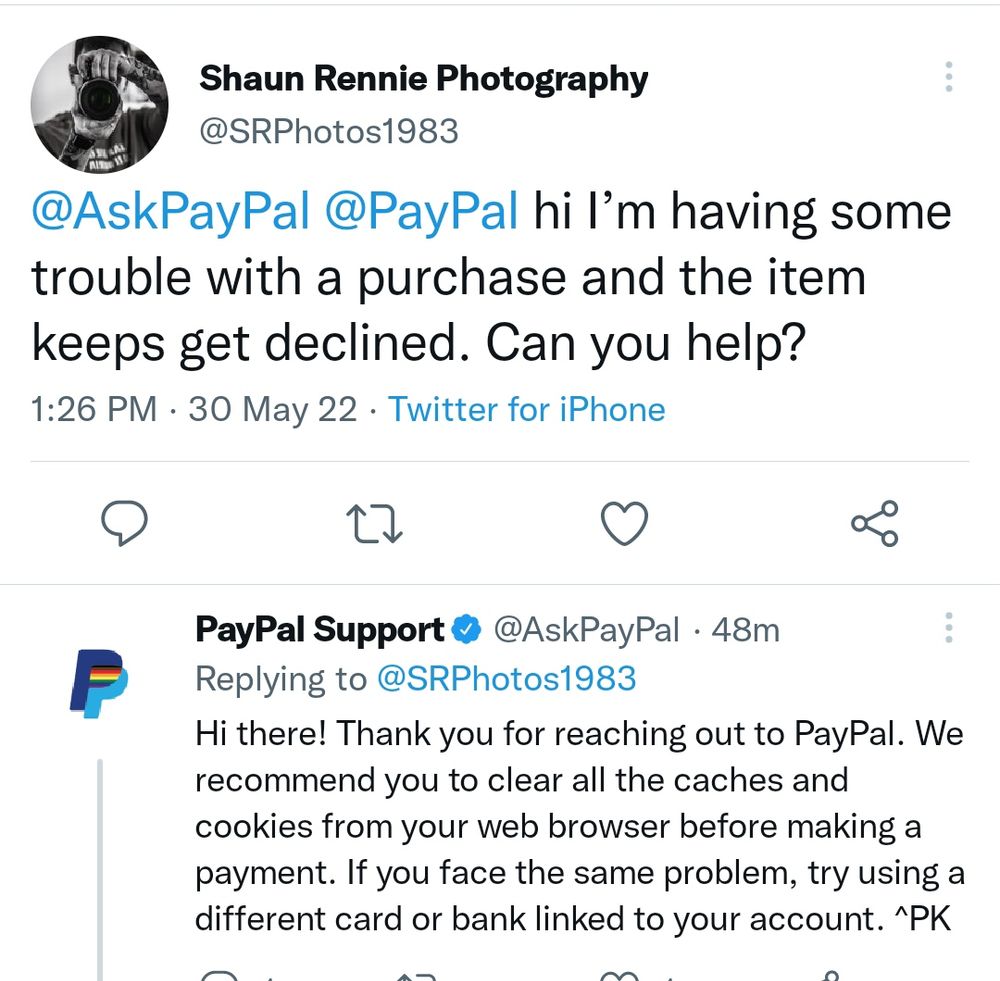
Twitter is a public platform, and all the Tweets are visible to everyone by default. It allows scammers to view the complaint tweets in which a brand, any related Twitter handle, or specific keywords are mentioned.
Scammers either reply to tweets from fake brand profiles, or they DM the user posing as the brand’s customer support. The end goal of scammers is to deceive the user into giving up confidential information and use that information to hijack accounts or cause financial damage.
Different Types of Campaigns
- Financially Motivated
A high percentage of these accounts primarily target users for financial reasons. These accounts try to trick the users into giving up their secret recovery phrase to hijack crypto wallets. Or they try to deceive the user into giving the username, email, passwords, and security question answers for their bank or crypto exchange accounts.
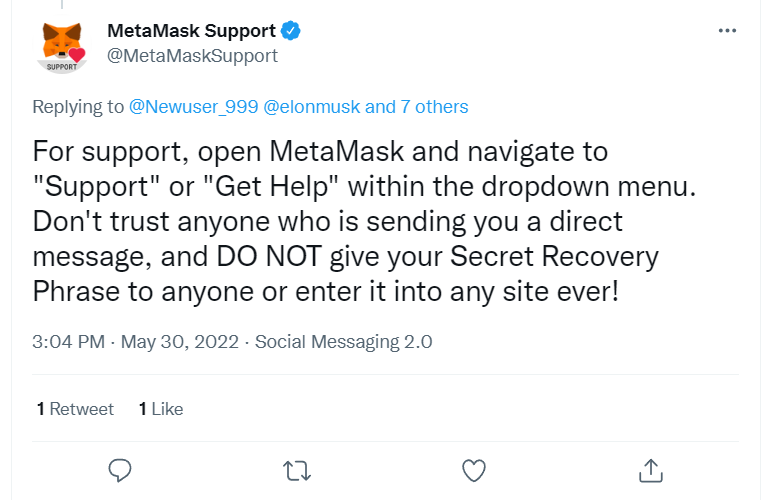
We made a few tweets using a honeypot account that contained keywords like help, support, and the name of popular crypto wallet apps. Within a few seconds of making tweets, we started receiving replies from fake customer support bots.
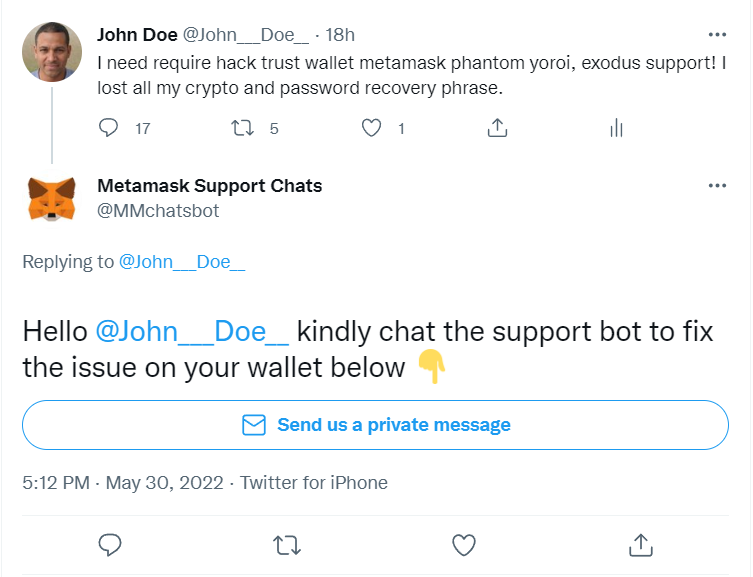
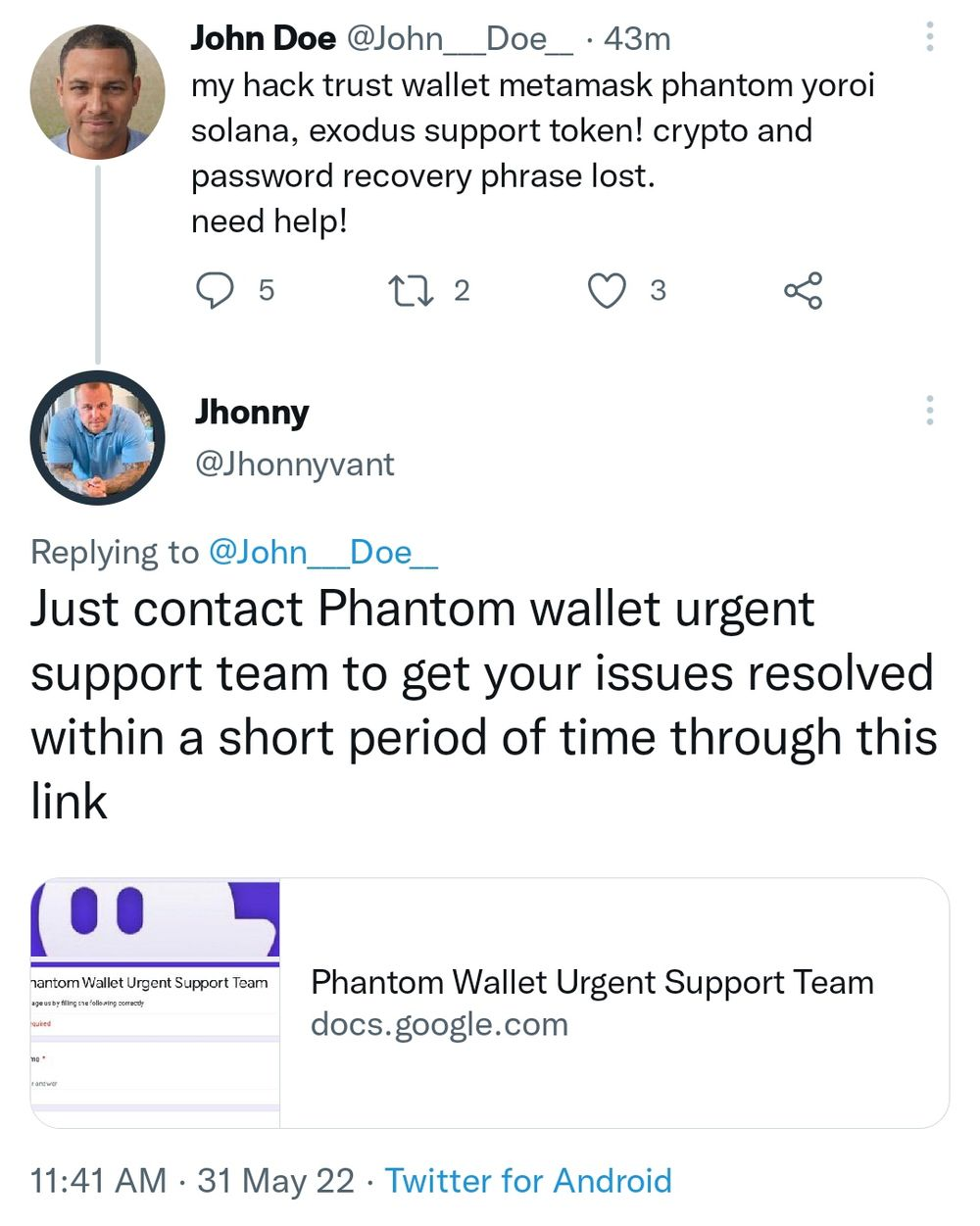
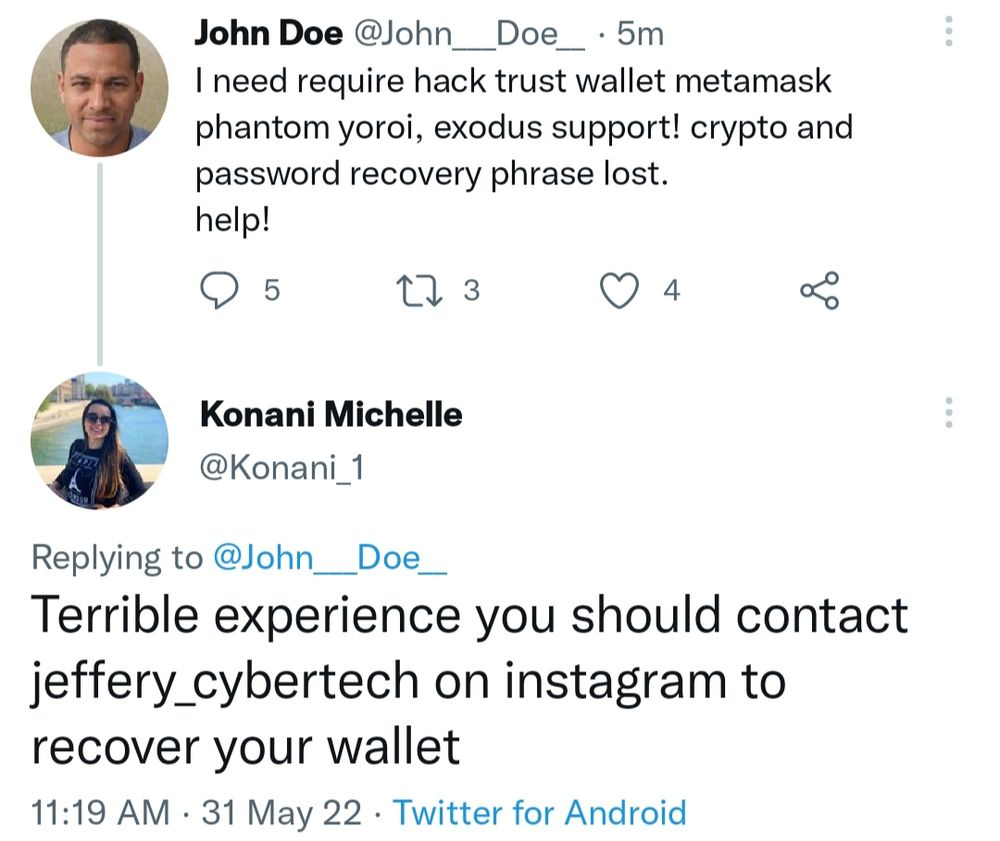
Some crypto companies’ customers are targeted to such an extent that their customer support has to write a warning message in each reply about not trusting any DM’s or replies claiming to be from them.
- Account Hijacking
Another motivation for these scammers is to hijack high-profile, verified accounts or accounts with a highly desired username.
These hijacked, high-profile, verified accounts with a large following are later used in promoting scam campaigns to the masses.
Usually, hijacked high-profile, verified accounts are short-lived. Once they’re spotted or reported, Twitter rollbacks those accounts to their original owners. Scammers have a short time window after hijacking such accounts, and they’re aware of it.
After 20 years working in tech, I almost fell for this phishing attempt targeting my Twitter account credentials. I even clicked the link, entered my username, and only stopped when prompted for my old and new password. pic.twitter.com/4mILEEEKV6
— Kelsey Hightower (@kelseyhightower) May 23, 2022









