Name brand postal services have been increasingly targeted by phishing campaigns. We previously published a blog post surrounding one of these scams, specifically a USPS phishing campaign.
Bolster Research Labs recently discovered a phishing kit that impersonates Qatar Post, a national provider of postal services in Qatar. This phishing kit is available for free in cybercrime marketplaces. The phishing kit is sophisticated, and can evade detection by blocking various bots, security vendor IP addresses, and user-agents. In this blog, we will discuss its capabilities in detail.
Acquiring the Phishing Kit
While researching cybercrime marketplaces, the Research Team discovered numerous phishing kits designed to impersonate most postal service organizations globally. The Qatar Post phishing kit was posted recently[Jan29,2024] and shared for free in one of the marketplaces.

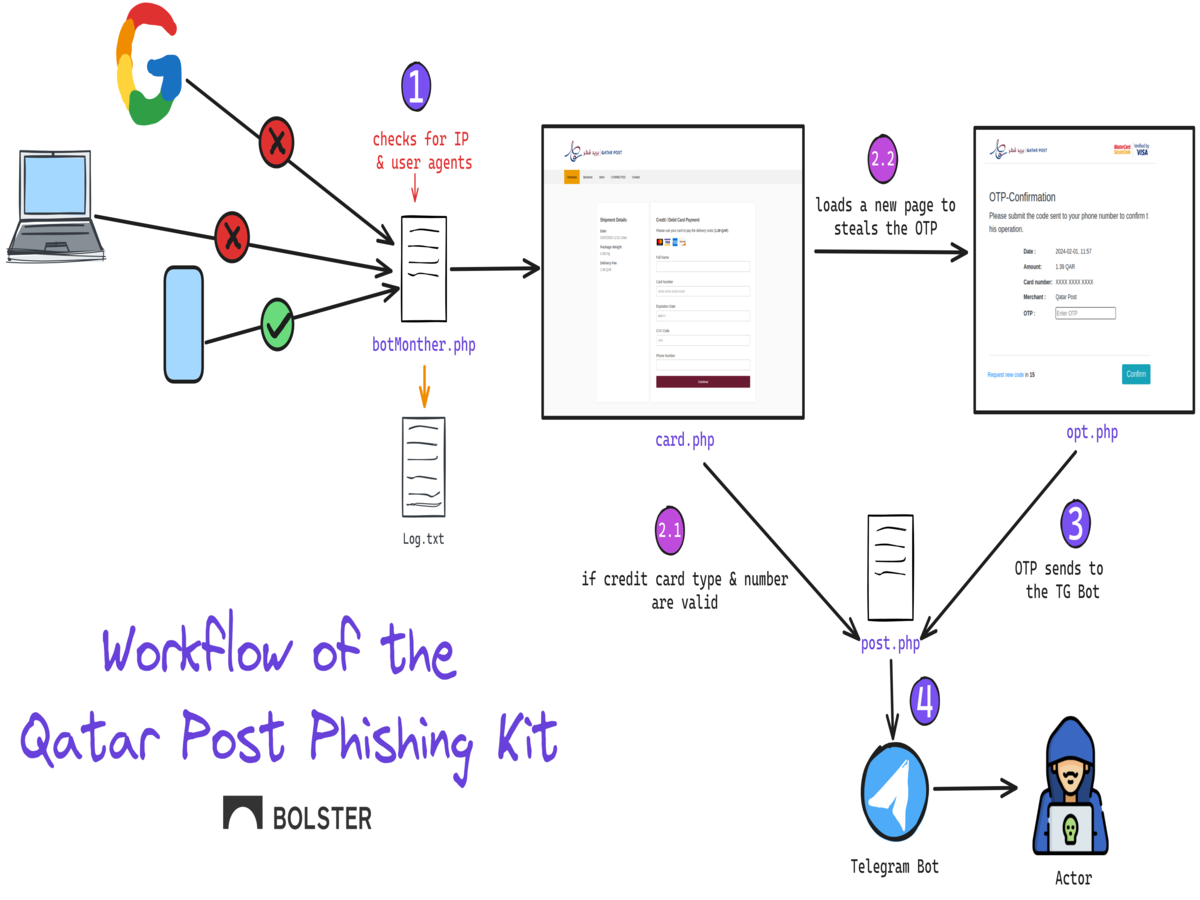
Workflow of the Phishing Kit
Websites created using this phishing kit always check the visitor’s IP address and user agent before displaying the phishing content. When submitting the credit card details, it validates the credit card type and number before sending via TG bot.

Phishing Kit Analysis
The phishing kit involved in the Qatar Post campaign is written in PHP, JS, and, interestingly, the improvised version of previous phishing kits the Bolster Research Team analyzed. Some enhancements to the phishing kit incorporate blocking security vendors’ IP addresses and desktop user agents to validate card numbers using Luhn Algorithms.


Credit card validation
While looking into its source code, the phishing kit not only validated the entered credit card types using the validateCreditCard() function [Fig2], but also checked for credit card number length using Luhn’s algorithm [Fig3], which determines whether or not a credit card number is valid, making it less spammy while stealing credit card information.


Evasion techniques
This phishing site can block users based on user agents, IPs, and IP ranges to get less unwanted traffic [Fig4].

Also, it can redirect to google.com using the killBot() function [Fig5] based on the user’s IP location. These capabilities help phishing sites stay undetected by most AI detection engines.



Exfiltrating credit card information
Like other sophisticated phishing kits, this phishing kit also uses a telegram bot to steal the credit card information and the OTP. [Fig7]. Among actors, stealing PIIs is a more popular technique to avoid detection and works as a zero-investment infrastructure.

Indication of future development
While reviewing the source code of the phishing kit, we found an interesting function named isValidKey(). This discovery suggests that the phishing kit’s creator intends to improve this version. However, it remains unclear which specific key the actor intends to validate.

Conclusion: Protecting Your Business From Phishing Attacks
With similar sophisticated phishing kits, we expect more phishing sites to be created targeting the courier and logistics industry. Vigilance and proactive detection practices are crucial for organizations and individuals to protect against these threats. Continued monitoring and analysis of such threats are essential to staying ahead of cybercriminals and maintaining the security of postal services and their customers.
Bolster AI helps protect businesses from phishing attacks and scam sites with our trained LLM’s. By detecting and taking down even the most sophisticated attacks, you can trust Bolster to protect your consumers from hackers as techniques continue to evolve. Request a demo with us today.