According to research by the Aite Group, financial institutions are facing a 64% uptick in account takeover attacks than before the pandemic. This number is expected to rise further as the digital ecosystem expands, enlarging the surface area culpable to attack.
Account takeover fraud is one of the most common fraud types, and institutions must be vigilant against it. This article will discuss account takeover fraud, its types, and five ways to protect your business.
Let’s dive in.
What is Account Takeover Fraud?
Account takeover fraud is an attack where hackers compromise a victim’s account using stolen credentials. In this attack, fraudsters can use a variety of tactics to gain illegitimate access to user credentials.
From simpler credential stuffing and phishing scams to much more nuanced spear phishing and Man-in-the-middle attacks, fraudsters have become coordinated, sophisticated, and modern in their approach.
The banking industry is the most commonly attacked industry under the onslaught, followed by other financial institutions. Some hackers also use account takeover to hack into Spotify, Google, Netflix, and other accounts that potentially contain banking information.
What are the Methods Commonly Used in Account Takeover Fraud?
Phishing
According to the Verizon 2021 Data Breach Report, over 85% of data breaches involved the weakest link of the cybersecurity chain, humans.
Simple social engineering and spoofing can compel unsuspecting users to cough up their credentials. 52% of the organizations affected by phishing attacks and account takeover fraud lost credentials and account data.
While 96% of social attacks occur over email, text messages, and social media are also commonly used vectors. Attackers use techniques to gain user confidence or fool them into giving up details.
Some phishing attacks also install malware onto the computer to track keystrokes and steal login data. Once credentials are stolen, the hacker can gain illegitimate access to the account.
Credential stuffing
This is another popular account takeover fraud technique that has seen a rise due to Covid-19. Hackers generally buy off stolen usernames, passwords, and other credentials from the dark web. These passwords could have been leaked during any of the hundreds of data breaches that have occurred in the last few years. Then, using automated bots, the attacker keeps stuffing the stolen credentials into the target site until it hits the right ones.
Another method that comes under this category is called credential cracking. In this case, only the usernames are available. The hacker works under the assumption that most people use simple passwords and, using a brute force attack, seeks to crack that password.
Another issue connected to this category is that almost 72% of people reuse the same passwords for four or more accounts. If even one account is lost to hackers, they can use the same credentials to take over several other similar accounts.
Sim card swapping
Although old-fashioned, fraudsters regularly use this account takeover fraud method to overcome 2FA methods such as OTPs. Using social engineering, the cybercriminal can get a genuine user’s number ported to an illegal sim. Once this sim is switched on, they can use it to activate the user’s banking app on the phone.
The fraudster can also receive OTPs and other details once the number is ported. Once access is gained, they can transfer funds, add payees, and change login details, amongst other banking operations.
Malware
With more than a billion malware programs, users and companies are bombarded with malware every second. It isn’t uncommon for an unsuspecting user or employee to fall prey and become a victim of account takeover fraud.
Malware can either be delivered as a malicious attachment via mail or infected applications downloaded from suspicious sources.
It can be as covert as downloading a legitimate-looking update that turns out to be malicious. What makes it worse is that most malware remains hidden for months before getting caught. By then, they could’ve stolen tons of data and passwords, putting every user account at risk.
Mobile banking trojans
Nearly 58% of all computer malware can be attributed to trojans. One of the more common trojans layers a fake screen on top of a legitimate application. When an unaware user inputs credentials, the banking processes continue in the background, but the details get swiped from the fake screen.
Trojans can also modify transactional data and redirect funds to fraudulent accounts even if the user enters the correct information.
Man-in-the-middle attacks
Coinciding with the rise in remote work uptake and smartphone usage is the number of MitM attacks. MitM attacks occur when attackers position themselves between the user and the legitimate application without being caught.
In this scenario, the attacker can monitor the traffic on the device and steal credentials, data, and user history. One of the most common methods is setting up a public WiFi hotspot and waiting for unwary users to use it. They can sit in a remote location and monitor all the activity.
Steps You Can Take to Protect Your Customers From Account Takeover Fraud
With account takeover fraud methods only growing more and more sophisticated with the further adaption and reliance on technology, it’s important to know what your options are to best protect your business.
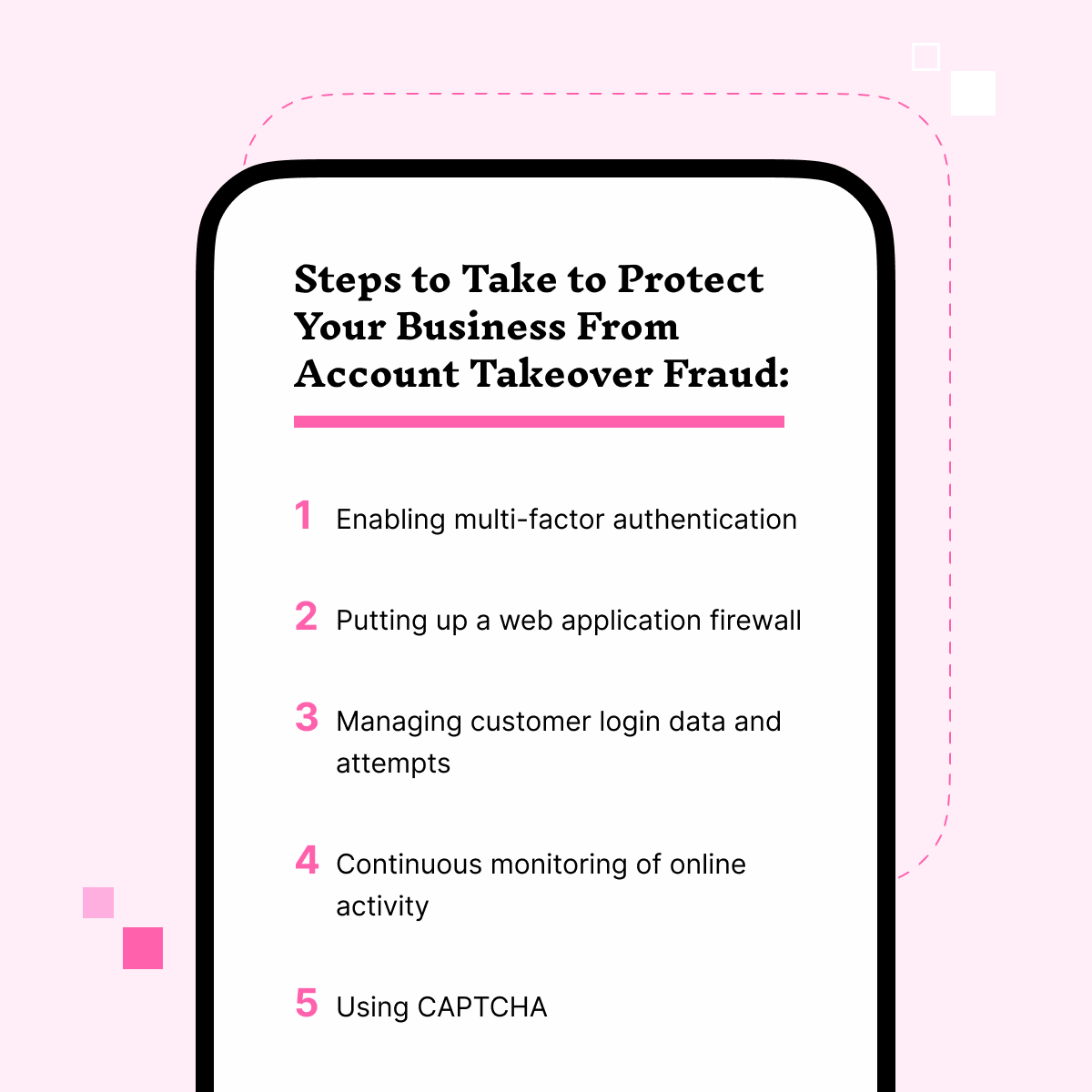
Enabling multi-factor authentication
Advanced social engineering scams and phishing attacks have made ‘strong’ passwords obsolete. This issue gets compounded when you realize that 69% of people admitted to sharing their passwords with colleagues.
Organizations need to add another layer of security on top of passwords to secure customer accounts. This is where multi-factor authentication, or MFA, comes in. When deployed as part of a scalable Customer Identity and Access Management (CIAM), MFA can provide a frictionless yet secure customer experience.
As opposed to using just one form of proof of identity, MFA draws from multiple PoI categories. There are three broad categories.
- Knowledge – This refers to something the customer knows, including authentication forms such as passwords, PINs, and security questions.
- Possession – This refers to something that the customer possesses. It includes soft tokens, such as OTPs sent to emails and phones, and hard tokens such as USB devices and key fobs.
- Biometric – This refers to different forms of biological expressions of your customers, such as fingerprints, retina scans, facial scans, and voice recognition.
Few cybercriminals can fabricate all three forms of authentication, keeping them locked out of accounts secured with MFA. MFA is one of the best ways to protect against account takeover fraud.
Putting up a web application firewall
A Web Application Firewall or WAF is a protective layer around web applications to keep malicious traffic from infiltrating. It filters HTTP traffic by monitoring and identifying potential ATO attacks and mitigating them. It can do this in multiple ways.
- It identifies and blocks access requests from known attackers.
- It detects malicious bot activity deployed during ATO attacks.
- It identifies credential stuffing attacks and stops them.
- It detects and blocks brute force attacks by identifying sessions with an unusual number of login attempts.
- It enables MFA or third-party authentication to deter attackers.
- It scans traffic for any indicators of credential stuffing tools.
Managing customer login data and attempts
Over 86% of users have experienced some sort of phishing attack at work. And with billions of credentials being leaked online by hackers, managing customer login data effectively is key to protecting them from ATO attacks.
- Using customer analytics, organizations need to cross-reference login data for specific devices, browsers, and IP addresses with the existing customer data. Their behavior data, i.e., orders, payment methods, transactions, and locations, can be checked. This gives firms an upper hand in recognizing anomalies.
- Every time a new user signs up, their login data can be checked against a breached credentials database. If they are signing up with compromised credentials, they can be stopped and warned. Old users can also be alerted if their login information is on the breached credentials database.
- Every time a customer tries to change their credentials, make it a point to make them go through a frictionless MFA funnel to confirm their identity.
- Lastly, contact users and inform them of any new activity on their accounts, even if it was only approved after MFA. This way, the user can still salvage their account after it’s been taken over.
Continuous monitoring of online activity
Advances in AI and ML have enabled organizations to monitor customer activity on their portals continuously. ML algorithms build a normative customer profile of their usual online journey across devices and accounts by watching and learning continuously.
These intelligent systems analyze new devices, cookies, headers, referrers, and locations. Any tangent away from normal user behavior is flagged down for further inspection. Most of these processes occur in real time.
This proactive approach ensures the machine can decide quickly whether the suspicious activity is an attack or a genuine customer trying to change details.
Moreover, continuous monitoring can easily be integrated with other protection systems, such as MFA and dynamic linking.
Using CAPTCHA
Lastly, organizations can curtail the number of login attempts on the portal within a reasonable number. This number can be decided based on customer analytics data and operational business requirements.
Even the use of proxies can be limited to targeting the issue of account takeover specifically. After several attempts, organizations can try displaying an authentication test if setting such a limit seems like an unnecessary friction point for the customer.
The most popular authentication method is CAPTCHA, a puzzle to curb ATO bots from gaining access to an account. Captcha can be quite an effective strategy against account takeover fraud.
While keeping users secured is essential, keeping the entire customer experience as frictionless as possible, lest they migrate to your competition, is vital.
This requires implementing an elaborate account takeover protection solution such as the one provided by Bolster. It uses URL scanning and threat intelligence to prevent real-time ATO attacks.
Apart from identifying and alerting compromised users, it also detects and blocks phishing sites automatically within just a few minutes. Its zero-touch takedown process and easy integration with underlying systems make it a top choice for vigilant proactive organizations.
About Us
Bolster is the only automated digital risk protection platform in the world that detects, analyses, and takes down fraudulent sites and content across the web, social media, app stores, marketplaces, and the dark web.
Interested in learning more about Bolster’s solutions? Request a demo here.