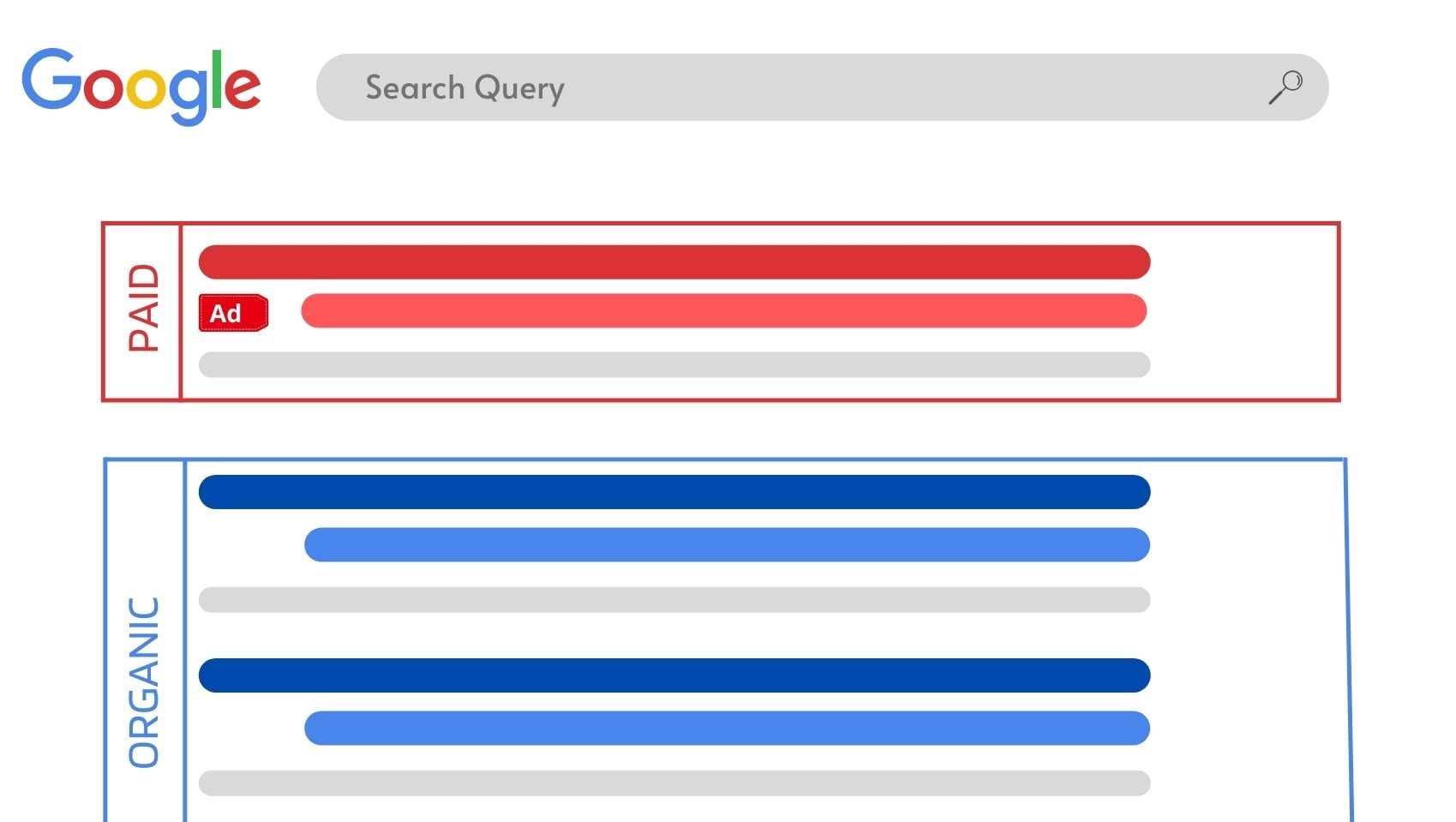
Did you know, that scammers can weaponize Google Ads to target a brand and its customers? Anyone can buy and run ads on Google Search for any set of keywords. All they need to do is pick and keyword and pay for it to be on top of the results page. Scammers do the same. They buy and run ads that show up on top of Google results when a customer/ user searches for a specific brand-related keyword.
When clicked, these ads redirect users to phishing or fraudulent web pages. Some of these websites redirect to phishing pages of the target brand and others might redirect users to elaborate scams like asking them to call a fake customer support number.
These phishing pages trick users into giving up confidential information such as their login credentials, account details, and Personal Identifiable Information (PII). The fake customer support webpages ask users to call a fake customer support number and carry out their scam.
Scammers use this collected information to hijack accounts, drain crypto wallets and use the Personal Identifiable Information to build more data points on their future victims.
Examples of scam campaigns on Google Ads
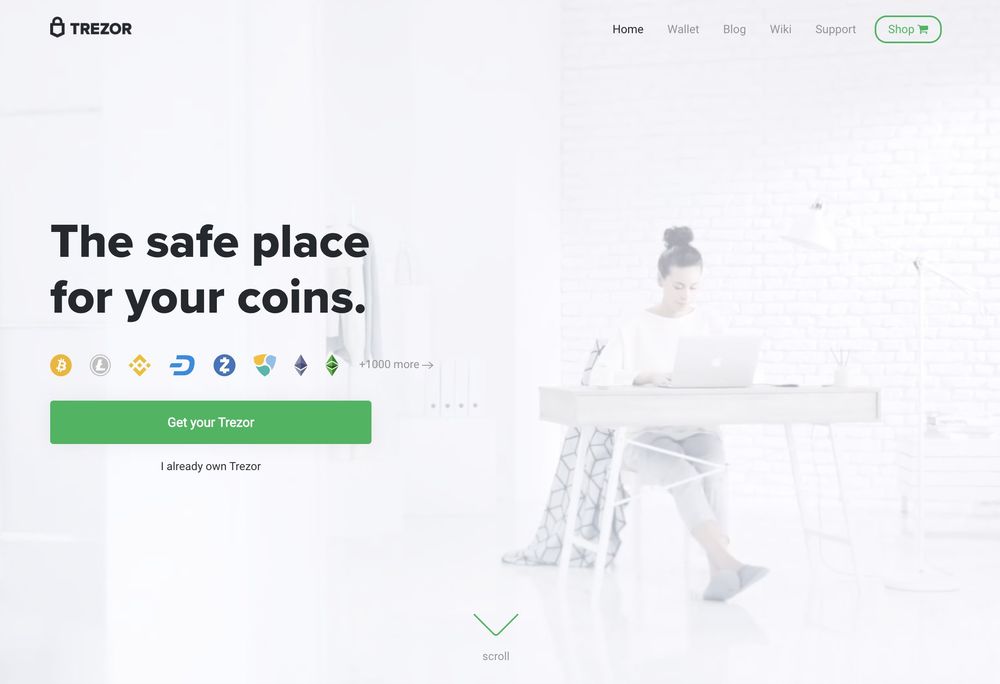
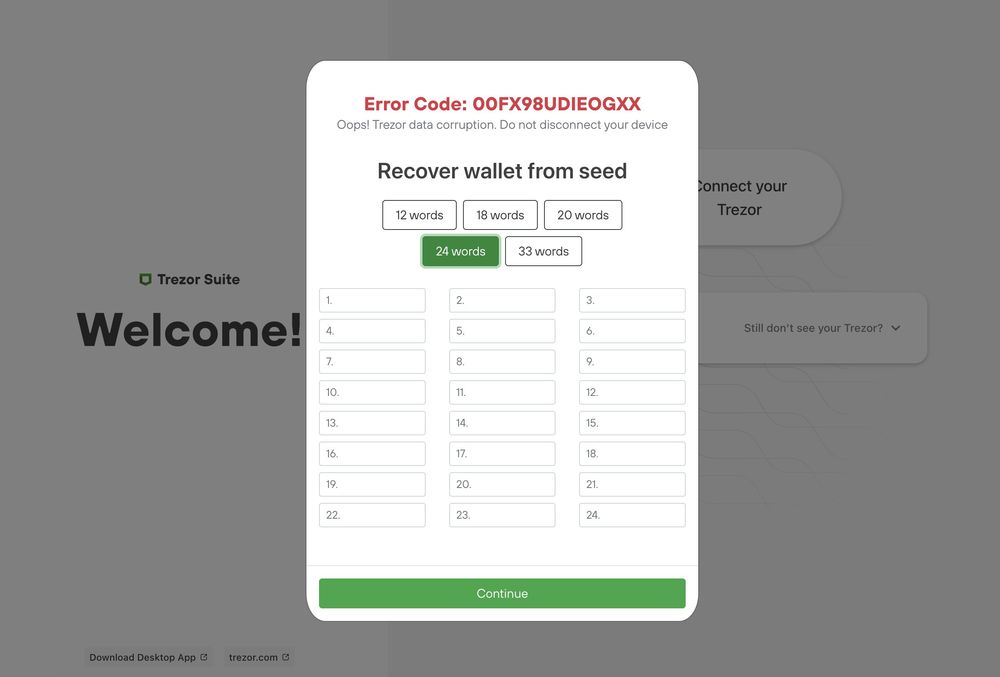
Recently, attackers ran a scam campaign targeting Trezor (crypto wallet) users. Whenever a user searched for Trezor-related keywords on Google, they saw ads impersonating the Trezor website pop up on top. These ads lead to fake look-alike websites that try to phish users for their wallet seed phrase. If the victim enters the seed phrase, their crypto wallet is drained empty by the scammers.
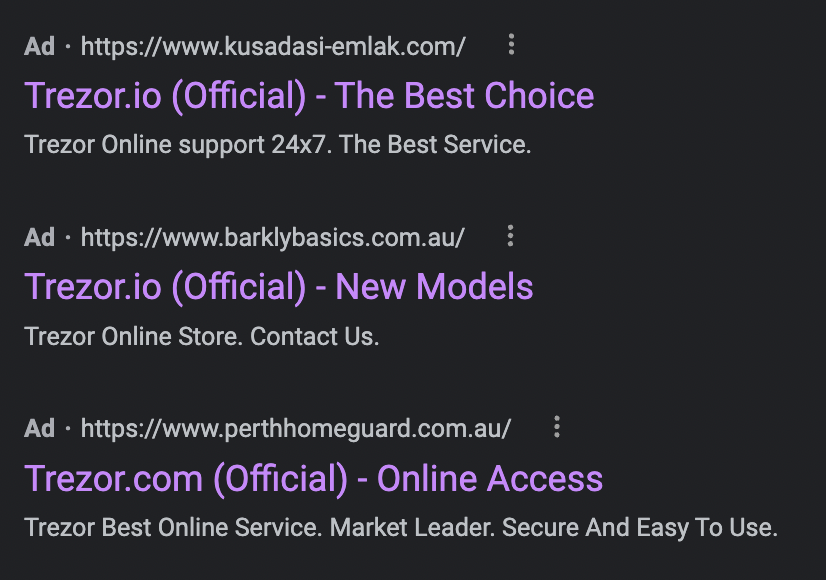
In another uncovered ongoing scam, a Twitter user was able to identify a fake Google Ads campaign that was able to steal over 100 ETH (Over 200 thousand USD)
Using an exploit with Google ads, scammers are able to make the real and scam URL look exactly the same.
Already ~100 ETH stolen pic.twitter.com/eSv20uKIVK
— Serpent (@Serpent) May 10, 2022
Similar search ad campaigns are used to run ads for fake hotlines of brands and banks. When users search for their bank helpline number or customer support number, they get an ad on top for the customer support number that scammers control. If victims call the number, scammers try to social engineer them into giving away confidential bank account info.
Steps to Protect
For Individuals
- Examine URLs carefully for lookalike and typosquatting websites. Check if it’s the legitimate domain of the brand.
- The domain in the ad might look correct but once opened, it might redirect you to a lookalike domain. So recheck the domain once you’re on the website.
For Brands
- Regular monitoring of brand and industry-related keywords on search engine results.
- Proactively monitoring lookalike domain registration. Such domains might later be used in search engine ad scam campaigns or other scams. In the past, attackers used to employ spam emails to promote their scam & lookalike websites. Recent trends show that some attackers are using search engine results manipulation either by means of buying ads or gaming the search result ranking algorithm to widen the reach of their scam campaigns.
Bolster monitors for registration of lookalike domains of your brand and provide continuous monitoring on multiple search engines for fake, lookalike scam ad results for your brand. Click here for a free report assessing your company’s typosquatting threat landscape.
About Us
This blog is published by Bolster Research Labs. We are also creators of https://checkphish.ai – a free URL scanner to detect phishing and scams sites in real-time.
If you are interested in advanced research and uncovering of new scams or working with cutting-edge AI, come work with us at the Bolster Research Labs. Check out open positions here