Today, more than 4.6 billion people are on social media, representing 58.4% of the total human population.
Even businesses realize social media’s massive potential, with 73% of all small businesses investing time and money on these platforms. As ingrained as these platforms are in the daily life of consumers, they’re also home to opportunistic scammers and fraudsters trying to dupe users with a multitude of scams.
As a brand, you must be aware of all these scams and their potentially detrimental effects on your business.
But it’s not always easy to detect these frauds.
Why is it So Hard to Detect Social Media Scams?
Social media scams are rampant on almost every platform.
Social media fraud losses comprised 26% of the total fraud losses reported in 2021. This number represents a shocking 18-fold rise compared to the previous four years. It’s a lucrative option for malicious actors because of how hard these scams are to detect.
Let’s take a look at what factors are contributing to the complexity of social media scams.
More than 20 social media platforms to manage everyday.
There are over 20 social media platforms with over 250 million monthly active users (MAUs) and 7 with over a billion.
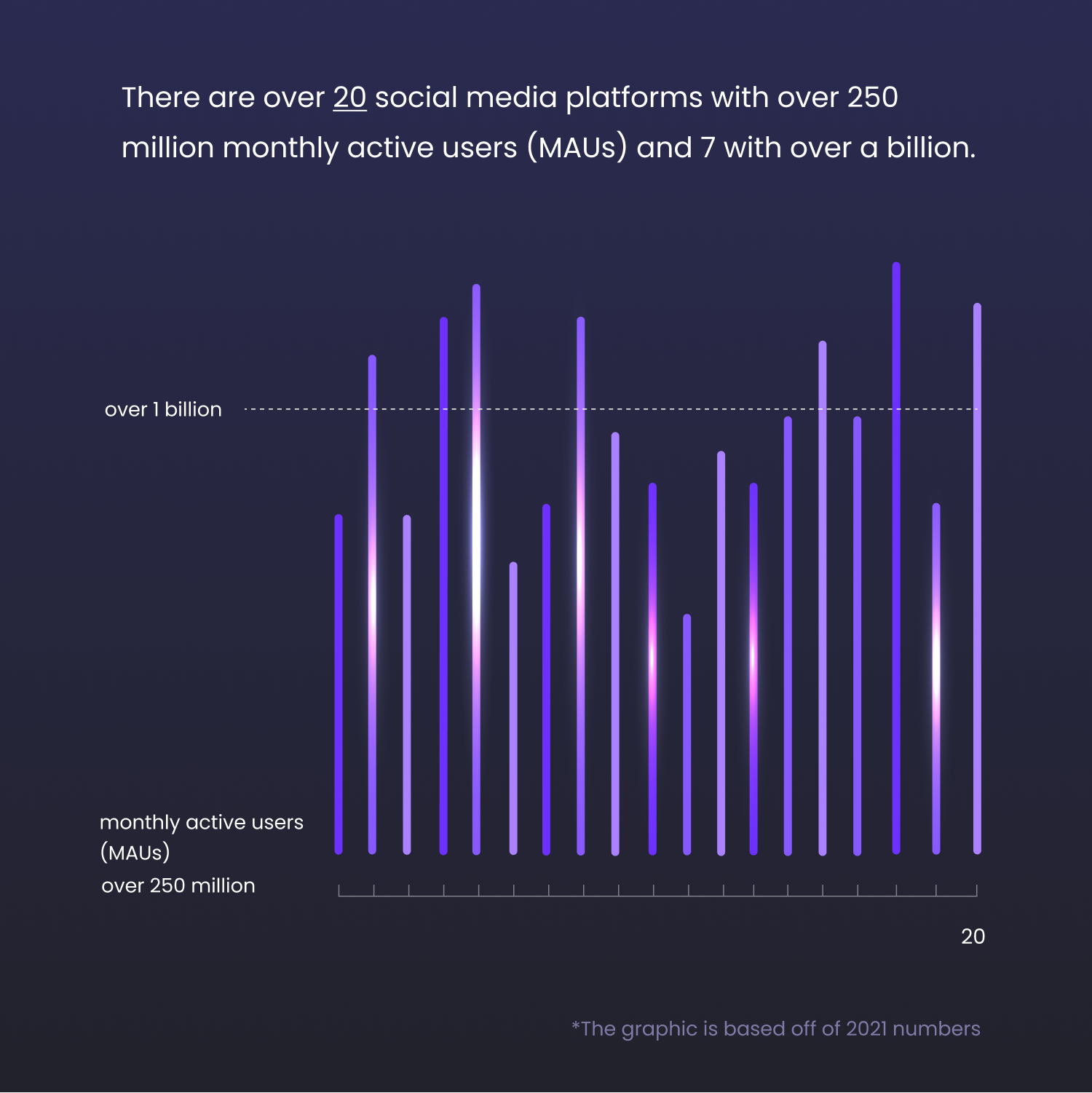
These numbers are only expected to grow further.
With the number of regional social media platforms exploding, billions of new users are connecting to these expanding networks. With each user connecting, that user is also expanding the digital landscape of their employer. This phenomenon’s sheer scale and complexity make it a nightmare for IT security teams fighting against social media scams.
Understaffed and overworked, these teams will have to spend each waking hour jumping from site to site, trying to bring down fraudsters from targeting their employees, partners, and expanded audience connected to their brand.
There are several different types of frauds and social media scams to look out for.
Social media provides easy public access to personal information that can facilitate a variety of social media scams.
Pages and profiles sell pirated and counterfeit goods, conduct crypto, currency, and gift card scams, enable phishing and executive impersonation, and send out fake ads. Each scam on each platform requires a different technique to detect and take down, especially when each technique is meant to target different audience members.
Social media isn’t governed by a common set of regulations.
Unlike websites that come under the purview of regulatory scrutiny and a globalized system of common control, social media platforms are largely unregulated.
Each platform has policies that dictate what to post, how to post, and how to report abuse. This means when it comes to brand impersonation instances, and organization’s SOC team needs to approach each platform differently.
In addition to an already heavy workload, learning the ins and outs of regulations for the 20+ platforms is nearly impossible. Combine this with the sheer amount of posted content the security team must scan for fraud, and one can understand why social media scams are so hard to detect.
Reporting and taking down fraudulent posts on social media is hard.
When traditional website scouring techniques falter to detect social media scams on social media platforms, SOC teams must develop new techniques for each platform.
Even after fraudulent, infringing posts have been identified, taking them down is another task altogether.
Each platform has different definitions of wrongful posts with different steps to take down such content. Moreover, due to these differences, takedown success metrics need to be tracked for each platform individually, and this makes reporting complicated, with many readings to check daily.
The first step to putting a stop to these scams is to understand how they work.
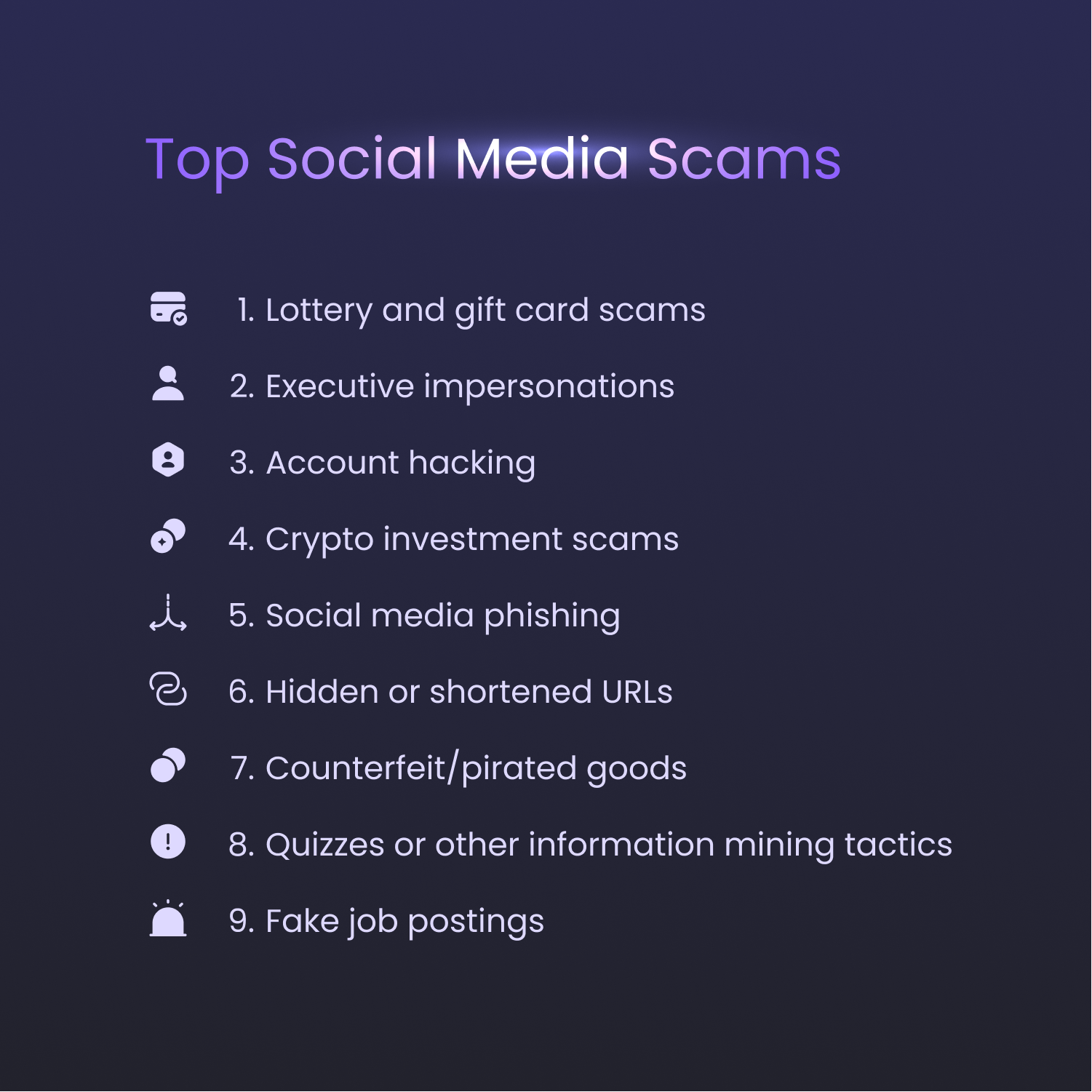
Here are some of the most popular scams that have fleeced social media users.
What are the Biggest Social Media Scams to Watch Out For?
1. Lottery and gift card scams
Lottery and gift card scams prey on people’s desire for money.
In a bid to make quick money, many unsuspecting victims end up taking the bait. These scams usually begin with unsolicited messages on social media claiming to give out gift cards for popular brands. The message will then most likely divert them to another page, where they’ll be asked to complete a basic task like forwarding the message to their friends. Sometimes they also ask for additional credentials to be filled out, which are then stolen.
Lottery scams also begin in the same manner. They either ask the people to send their account information to complete the transaction or transfer a small amount of money to cover transaction costs. Many victims lose thousands of dollars in the vain hope of landing a big prize in the end.
2. Executive impersonations
In a prime example of executive impersonations, Twitter handles pretending to be tech CEOs Elon Musk and Jeff Bezos sent out tweets asking for investments in a certain crypto account. Assuming the endorsement to be real, persuaded victims ended up transferring money to the criminals’ accounts.
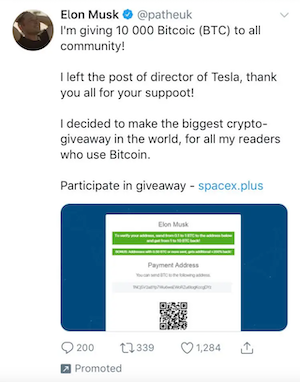
During an executive impersonation social media scam, the criminal first builds a fake profile mimicking a real person. Using the plethora of publicly available information, a fake account impersonating someone influential is created, using the real person’s pictures, personal information, and even speaking style and tone. Then this account is used to send out fake messages and posts to people asking for money, even targeting employees or business connections to the real individual that would be likely to respond.
3. Account hacking
This is one of the most popular social media scams.
Many data breaches expose millions of social media credentials for criminals to exploit. These credentials are used to get into people’s accounts, where hackers change the passwords and lock the actual owners out of the accounts.
Once hacked, the criminals then look to approach the user’s network and scam them, maybe asking for money or further compromising information.
4. Crypto investment scams
This is a new scam that has picked up steam with the popularity of many cryptocurrencies.
Preying on people’s culpability, scammers pose as investment experts and ask victims to transfer funds to their accounts. They promise to invest these funds in cryptocurrency and give them massive returns.
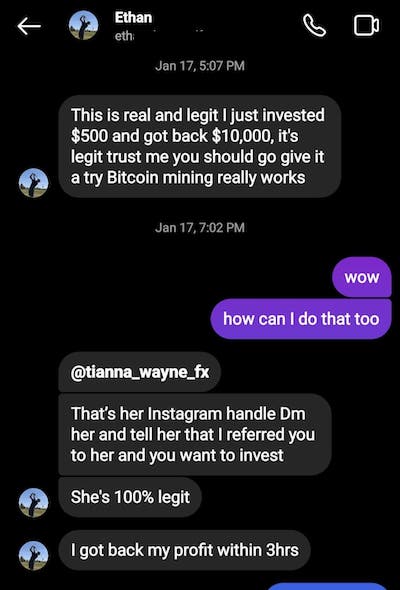
Due to the purported anonymity of blockchain, criminals are hard to track down. 37% of social media scam losses reported in 2021 were related to such investment scams.
5. Social media phishing
Social media phishing can occur in a variety of ways. Criminals have access to so many tactics and avenues of communication that it can be hard to nail down all of them targeting your employees or your organization.
In the most upfront sense, social media phishing is when fraudsters send you compelling messages that contain interesting information. But to access the information, you need to enter your personal details. These details are then stolen and used for other cybercrimes. These messages can be sent through a variety of social media sites, both on desktops and through mobile devices.
Several social media scams fall under this category. The gossip scam, healthcare scam, photo scam, account deleted scam, Nigerian prince scam, and stuck abroad scam are just a few common examples of social media phishing scams you’ve probably heard of.
6. Hidden or shortened URLs
Clicking on shortened URLs can lead to malicious websites if not checked properly.
Since these URLs do not show the full link, it’s hard to discern where it will take you after clicking. More often than not, it’ll be a nefarious site run by criminals that can either mine your data or download malware onto your device.
It’s advised to use a URL lengthening service before clicking on it to check where it leads.
—> Click this link. I dare you. <—
7. Counterfeit/pirated goods
According to the FTC, 45% of total loss reports in 2021 were related to online shopping scams.
These social media scams sell counterfeit or fake goods to unsuspecting consumers or take money upfront and never send goods. They cause massive reputational damage to brands, when interested customers purchase fraudulent goods that never come.
Posts and pages advertising such goods need to be identified and taken down as soon as possible.
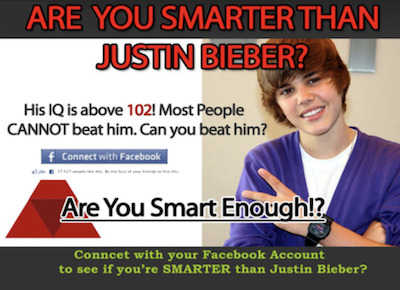
8. Quizzes and other information mining tactics
Data is one of the most sought-after commodities by cybercriminals.
From attractive quizzes, to enticing IQ tests, each one is set up to mine your data. Since these services are not chargeable, the value lies in the data they collect.
These quizzes have clickbait titles which make them a very compelling proposition. Once the developers of the quiz get the facts they need, they’ll sell it off on the dark web to other malicious actors.
9. Fake job postings
Another popular social media scam that businesses and users alike need to look out for are fake job postings. This is when hackers create fraudulent job postings on LinkedIn (or other professional networks) and convince people to apply. When you’re in the hiring process, the hackers will ask for personal identifiable information (PII) and other sensitive information (like your bank account info), which all would be normal to give a new employer. Once information is received, the unsuspecting victims will never hear from the fake company again.
Fake job posts hurt both individuals and organizations. Businesses that criminals are mimicking to set up fake jobs will face reputational damage from angry job hunters.
This type of social media scam has gained popularity in recent years thanks to the COVID-19 pandemic and related work force ebbs and flows. With more and more people looking for completely remote jobs, it’s become more common to not meet potential new employers in person before sharing sensitive data, which makes it easier for hackers to conduct these scams.
With more than half the population on social media, it’s a platform no self-serving business can overlook.
But as large a market social media is, it is an even larger nexus of scams, frauds, and cyber threats. It’s almost impossible to tackle manually. The scale, sophistication, and granularity of the threat actors are simply unmanageable by traditional SOC practices.
It requires a refreshed approach, backed by automation and machine learning.
Cybersecurity personnel can use automation to build workflows that scour these platforms daily, scanning every post, image, ad, and other content to detect fraud. It makes the discovery process automatic, leaving your team to tackle more cognitive security tasks.
The second layer is that of machine learning.
These advanced algorithms can analyze, detect, and mark suspicious activity. In fact, it can even be trained to identify many scams, including content abuse, counterfeit products, copyright infringement, and fake ads.
Run together, the entire discovery, detection, and resolution process can be automated and run 24/7, ensuring your customers remain safe from social media scams.
Bolster’s Social Media Protection Solution
Bolster provides a comprehensive AI-powered social media protection solution that enables organizations to remain vigilant across 14 social media platforms.
It automatically detects fraudulent activities, be it an organic post, paid ad, or fake executive profile, and removes it.
It can also remove malicious external links posted on social media, dismantle phishing and scam offers and take down impersonating profiles – all in just a few minutes.
Moreover, all the data and evidence it gathers is presented in an intuitive visual dashboard, making it easier for your security team to track all the activity.
If you want to learn more about how Bolster can help you protect your brand and its customers on social media with a combination of AI and ML, then book a demo today.









