Phishing Kits 101: How to Identify and Mitigate Attacks
Phishing is one of the most common cyber threats to organizations, and phishing kits are a significant reason for this. A phishing kit is a set of tools that enables attackers to create convincing fake websites or emails that trick users into divulging sensitive information. In this blog post, we’ll explore what phishing kits are, how they work, why they’re dangerous, and how you can protect yourself and your organization against them.
What is a phishing kit?
A phishing kit is a collection of tools and html and php code that even cybercriminals with low level skills use to create and launch phishing attacks. These kits typically include pre-designed email templates, fake login pages, and other components needed to trick victims into divulging sensitive information such as passwords or credit card numbers. The goal of these attacks is usually to steal money or valuable data from individuals or organizations.
There are various types of phishing kits available in the underground market, ranging from simple ones with basic functionality to more advanced kits that can bypass common cybersecurity measures. Some kits even include features like automatic updates and encryption capabilities for added security. It’s crucial for IT security professionals to stay vigilant against these evolving threats by implementing robust defenses against phishing attacks and regularly updating their detection systems.

Definition of phishing kit
A phishing kit is a collection of code and tools that are used to create and deploy phishing attacks. These kits are often created by cybercriminals who want to steal sensitive information or gain access to systems through deceptive means.
Phishing kits work by mimicking legitimate websites or emails in order to trick users into revealing their login credentials, financial information, or other sensitive data. They may also contain malware that can infect the victim’s device once they have clicked on a fake link or downloaded an attachment.
Common components found in a phishing kit include:
- Fake login pages for popular websites such as banking sites
- Email templates designed to look like official communications from trusted sources
- Script files for automatically harvesting data entered into these fake pages
IT security and risk management professionals should be aware of the dangers posed by phishing kits and take steps to protect their organizations from these types of attacks.
Types of phishing kits
Basic phishing kits are the most common type of kit used in cyber attacks. These kits typically contain pre-written code and templates for creating fake websites or emails that mimic legitimate ones. They also include tools for collecting login credentials, credit card details, and other sensitive information from victims. Basic phishing kits usually have limited customization options but are easy to use even for non-technical attackers.
Basic phishing kits are easy to use but advanced/phishing-as-a-service (PHaaS) kits offer more customized and sophisticated features, making them even more dangerous for cybersecurity.
Advanced/phishing-as-a-service (PHaaS) kits take phishing attacks to a new level by offering more customized and sophisticated features than basic kits. PHaaS providers offer a wide range of services, including access to advanced malware, social engineering tactics, domain registration services, and custom email campaigns that can bypass traditional cybersecurity measures. Customized/specialized phishing kits for specific targets or industries are also available through PHaaS providers.
Overall, IT security professionals must remain vigilant against all types of phishing attacks as they evolve with advances in technology and increasing sophistication on the part of attackers using these highly effective scamming techniques.
How do phishing kits work?
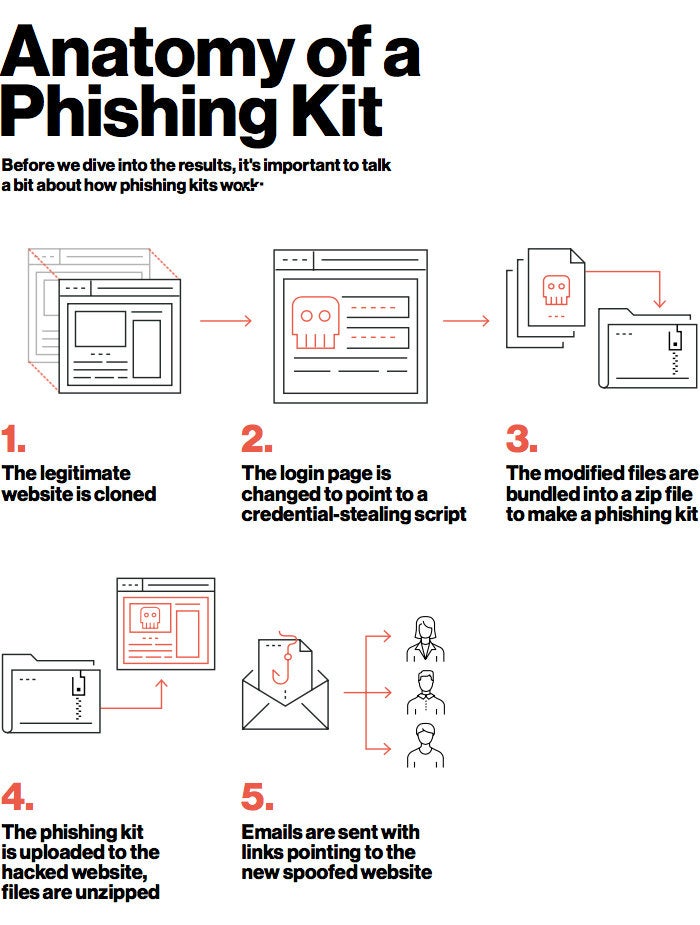
Phishing kits are essentially pre-packaged sets of tools that enable cybercriminals to create and deploy phishing attacks with relative ease. These kits typically include everything from spoofed login pages to email templates designed to look like legitimate messages from trusted sources. Once a victim falls for the bait, their credentials or personal information can be harvested by the attacker, who can then use it for a variety of malicious purposes.
The step-by-step process of using a phishing kit is relatively straightforward: first, an attacker identifies their target and determines what type of message or lure will work best. They then select an appropriate template from the kit, customize it as needed, and deploy it via email or social media channels. The victim is tricked into entering sensitive information on a fake page created by the attacker; this data is then collected and used for various fraudulent activities such as identity theft or financial fraud.
Step-by-step process of a phishing attack using a kit
Setting up a phishing attack using a kit involves acquiring and customizing the kit to create fake login pages, forms, and other fraudulent content. After setting up the kit, attackers need to develop interesting and convincing bait content in the form of email messages or social media posts to lure victims into clicking on links or entering sensitive information.
Once the bait is created, attackers deliver it by sending out fraudulent emails or social media posts to targeted individuals or groups. The goal at this stage is for victims to click on embedded links that lead them to fake websites where hackers can collect data such as login credentials.
After collecting sensitive information from victims through fake login pages, forms, etc., attackers use stolen data for malicious purposes such as financial gain through unauthorized transactions or identity theft. Hackers may also attempt further attacks by exploiting stolen information from compromised accounts.
- Acquire and customize phishing kit
- Develop convincing bait content
- Send fraudulent emails/social media posts
- Collect sensitive victim data through fake webpages
- Exploit stolen data (financial gain/identity theft/hacking attempts)
Why are phishing kits dangerous?
Phishing kits are dangerous because they make it easy for cybercriminals to create and distribute convincing phishing emails. These kits typically include pre-built email templates, fake login pages, and other tools designed to trick people into giving away sensitive information like usernames, passwords, or credit card numbers. By using these kits instead of developing their own phishing campaigns from scratch, cybercriminals can save time and effort while still reaching a large number of targets.
The danger of phishing kits lies in their potential to cause significant harm to both individuals and organizations. Once an attacker gains access to someone’s personal information through a successful phishing attack, they can use that data for identity theft or financial fraud. Additionally, if the target is an employee at a company with access to sensitive corporate data or networks, the attacker could leverage this stolen information for more sophisticated attacks like ransomware or business email compromise. Thus businesses need effective ways protect against these kind of attacks by educating employees on how not fall prey on such scams as well as implementing security solutions capable enough detect such malicious activities .
Impact on individuals and organizations
Phishing attacks can have a devastating impact on both individuals and organizations. Hackers use these attacks to steal sensitive information like login credentials, credit card numbers, and personal identification details. This type of data breach can result in significant damage to an individual’s financial security, reputation or organizational structure.
Recent high-profile phishing attacks include the Google Docs scam that affected over one million users in 2017 and the WannaCry ransomware attack which caused billions of dollars in damages worldwide. Both examples demonstrate how successful phishing techniques lead to severe consequences for both individuals and organizations.
A successful phishing attack can also lead to data breaches or losses of millions of dollars if attackers gain access to payment systems or internal networks. Once hackers obtain valuable information through a spear-phishing attack they might sell it on criminal markets or use it as leverage against their target organization further complicating this issue for IT Security professionals who must remain vigilant at all times.
The cost of a successful phishing attack
Successful phishing attacks can have significant financial impacts on organizations. Estimates suggest that the average cost of a successful phishing attack can reach up to $1.6 million, taking into account expenses related to investigation, recovery, and legal fees. However, non-financial costs such as reputation damage and loss of customer trust could have a more profound impact on an organization’s future success.
The cost of a successful phishing attack may vary depending on several factors such as the industry sector or type of data targeted by attackers. For example, healthcare organizations dealing with sensitive patient information are at higher risk for costly breaches than businesses in other sectors. Similarly, if attackers successfully obtain access to highly confidential data like credit card information or intellectual property rights, the damages caused could be considerably higher compared to less sensitive information breaches.
How to protect against phishing kits
Phishing kits are a major threat to an organization’s security. To protect against these attacks, it is essential to provide regular employee training and awareness programs on how to identify and avoid phishing attempts. This can help reduce the success rate of phishing attacks and prevent data breaches.
In addition, choosing the right security solutions such as anti-phishing software or email filtering can also significantly reduce the chances of successful phishing attacks. However, it is important to continuously monitor and test these solutions to ensure they are effective in detecting new types of phishing techniques that attackers may adopt over time. By implementing these measures, organizations can better protect themselves from falling victim to the harmful consequences of phishing kits.
Employee training and awareness
Employee training and awareness are critical components of any organization’s overall cybersecurity strategy. By providing ongoing education, employees can become better equipped to identify and mitigate potential cyber threats.
One effective way to increase employee awareness is through regular phishing simulations. These exercises simulate real-world attacks, allowing employees to recognize the signs of a phishing attempt and respond appropriately. Additionally, providing clear guidelines for email usage can help prevent accidental data breaches caused by human error.
Incorporating cybersecurity into employee onboarding is another important step in promoting a culture of security within an organization. New hires should be trained on best practices for password management, recognizing common scams, using secure networks when working remotely, and reporting suspicious activity.
- Regular phishing simulations
- Clear guidelines for email usage
- Cybersecurity incorporated into employee onboarding
Choosing the right security solutions
When choosing the right security solutions for your organization, several options exist. First and foremost, selecting an anti-phishing solution that fits your organization’s needs is crucial in protecting against malicious attacks. This includes identifying solutions that can detect and block phishing emails before they reach employees’ inboxes.
Another important step is implementing two-factor authentication (2FA) as an additional layer of security for accessing sensitive data and systems. By requiring a second form of verification, such as a text message or biometric scan, 2FA makes it more difficult for attackers to gain unauthorized access.
Lastly, investigating and adopting advanced threat detection solutions can help organizations stay ahead of evolving threats. These tools use machine learning algorithms and behavioral analytics to identify potential threats in real-time, allowing IT teams to respond quickly before any damage is done.
Overall, by carefully selecting the right combination of security solutions tailored to your specific needs and continuously monitoring them with regular testing updates, you can significantly reduce the risk posed by phishing kit attacks.
Continuous monitoring and testing
Regularly performing vulnerability assessments, conducting penetration testing to identify gaps in security protocols and keeping up-to-date with the latest phishing trends and techniques are essential for maintaining a secure IT environment. Vulnerability assessments should be performed on a regular basis to ensure that any potential weaknesses within the system are identified before cybercriminals can exploit them. Penetration testing is also necessary as it allows companies to simulate real-world attacks and determine whether their security protocols are effective. Finally, staying up-to-date with the latest phishing trends and techniques is vital as these tactics evolve quickly.
By continuously monitoring and testing your IT systems, you can stay one step ahead of cybercriminals who use sophisticated methods like phishing kits to lure unsuspecting employees into giving away sensitive information. Regular vulnerability assessments combined with frequent penetration tests help ensure that all potential vulnerabilities have been addressed while keeping pace with evolving threats such as new types of phishing scams or social engineering efforts helps protect against future risks.
Phishing attacks are a common threat to organizations of all sizes, and they often come in the form of phishing kits. These kits make it easy for even low-level scammers to create convincing phishing campaigns that can lead to data breaches, financial loss, and other serious consequences. As an IT security and risk management professional, it’s your responsibility to protect your organization from these attacks. Here are some key strategies to consider:
Multi-Factor Authentication
Multi-Factor Authentication (MFA) is an essential layer of security that should be used whenever possible. By requiring a second form of verification, MFA makes it much more difficult for attackers to gain unauthorized access. This can include a text message, biometric scan, or other forms of authentication. By using MFA, you can significantly reduce the likelihood of a successful phishing attack.
Advanced Threat Detection Solutions
Advanced threat detection solutions can be an effective way to stay ahead of evolving threats. These tools use machine learning algorithms and behavioral analytics to identify potential threats in real-time. This allows IT teams to respond quickly before any damage is done. By adopting these technical solutions, you can significantly reduce the risk posed by phishing kit attacks.
Continuous Monitoring and Testing
Continuous monitoring and testing is essential for maintaining a secure IT environment. Regular vulnerability assessments and penetration testing can help identify gaps in security protocols before they can be exploited by cybercriminals. Staying up-to-date with the latest phishing trends and techniques is also vital, as these tactics evolve quickly over time. By continuously
Resources
Bolster Brand Protection Free Trial