
Unlimited Auto-Takedowns for Phishing and Scams
Automated takedowns of malicious websites, social impersonations, scam ads, rogue apps leveraging APIs and Large Language Models (LLMs) to offer unparalleled speed and security.
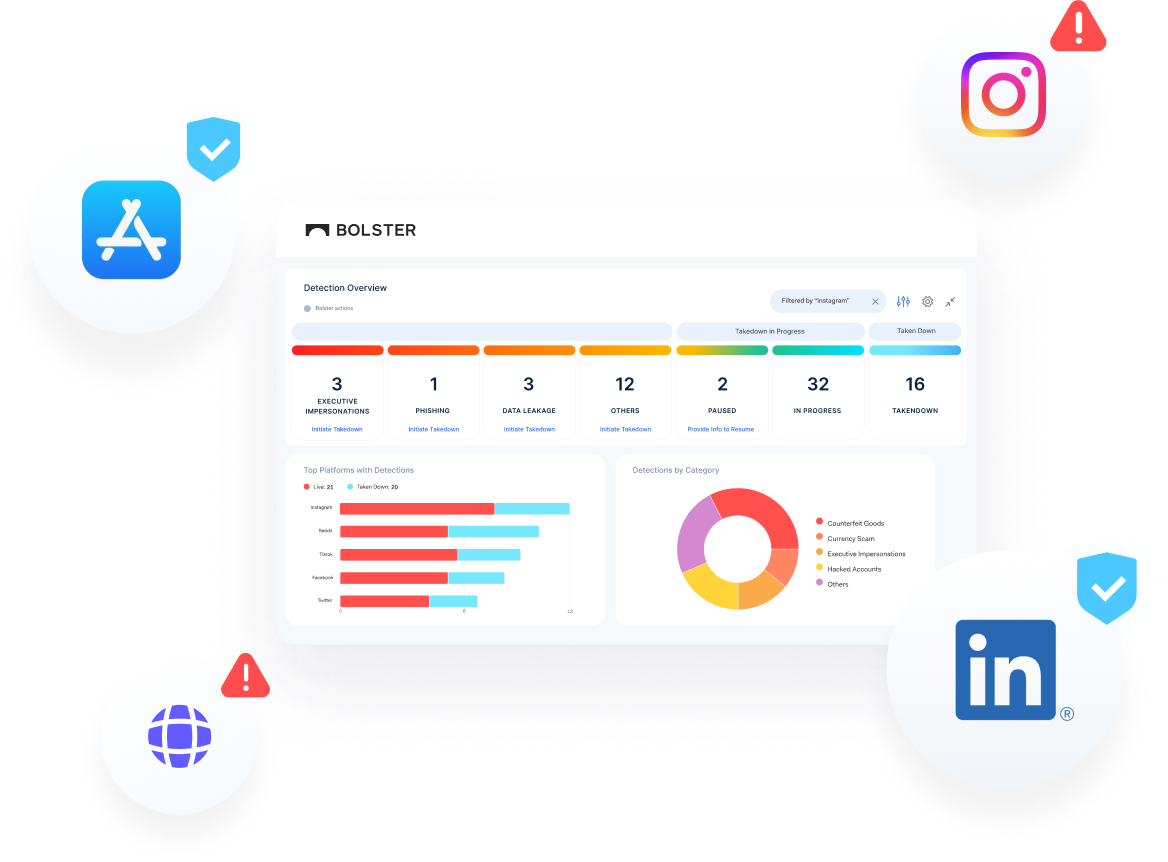
Industry’s Fastest Takedown Speeds
Bolster’s automated takedown with leading AI models and direct integrations with hosting providers, social media platforms, and other technology partners allows for the fastest takedown speeds for brand and phishing protection.
60 sec
Mean Time to Response (MTTP)
95%
Without manual intervention
6.5 sec
Submission to Global Blocklists
24/7
Continuous post-takedown monitoring
The Only External Security Vendor That Provides Protection Throughout the Entire Threat Lifecycle
Bolster distinguishes itself as the unrivaled external security vendor in the industry by combining swift takedowns with proactive post-takedown monitoring, ensuring there are no reoccurrences of malicious activities, and providing comprehensive protection and visibility into the entire timeline and lifecycle of a online threat.
Lightning-Fast Responses with Takedown Requests
Monitor Post-Malicious for Continuous Protection

Reducing Takedown From Days to Minutes
Issues with jurisdiction, collaboration, verification, and quality of reporting data are the reasons why most fraudulent removals take an average of 10 to 12 days without Bolster. The longer a fraudulent site stays online, the more loss to the business and risk to consumers.
Time is Money
Speedy detection and take down are critical to protecting your business, employees and consumers who spend money on your trusted brand.
Bolster’s automated search and analysis find, analyze and remove sites with minutes. This is due to Bolster’s relationships with registries and hosting providers who accept the automatic takedown requests through API integrations with Bolster as well as Bolster’s own LLMs that expedite the correspondence.
Reducing Takedown From Days to Minutes
Issues with jurisdiction, collaboration, verification, and quality of reporting data are the reasons why most fraudulent removals take an average of 10 to 12 days without Bolster. The longer a fraudulent site stays online, the more loss to the business and risk to consumers.
Ready to get started?
Explore what Bolster can do for you with a custom demo for your online business to understand existing online threats and how Bolster can take them down. Contact our sales team for pricing and packages today.
Get 24/7 Support
Start Your Integration
Frequently Asked Questions
How does Bolster do DMCA and UDRP takedowns, which are part of domain takedowns?
DMCA takedowns of brand abusers focus on Digital Copyright infringements based on an outdated 2008 law. DMCA takedowns are difficult to execute, because they:
- Require site registration, image watermarking, and other maintenance on part of the brand
- Are mostly self-service, so following up on fraudulent sites means doing your own investigations, working with legal teams, and presenting the evidence.
- Can also be handled through dispute resolution brokers, DNS services, Whois, attorneys, and other third parties – but for a fee
ICANN-based UDRP takedowns focus mostly on URL cybersquatting, so they can be useful to detect potential phish sites before they are live. But these are also slow and cumbersome because:
- Takedowns are resolved by agreement, court action, or arbitration before a registrar will cancel, suspend, or transfer a domain name
- Complaints must be filed in the proper jurisdiction (which can be many in the case of prolific fraudsters)
- Complaints can also be handled through approved dispute-resolution broker (same as DMCA) on a per-fee basis
Can Bolster conduct domain takedowns across multiple fraudulent domains, registrars and hosting providers?
Yes! Bolster takes down fraud sites in near real-time across as many domains and hosting providers involved, eradicating this risk to consumers and their trusted brands.
How does Bolster conduct a domain takedown in so short a timeframe?
Bolster has relationships with leading registrars and hosting providers who use Bolster’s realtime protection API’s to accept and act on takedown requests. So, 75% of our takedowns occur within minutes through these automated API’s.
How do you conduct a domain takedown with a provider that does not have the Bolster API?
Hosting providers that do not use Bolster’s API’s will receive automated emails that present evidence with up to 25 attributes providing irrefutable proof of fraud. Because these reports are evidence-based, hosting providers trust the data and usually take down sites within 24 hours.
Once the sites are removed, how does Bolster stop these fraudulent sites from coming back?
Once Bolster analyzes and determines the site to be fraud, it automatically sends the fraudulent URL with proof of fraud attributes to global blacklists that then stop any rebuild of the site at the registrar level. Bolster also continuously scans for recurrences of fraudulent sites and has them removed the instant it finds them.
Can Bolster conduct domain takedowns that are hidden behind proxies?
Yes, Bolster can detect fraud and phishing sites hosted behind proxy servers, in cloud services, and elsewhere and still achieve the same fast analysis and takedown through Bolster partnerships with registrars and hosting providers.







