Since the World Health Organization (WHO) declared a worldwide pandemic in March, life as we knew it changed. Much of the world is sheltering in place, and virtual everything has become the norm. Cyber criminals adapted quickly, and the Internet was immediately flooded with online phishing and fraudulent websites. The campaigns covered everything from fake local government COVID-19 updates to offers to help with the U.S. Government Paycheck Protection Program. As pharmaceutical companies race to develop a vaccine, life returning to normal seems like a futuristic fantasy, similar to establishing a colony on Mars.
Bolster Research analyzed more than 245 million web pages to identify the top company brands used for phishing and online fraud campaigns. Some of this data is available on Bolster’s community product checkphish.ai. The chart below shows the total number of new phishing and fraudulent web pages found by Bolster’s AI platform.
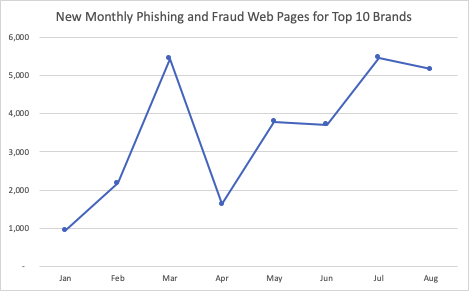
The top 10 brands are responsible for nearly 30,000 new phishing and fraudulent websites from January through August in 2020. Every month, there are approximately 4,000 new phishing and fraudulent websites created for just these 10 brands alone. The number of these sites increased in February, with a huge spike in March, aligning with the WHO pandemic announcement. The number of new malicious sites decreased in April and started rising again in the summer months, peaking at a level higher than March.
The data reveals that the increase in phishing and fraudulent websites in April through August was driven by three companies: Microsoft, Apple and PayPal. The other seven brands show small increases, but in aggregate do not reach the high levels from March.
Among the three brands driving the sharp increase, Microsoft accounts for more than half of the total number of phishing and fraudulent web pages. Detailed analysis illustrates that the attack focused on credential phishing through the creation of fake login pages for the company’s leading SaaS services. The pages were crafted with a high level of attention to detail, indicating the sophistication of the threat actors. Phishing and fraudulent websites related to Microsoft continue to increase, and in the first half of September exceed the number of malicious web pages created in March.
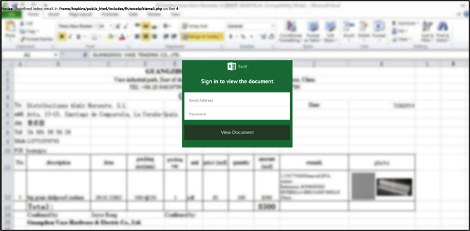
PayPal spiked in May and has since trended downwards, though still higher than its March level. The data illustrates most were instances where PayPal was used to collect fraudulent payment or harvest user credentials. One novel campaign purported to add money to an account by only providing credentials. To make the site look authentic, the fake site added endorsements from people who made hundreds of dollars.

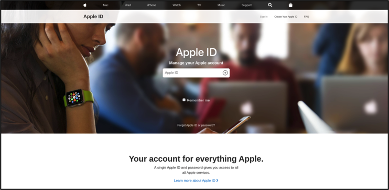
Apple experienced a very large spike in July, with more than 10X its usual volume of phishing and fraudulent websites, and returned to normal levels in August. The Apple campaign attempted to gain user’s Apple ID login and password information. The threat actor created multiple domains that displayed a fake Apple ID login page. The URL used was designed to trick users into thinking it was a legitimate Apple domain by using “secureupdate.appleID.com.” However, it is clear the domain is “duilawyeryork.com.” The URL and screenshot of the landing page are show below.
Though the total volume of new phishing and fraudulent websites created is alarming, there isn’t sustained growth in new web pages. Starting in September, the volume of malicious sites for these two brands trends downward to pre-pandemic levels.
One reason for the explosion of phishing and fraudulent websites for SaaS services is due to a change in tactics by cyber criminals. With broad adoption, criminals are leveraging legitimate enterprise SaaS services to harvest user credentials or trick users to download malicious attachments. Rather than sending a piece of malware as an email attachment, users are sent a link to a file that is stored on an enterprise cloud storage service for download. In some cases, the login page is a fake designed to collect usernames and passwords. In other cases, logging in provides access to a file that looks legitimate but is malicious.
Hikvision, a Chinese surveillance company, is also listed in the top 20 brands for phishing and online fraud campaigns. The company manufactures and sells a comprehensive portfolio of surveillance equipment. The number of malicious sites jumped to 300 in July and has since fallen back to near zero fraudulent websites. The campaign targeted Hikvision’s customer accounts allowing criminals to gain access to surveillance data. The sites were hosted in multiple countries, indicating the hackers were likely targeting a large multinational corporation. Most of the sites have been removed, a sign that this attack was a specific campaign with a start and an end.
The Internet continues to be a dangerous place, and it gets more and more dangerous every day. Most alarming is the rapid increase of new phishing and fraudulent sites being created. Extraordinary events, such as a global pandemic can cause large spikes in phishing and online fraudulent campaigns. However, as the data illustrates, the number of new malicious sites being created is now at a higher level, with no extraordinary shocks. The sheer volume means that an attack will inevitably succeed, and why ridding the cesspool of phishing and fraudulent activity is essential.
Bolster has developed AI technology that evaluates more than 1 million web pages per day. Using a combination of deep learning, natural language processing, and natural language processing results in a 99+% accuracy in determining whether a web page is designed for malintent. Leveraging AI and automation, Bolster is able to remove these sites within hours of discovery with zero human intervention. You can learn more about our offering by visiting our website or signing up for a free trial. Free scanning of suspicious URLs or sites can be done using our community product available at checkphish.ai.
Learn more about Bolster’s Phishing & Fraud Prevention Solutions.
Request a Free Trial today.








