Bolster’s threat research team recently uncovered a widespread brand impersonation scam campaign targeting 100+ popular clothing, footwear, and apparel brands. Among the notable brands affected by this campaign are Nike, Puma, Adidas, Casio, Crocs, Sketchers, Caterpillar, New Balance, Fila, Vans, and numerous others. This campaign came live around June 2022 and had peak phishing activity between November 2022 and February 2023.
To carry out their scam activities, threat actors have registered thousands of domains with the intention of targeting unsuspecting customers of these brands for their own financial gain.
The Scale of This Brand Impersonation Campaign
Our investigation revealed an extensive network of brand impersonation scam sites, with over 3,000+ live domains identified.
These fraudulent websites target more than 100+ popular clothing, footwear, and apparel brands. When considering all the domains that are now inactive but were part of this campaign, the number of brand impersonation domains exceeds 6,000.
The list of affected brands is substantial, encompassing over 80 well-known names. Notably, major brands such as Nike, Puma, Clarks, and others have faced the brunt of this campaign, with at least 10+ live sites impersonating each brand.
Brands impacted by this campaign
Below is a sample list of the brands our Bolster team has identified as being targeted by this campaign:
- Clarks
- Kipling Bags
- Superga
- Arc’teryx
- Vivobarefoot Shoes
- Wolverine Shoes
- Hoka Shoes
- Tommy Hilfigher
- NVGTN
- Palladium Shoes
- Mephisto
- Etnies
- Keen Footwear
- Lowa Boots
- Kate Spade
- Rieker
- Salomon
- The North Face
- FitFlop
- NoBull Shoes
- Fossil
- Guess
- Demonia
- Veja Shoes
- Gola Sneakers
- UGG
- Young LA
- Vibram
- Sketchers
- Columbia Sportswear
- Danner Boots
- Saunk
- New Balance
- Russell and Bromley
- O’NEILL Sportswear
- C&A Clothes
- Timberland Shoes
- Caterpillar
- Rocky Boots
- Toms Shoes
- Reebok
- Desigual
- Mizuno
- aigle
- Native Shoes
- Casio
- Asics
- lora Jewel
- Nine West
- Puma
- AYBL
- Groundies Shoes
- Converse
- La Sportiva
- Tretorn
- Salewa
- On running
- Kenneth Cole Shoes
- Be Lenka
- Nike
- Vans
- Muck Boots
- Bo+Tee
- Teva Slippers
- PANDORA Jewelwers
- Irish Setter Boots
- fjallraven
- SuperDry
- Doc Martens
- Miu Miu
- Ariat
- AllBirds
- Kappa
- Melissa
- Inov-8
- New Era Cap
- Fila
- Etsy
- Alphalete
Origin of Phishing Infrastructure Behind the Campaign
The campaign domains associated with this scam have been traced back to the autonomous system number AS48950.
These domains’ IP addresses are hosted by two specific internet service providers, Packet Exchange Limited and Global Colocation Limited. It is worth noting that both providers have a negative reputation for fraud risk.
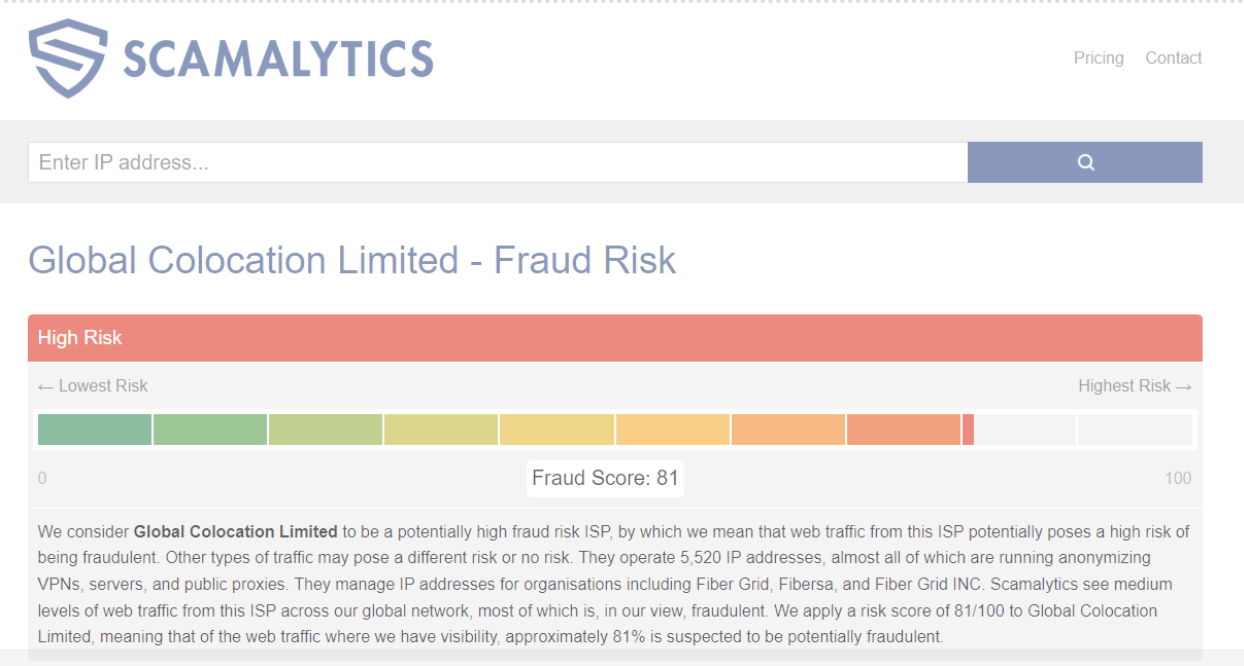
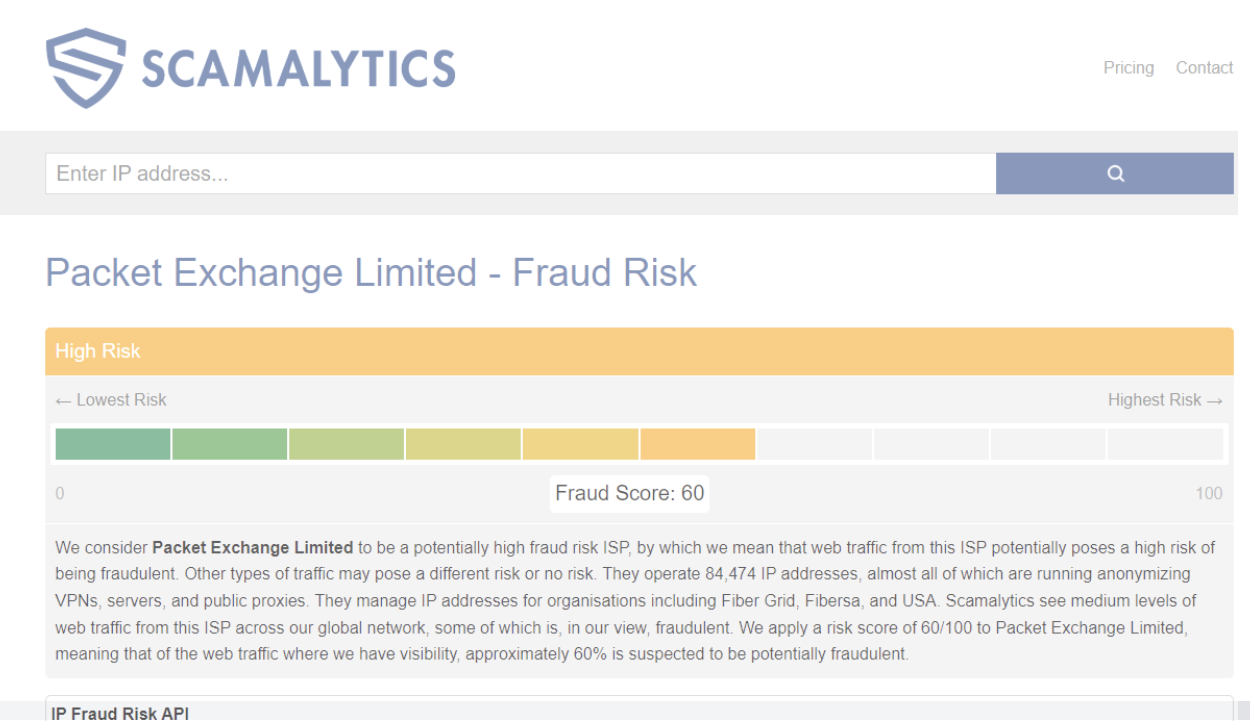
Additionally, most of these domains (almost 1500) are registered with the domain registrar ALIBABA.COM SINGAPORE E-COMMERCE PRIVATE LIMITED. The age of the domains in this campaign vary, with some being approximately two years old, while a significant number having been registered within the past 90 days.
In their attempts to deceive, the attackers predominantly utilize a pattern of combining the brand name with a random country name, followed by a generic top-level domain (TLD). See the example below of domains we found targeting Puma:
- puma-shoes-singapore.com
- pumaenmexico.com.mx
- bestpumaindia.in
- puma-italia.com
- pumashoesaustralia.org
- pumaoutletsingapore.com
- pumacheapuk.com
- pumashoes-singapore.com
- puma-south-africa.co.za
- pumashoesirelandie.com
- pumashoesindia.co.in
- pumaoutletspain.es
- pumafactoryoutletuk.com
- puma4romania.com
- pumaonlineshopdeutschland.com
- pumaslovensko.sk
- pumasalesingapore.com
- puma-india.co.in
- pumasneakers.co.in
- pumastoremexico.com
- pumacroatia.com.hr
- pumaoutletindia.com
- pumasingaporeoutlet.com
- pumaoutletgreece.com
- pumahungary.org
- pumashoeireland.com
- pumaifactoryturkey.com
- pumamexicomx.com
- pumaoutletnorge.com
- pumaparamexico.com
- pumacroatia.com
- puma-barcelona.com
- pumagreece.gr
- pumasaleonlineindia.in
- pumashoes-uksale.com
How Long Has This Brand Impersonation Campaign Been Running?
The Bolster threat research team first observed a live site from this campaign in our system in June 2022. Upon more investigation, the team has found that the oldest registered domain in this campaign was registered back in 2020, but was not live until 2 years later.
The initial big spike (100+ increase in activity) of activity was observed in January 2022. Subsequently, another big spike was detected in January 2023 and February 2023, with a 300+ increase in fake sites observed in each month.
While there is some difficulty estimating the exact number of sites because the domains would go back and fourth between being active and inactive every month, the team estimates that the peak campaign activity happened between November 2022 and Feb 2023, during the holiday season.
While the current attack level is not as prominent as it was during the holiday season, the research team is still monitoring for and detecting substantial activity from this brand impersonation campaign. Currently, there are still about 2200-2300 live domains from this campaign (during the week of May 22-26, 2023). If we include the inactive domains, there are about 5000 – 6000 domains still associated with this scam campaign.
Squatting in the Top Position of Google Search Results
Several of these brand impersonation scam sites have managed to exist for a considerable period of time, to the extent that when users search for the brand name, these impersonation sites appear as the second or third result on popular search engines like Google.
This is a unique strategy that attackers are leveraging to dupe unsuspecting users. Attackers are employing various search engine optimization (SEO) techniques to manipulate search engine rankings and increase visibility. This attack seems meticulously planned as the domains were registered two years in advanced, allowing for aged domains that in some cases greatly increases their rank to the second or third result in Google search for many brand-related keywords. Here’s an example of this with Clarks:
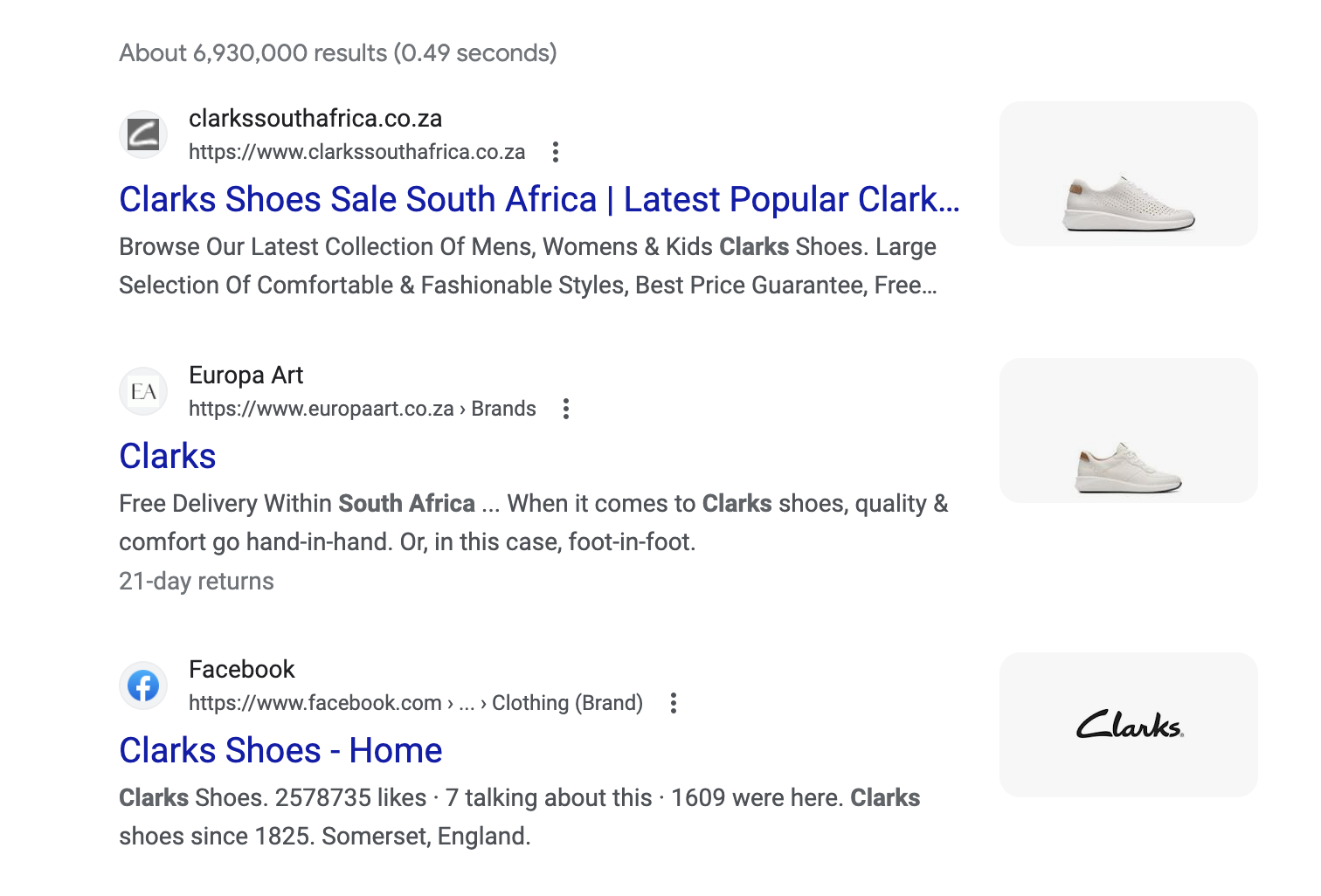
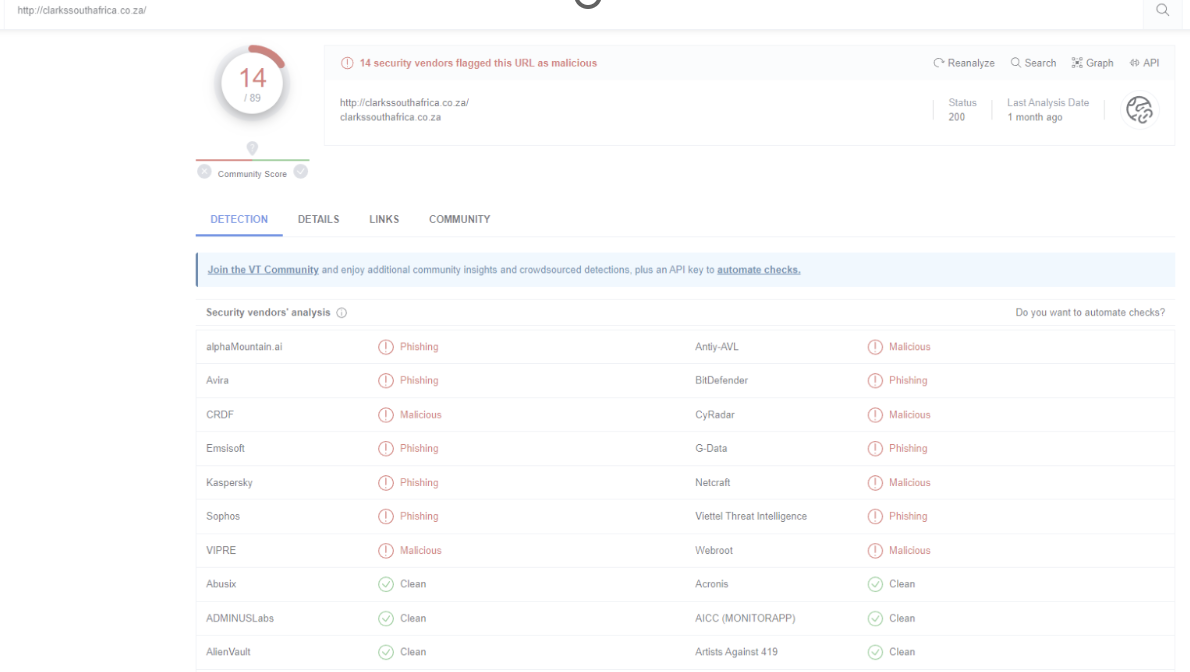
The implications of these deceptive sites ranking high in search engine results are particularly concerning for non-tech-savvy users. Such individuals may be at a greater risk of falling victim to these scams since they might trust the search engine results and assume the fraudulent sites to be legitimate.
What are the Attackers’ Motivation?
Motivated by financial gain, these scammers exploit the trust associated with reputable brands to trick unsuspecting shoppers into making purchases on their fraudulent websites. Instead of delivering the promised products, they either never send anything or ship low-quality knockoffs sourced from Chinese marketplaces.
Customers who overlook the fact that these websites are not official brand sites often end up falling into the trap. They enter their email, password, and credit card details, unknowingly compromising their personal information as well. To make matters worse, some of these impersonation websites manage to rank high in search engine results, making it easier for victims to unwittingly stumble upon them and considering them legitimate.
Use of same domain registrar, combination of the same two ISPs, and similar typosquat domain name registration pattern leads us to believe that same group of threat actors is behind all of these scam and brand impersonation sites.
How to Avoid Getting Scammed by Typosquat Sites
This scam campaign highlights the importance of awareness and caution while browsing and making online purchases. Users should exercise diligence in verifying the authenticity of websites, especially when dealing with popular brands, to minimize the risk of being misled by these impersonation scam websites.
Ensure that you are on an official brand website by confirming the original brand’s domain. Keep an eye out for any signs of a suspicious domain names.
If you come across a deal or product price that seems too good to be true, you should take extra steps to verify the legitimacy of the domain.
It’s also critical for business to protect their digital assets from brand impersonation attacks to prevent damaging their brand reputation. If customers (or employees, partners, and others in your network) fall victim to a scam pretending to be your organization, it can turn them off from purchasing from you in the future, as well as create bad reviews, bad press, and bad word of mouth.
Bolster provides comprehensive digital risk protection services to detect and take down phishing scams and brand impersonations in real-time. We also offer search engine brand monitoring services, keeping a close watch on search engine results to identify websites impersonating your brand.
Contact us here for more information on how to protect against the ongoing brand scams.





