Ensuring the security and protection of your business in today’s interconnected world should be a top priority. The dark web is an area that often gets overlooked. It’s important for businesses to understand how to navigate this hidden realm and leverage dark web monitoring to safeguard their valuable assets. In this blog post, we will explore key strategies and techniques for protecting your business on the dark web.
For a deeper dive into the world of dark web monitoring, download our free Guide to Dark Web Monitoring today.
What is the Dark Web?
The dark web, often shrouded in mystery, is a hidden part of the internet that is not indexed by search engines. Unlike the surface web, where most of our online activities take place, the dark web is intentionally designed to provide anonymity and privacy to users. It consists of encrypted networks that require special software, such as Tor, to access.
Within the dark web, individuals and groups can engage in illicit activities, including the buying and selling of stolen data, illegal goods, and even the planning of cybercrimes. It is essential for businesses to understand the dark web and its potential risks, as it poses a significant threat to their cybersecurity and sensitive information.
The How to: Accessing the Dark Web
Accessing the dark web requires special software, such as Tor, which enables anonymous browsing. By following certain privacy measures and employing a secure setup, individuals (and businesses) can safely access the dark web.
The first step is to set up the Tor browser and configure it for maximum privacy. This includes disabling any browser extensions, clearing cookies and cache and using a VPN.
Once set up, businesses can access the dark web by typing the “.onion” URL of the website they wish to access into the Tor browser. Since the Dark Web is unindexed, search engines will not be useful for finding specific websites, which is why businesses should bookmark websites they wish to monitor.
Discovering What Exposed Business Data is on the Dark Web
The dark web contains a vast trove of business-critical information, including stolen executive account details, compromised credentials, and sensitive business financial data like credit card numbers.
There are a multitude of options for monitoring for your business-critical data on the dark web.
Crawlers
Businesses can use a technique known as “crawling.”, which involves using specialized software to navigate and search for data across various websites on the dark web.
Crawlers can scan regular web pages as well as TOR hidden services that are not indexed in search engines. Crawling various marketplaces on the dark web can help businesses identify if their information is being traded or exposed.
Crawlers can collect and collate data from multiple dark web marketplaces, monitor for specific data types such as credit card details, and even plot their detection in real time. Scrapers can be used to automate the task of searching for specific data types or keyword mentions on the dark web. By using open-source tools, businesses can set up a low-cost but effective dark web monitoring system.
Monitoring dark web forums
From cybercriminal forums to trading networks, the dark web is a breeding ground for various threats. To detect potential threats to their operations, businesses should explore the different dark web forums where cybercriminals communicate and interact with each other.
You can monitor for mentions of their brand, executives, employee emails, and products on such forums.
The dark web is also home to various malware and hacking services, which businesses can explore to get a sense of how hackers may be targeting their industry or sector. Other threats that can be explored through dark web chatter include phishing scams, ransomware attacks, and social engineering.
Seeking Actionable Intelligence on the Dark Web
To obtain actionable intelligence from the dark web that your business can use to protect critical data requires a strategic approach. Once businesses gather the data, it’s important to filter and analyze the information gathered. This ensures the businesses can hone in on relevant and actionable insights.
For example, positive mentions of the brand should be noted, while negative mentions should be flagged for further action. It can be overwhelming to weed through the vast amounts of data collected from dark web scans, making taking action and remediating the truly business-critical threats difficult even with a proper scanning tool in place.
It’s important for your business to not only have your eye on dark web chatter, but also have the proper tools in place for sorting through dark web data and highlighting which risks are critical to your business, which risks might indicate future threats are mounting, and which threats can be ignored.
See what the top 10 biggest threats are to monitor for on the dark web with our Dark Web Monitoring Checklist.
Overcoming Challenges in Dark Web Monitoring
Monitoring the dark web comes with its fair share of challenges. One of the issues is the sheer volume of data that is present on the dark web. To tackle this problem, businesses can use automated monitoring and alert systems, which can flag potential threats and data breaches.
Another challenge is understanding the context of the data that is being mined. Businesses should contextualize data in terms of its source, content, and relevance to their operations to take appropriate actions. With a complete look at how threat actors may be targeting your business not only on the dark web, but across additional avenues like social media or app stores, you can better contextualize dark web data and prioritize risk remediation.
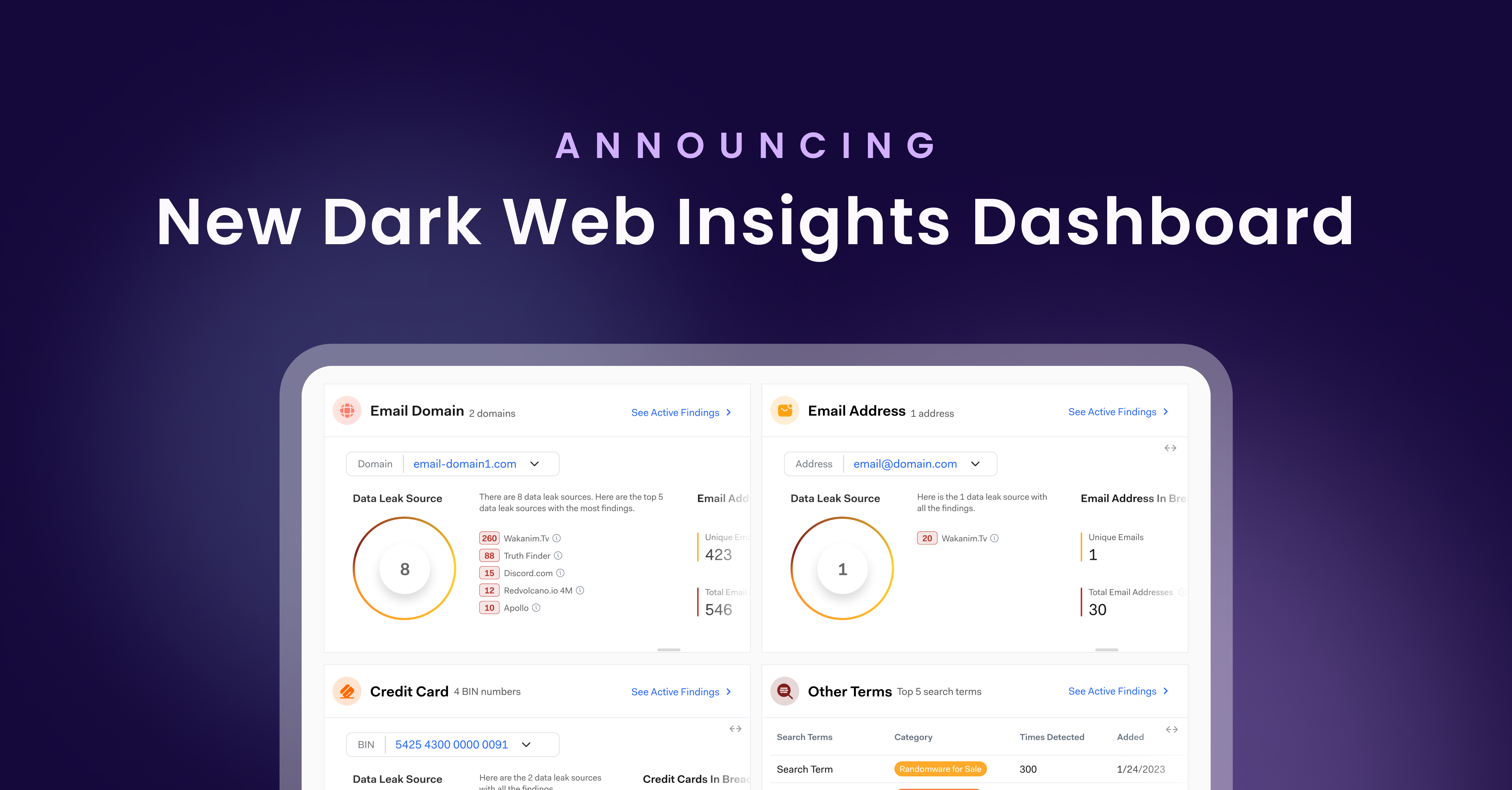
Monitoring the Dark Web: Bolster’s Customer-First Solution
Protecting your business on the dark web is crucial to maintaining a strong cybersecurity posture. Bolster’s Dark Web Monitoring solution and Insights Dashboard offers an actionable solution to monitoring and remediating dark web threats.
Bolster provides a fast-track view to achieve quick visibility and remediation of login credential threats originating on the dark web. By gathering dark web data from a multitude of sources, and organizing it in one cohesive and customizable dashboard, your team can quickly identify dark web threats that are critical to your business, and take action to remediate them immediately.
For more information on the dark web threat landscape, download our Guide to the Dark Web.
Request a demo with the Bolster team today to see how you can protect your business on the dark web.