
Bolster AI Difference
Large structured datasets and near-perfect AI models deliver online threat detection and response with unparalleled speed, scale, and accuracy.
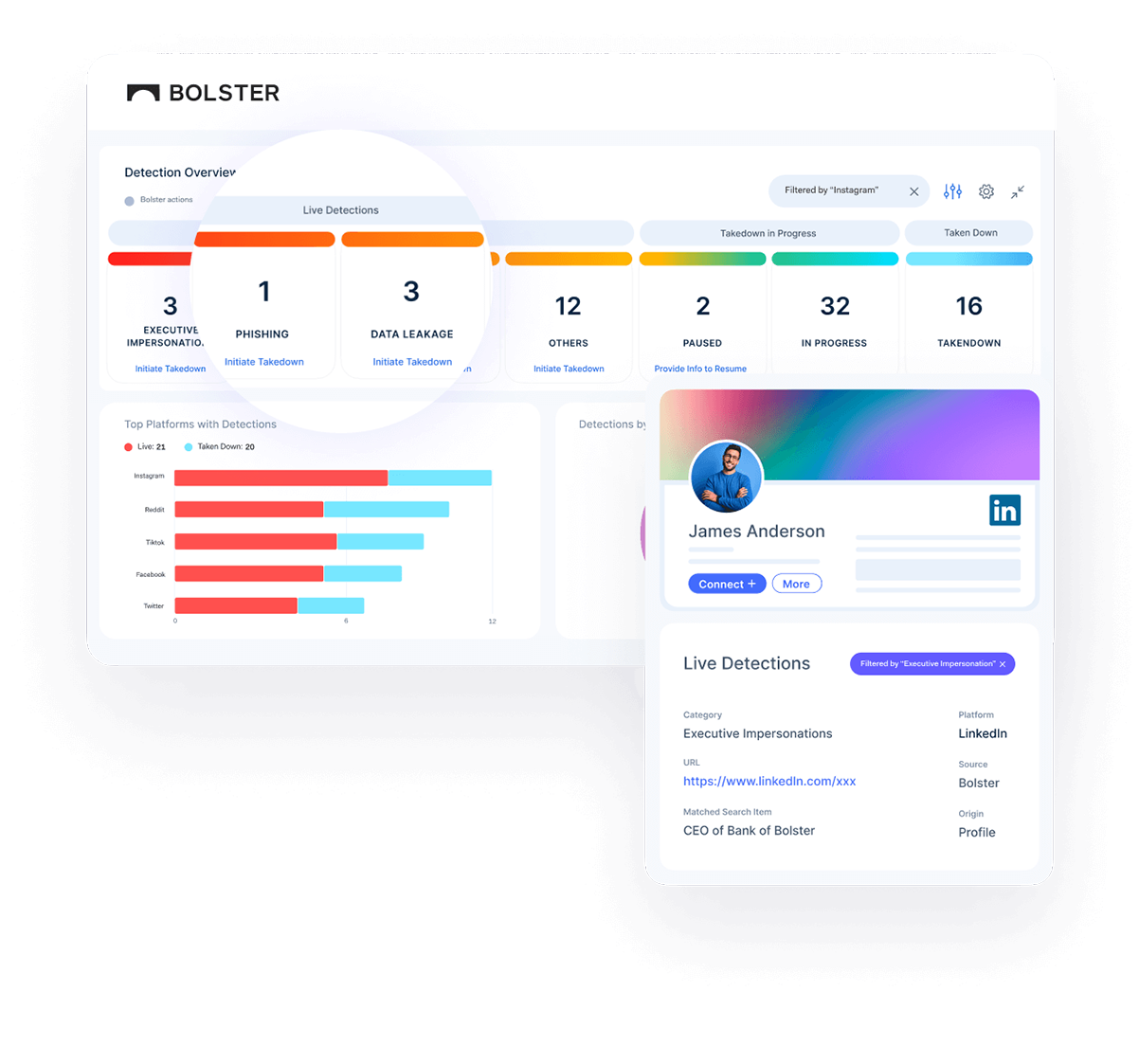
Using AI to Detect Threats Since 2019
99.999% Accuracy
Cutting-Edge AI
How Bolster LLMs and Computer Vision Works
Large Language Models
LLM models analyze vast amounts of text data to identify patterns, linguistic cues, and context indicative of fraudulent intent. With security prompts guided by our seasoned threat research team, these LLM models train on the evolving tactics used by attackers and recognize phishing and scam attempts in websites, emails, social media messages, and app stores and leverage RAG (retrieval augmented generation) to delivered automated, tailored takedowns.
Computer Vision
Computer vision allows for image and video processing and can identify visual cues commonly associated with phishing and scam activities (i.e. fake logos, misleading website interfaces, or deceptive content.) Bolster then trains large image datasets with models that scrutinize web pages, social media pages, and app stores for anomalies, recognizing patterns consistent with real-life fraudulent activities.
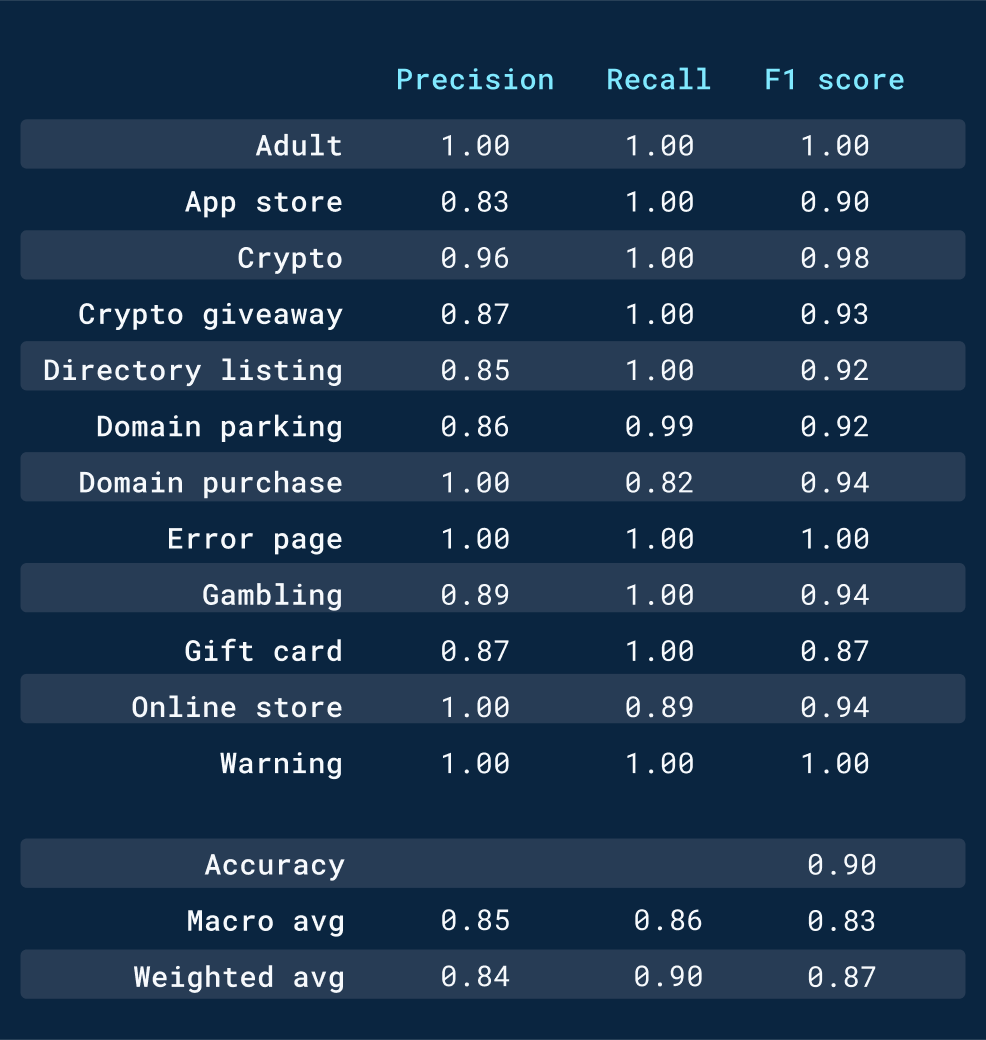
Near Perfect AI Models
Here at Bolster, we have a commitment to perfection in AI deployment. Unlike many counterparts, Bolster adheres to a rigorous standard, refraining from deploying AI models until they attain near-perfect precision, recall, and F1 scores. This meticulous approach ensures that the models excel in accurately detecting and combating phishing, scams, and impersonations online. By demanding the highest confidence scores trained on millions of data points, Bolster sets the benchmark for AI detection and response.

How Bolster AI Stacks Up Against the Competition?
If you’re just focused on takedowns, the damage is already done.
The best way to prevent damage to customers and your organization is to reduce the time to detect a threat. However, threat detection today mostly requires manual analysis by humans, making detection times take days or weeks.
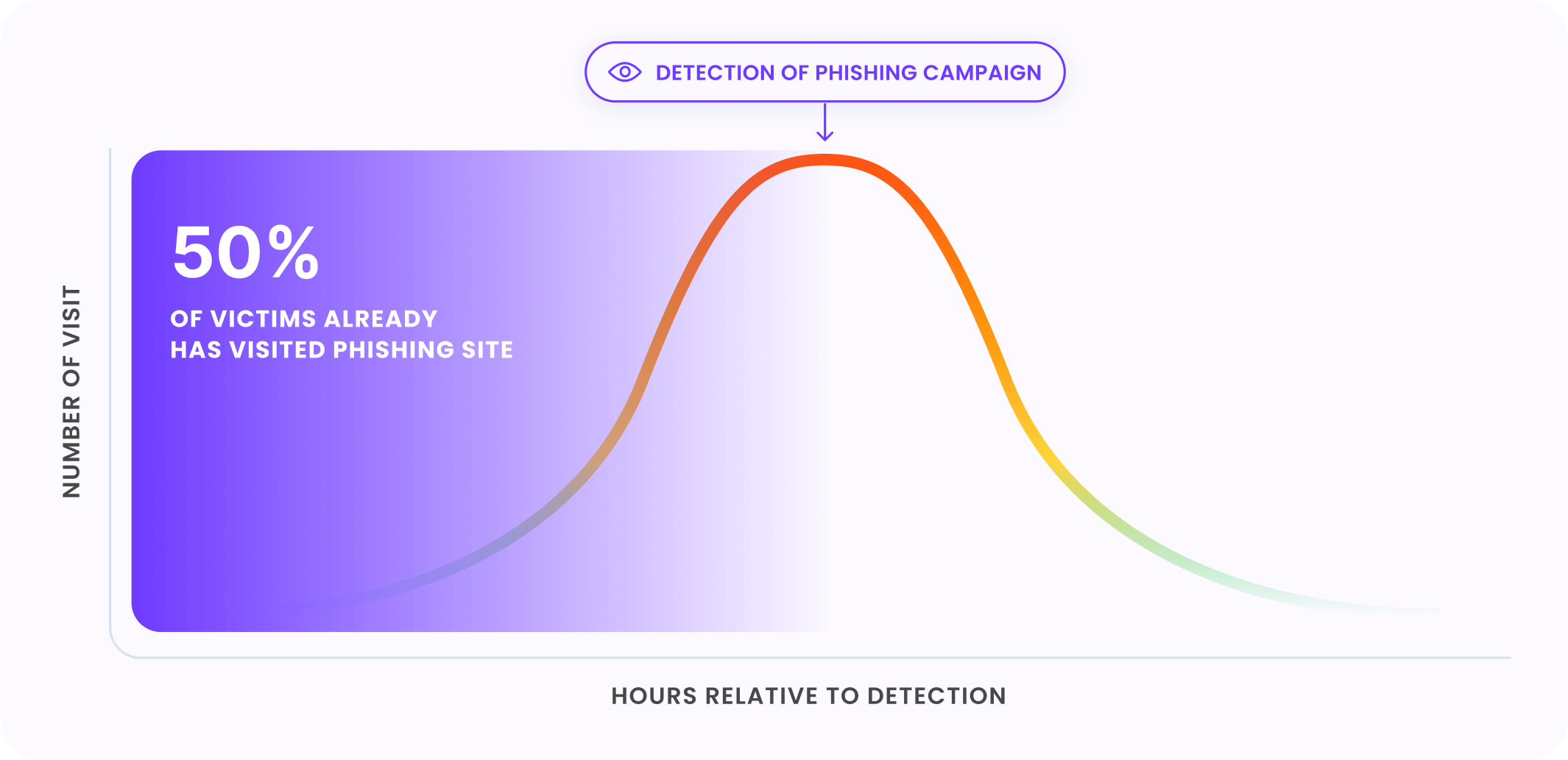

What’s Your MTTD?
Bolster’s scalable and patented AI detection engine delivers industry-leading speed and accuracy, enabling the best mean time to response against phishing and scam attacks.
4M+
Records Analyzed by A.I. in a Full Browser Every Day
80%
Malicious Records Taken Down in First 6 Hours of Going Live
1/100,000
False Positive Rate to Deliver the Highest Accuracy
#1
Tool to Identify Malicious Typosquat Variants on the Web
Ready to get started?
Explore what Bolster AI can do for you and your business with a custom demo for your online business to understand existing online threats and how Bolster can take them down. Contact our sales team for pricing and packages today.





