My parents were visiting from India and my mother who is very keen on learning new things on the internet wanted to access her bank account online. Having heard about WannaCry Ransomware in the news in India she wanted to know if it safe for her to access her bank account online. I asked her how does she know that she is going to know that she is visiting the real site? She simply said I see a ‘lock’ in the browser. I have happy and terrified at the same moment. Happy because she knew basics about SSL and TLS and terrified because we all in security community have teaching that https protects against everything.
How an attacker can obtain legitimate SSL certificate for any domain
Thanks to free SSL services anyone can get a certificate with no verification.
Getting SSL Certificate for Gmail homograph domain gmạil.com
- https://www.sslforfree.com/
- https://letsencrypt.org/
- https://buy.wosign.com/free/
We went about just doing that. We used LetEncrypt for our example. It took less than 5 minutes from buying to domain to getting an SSL certificate on Ubuntu 16.04. See steps below:
wget https://dl.eff.org/certbot-auto chmod a+x ./certbot-auto ./certbot-auto certonly –standalone -d xn--gmil-6q5a.com

Then tested quality of certificate from SSLLabs at Qualys and it got a nice B Rating

Finally you can see that we were successfully able to register Gmail the gmạil.com homograph domain. You can check it out in your browser.
We tested with Firefox, Chrome, Safari, IE and Microsoft Edge (latest versions of each). To our surprise IE was the only browser that expand domain gmạil.com to its punnycode ‘xn--gmil-6q5a.com’.
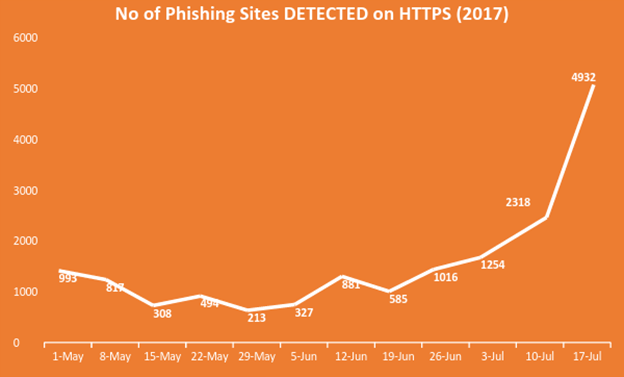
Trends on phishing attacks that use SSL
At Bolster, we are seeing a consistent rise in phishing attacks over https. Our latest figures show nearly 10% of all real-world phishing urls were hosted on https with legitimate SSL certificate. In the month of July 2017, we saw a massive surge in phishing sites on https. This is a worrisome trend because we know users are more likely to click on a phishing url if it is hosted on https.

Ways to identify these scams
Ways to identify these scams and protect yourself. As a security community, we should stop telling people that just because they see “https” or “lock” in the browser it is ok to trust the website. We need to educate them more. Here are the few steps one can take if they want to be sure that they are visiting trusted website.
- Do a domain lookup and see who is the registrar of the domain. Is there a real phone number and address? You can use whois lookup tool like the one provided by DomainTools, to determine if domain is owned actually by the company and not by an imposter. You can clearly see contact information for our site ‘gmạil.com” is not that of Google.
- If url looks suspicious to you then you can use either Phishtank or CheckPhish to determine whether site is phishing or not.
- Check who has issued the certificate? Is it a trusted authority?
- Check who the certificate was issued to. It should have the details of the organization you were expecting for the domain.
Resources
- Phishtank – a database of phishing urls
- CheckPhish – an AI based tool to detect phishing in real time
- Dnstwist – Domain homograph generator
This is more technical version of the post on info-sec magazine