Introduction
In a recent incident involving the NuGet, PyPI, and NPM packages, threat actors uploaded approximately 144,000 malicious packages to these open-source package repositories containing links to phishing and scam websites. These packages contain links to phishing and scam websites. These packages were part of a BlackHat SEO / SEO Poisoning campaign intended to manipulate search engine results and promote the ranking of the threat actors’ scam pages by creating backlinks from trusted websites.
In this blog post, we will explore the details of SEO Poisoning, analyze intent and provide guidance on protecting your organization from similar attacks.
What is SEO Poisoning?
Search engine poisoning (also known as “malicious search results”) is a technique used to inject spammy or malicious content into the search results of a search engine. One way this can be done is by creating backlinks from legitimate websites to malicious websites.
Backlinks are links from one website to another website. When a website has a lot of backlinks from other reputable websites, it can help improve its ranking in search engines. Search engines view backlinks as a sign of the website’s popularity and relevance.
Suppose a malicious actor creates backlinks from legitimate websites to malicious websites. In that case, it can trick search engines into thinking that the malicious website is more relevant or popular than it is. This can cause the malicious website to rank higher in the search results and potentially trick users into visiting it.
There are many different tactics that hackers use to build SEO poisoning attacks.
Here are a few examples:
Keyword stuffing
This involves loading a website with keywords to improve its ranking in search results. For example, a hacker may create a page filled with repetitive or irrelevant keywords to rank higher for those terms.
Hidden text or links
This involves using text or links hidden from the user but visible to search engines. Hackers may use this technique to manipulate search engine rankings or redirect users to malicious sites.
Cloaking
This involves showing different content to search engines and users. Hackers may use cloaking to trick search engines into ranking their sites higher or redirect users to malicious sites.
Spam emails
Hackers may send spam emails containing links to malicious sites or encourage users to download malicious software.
Social media posts
Hackers may use social media to spread links to malicious sites or to trick users into clicking on links that lead to malicious sites. Protect your social media with Bolster.
Malvertising
Involves using a fake ad to spread malicious links and redirect users to malicious sites. Hackers may use malvertising to infect users’ computers with malware or steal sensitive information.
There have been many instances of real-life SEO poisoning attacks in the past. For example, in 2011, hackers used SEO poisoning to redirect users who searched for terms related to the Japanese earthquake and tsunami to malicious sites that contained malware. In 2013, hackers used SEO poisoning to redirect users who searched for terms related to the Boston Marathon bombings to malicious sites that had malware. And in 2014, hackers used SEO poisoning to redirect users who searched for terms related to the Ebola virus to malicious sites that contained malware.
What is the process and end goal of SEO poisoning?
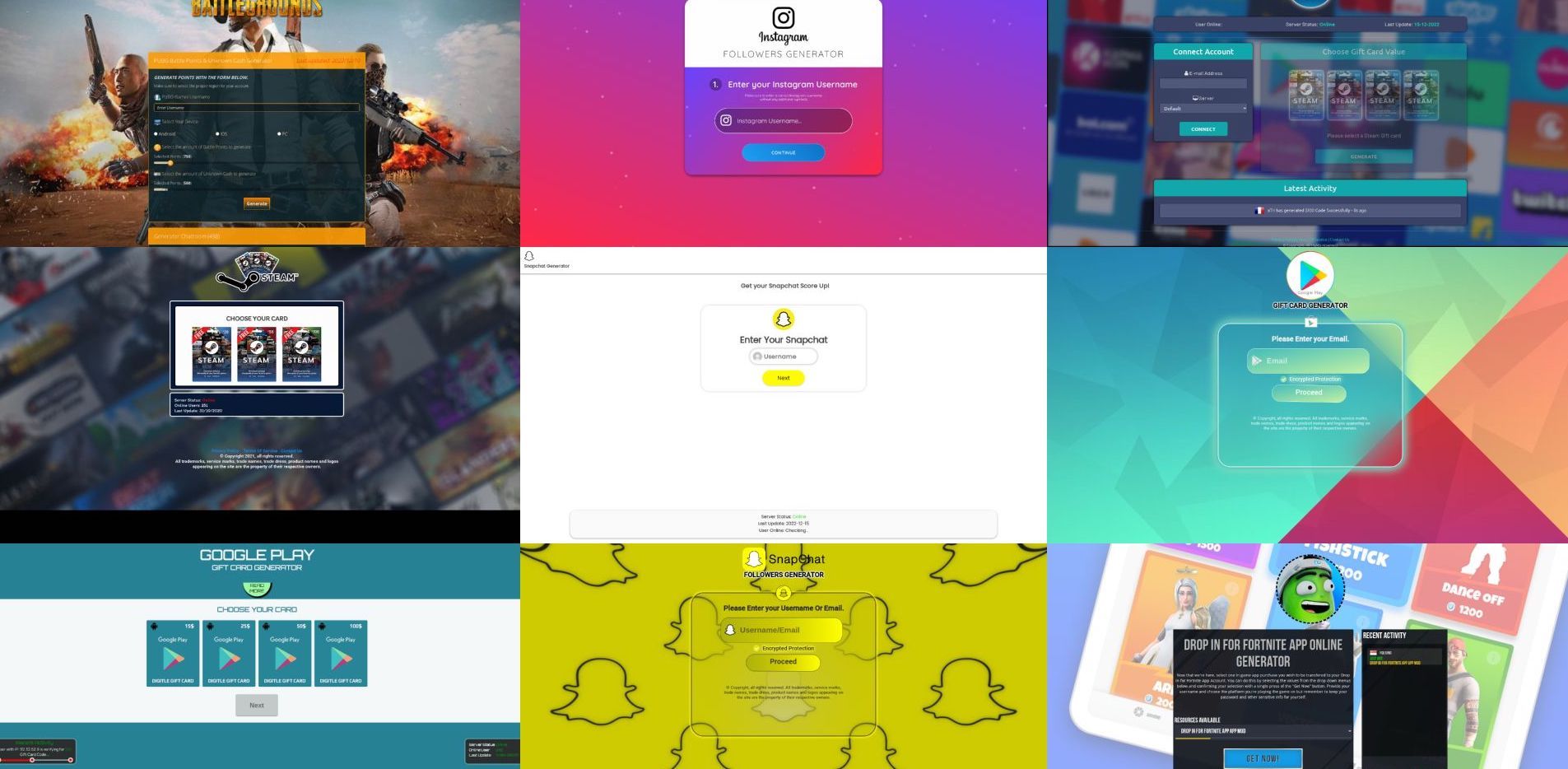
In this recent SEO poisoning attack, the threat actor used NuGet packages with phishing links and keywords to target brands in the description file of the malicious package. Threat actors posted over 136k malicious packages, targeting different video games, brands, and gift card stores. The intent of this campaign appeared to be to rank their phishing websites higher in search results when somebody searches for gift cards or hacks for the games/brand.
For example, if a user searches for hacks/cheat methods for their favorite video games on Google or searches “gain followers on Instagram.” Because of search poisoning in this campaign, they’d be shown the threat actor-controlled websites at the top of the search results.
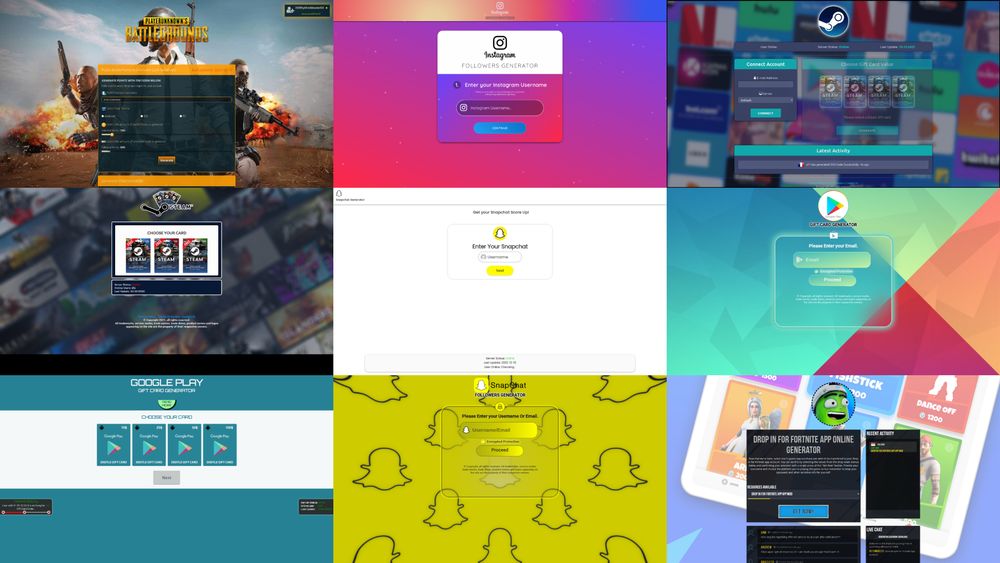
Here’s an example of what the process may look like:
- Threat actor-controlled website asks users to enter their username to claim gift card/game points or followers.
- A fake processing message or other technical jumbo mumbo appears to establish that something is happening.
- After some wait, they ask you to complete a survey/task. In our case, it was to install a browser and complete a survey for a Walmart gift card. Using this technique, threat actors drive traffic to survey websites and earn a commission on each completed survey/task.
- User, hoping to gain some in-game currency/ social media followers, completes these tasks without realizing that it is a fake operation. Others have reported that these websites are also redirecting to affiliate links of AliExpress and other e-commerce sites.
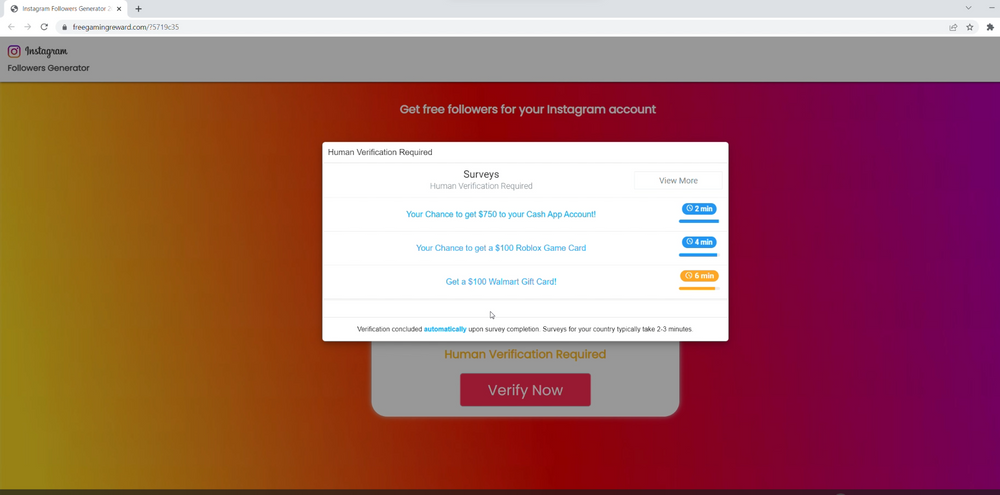
This type of campaign primarily targets a younger audience of less tech-savvy folks who may believe the promise of free followers, in-game currency, or gift cards at face value. Young folks looking for ways to cheat in games may be more likely to click on these links.
How to protect against SEO poisoning attacks
For Brands
- Proactively monitoring search engines for keywords related to your brand will help you become aware of such campaigns in the early stages.
- Monitoring new domain registrations with your brand name and keywords associated with your brand.
- Requesting takedowns on malicious websites that abuse your brand logo and name in phishing & scam campaigns. Learn more about Bolster’s Phishing & Scam solution.
For Individual Users
- Nobody offers free followers, gift cards, and in-game currencies.
- Do not enter your confidential information on such websites. This will lead to your accounts being hijacked & abused by threat actors and possibly sold on dark web markets.
- Utilize free community tools like checkphish.ai that can detect phishing & fraud websites in a safe sandbox environment.
Campaigns like this have been around for ages and will continue to happen in the future. NuGet package abuse was just one of the mediums that threat actors used as part of their Black Hat SEO techniques to poison search engine results. To neutralize such campaigns early and protect your brand and customers, proactive monitoring of your brand mentions, domain registration, and dark web monitoring is critical.
If you’re trying to monitor & protect your brand from such campaigns, get a demo of Bolster here.