Phishing attacks are the most common attack vector for hackers targeting brands of all sizes, costing brands across the market an average of $323 billion in damages yearly. With fraudulent emails, malicious links, and fake profiles inundating your employees and customers, it takes a robust cybersecurity detection and takedown strategy to fend off hackers that are maturing and expanding.
Many security teams are turning to web beacons to help detect phishing activity before hackers can successfully target their organization.
Web beacons are used to check whether a user has accessed a piece of content or a specific resource, or to track the behavior of a user through webpages. Web beacons can be used to track whether a user accessed a certain web page, url, or a file. They can also be used to track if an email has been opened. Web beacons, to some extent, offer tracking just like cookies.
How Do Web Beacons Work?
Before diving into how web beacons can be used as a tool to combat phishing attacks, let’s look at how they actually work. Emails and webpages distributed by organizations use a tiny invisible pixel image or other downloadable asset. This pixel image can be used to track the user activity by analyzing access logs for those downloadable assets, such as which IP accessed the asset, at what intervals, and including what type of characteristics.
Another way of analyzing webpage-based web beacons is through JavaScript (JS). If a page is rendered, and JS code is executed, the web beacon then makes a request to a tracking server with metadata about the user’s device. JavaScript-based implementation is also referred to as JavaScript tags.
Events and assets tracked by web beacons can gather different types of information, including the visitor’s IP address, the time the visit occurred, the URL or domain of the page on which the web beacon was triggered, any referrer or site headers, and the user agent string which can reveal details about the device and browser. Geo-location and ISP data can also be obtained through the visitor’s IP information.
Identifying Brand Impersonation and Phishing Attempts Using Web Beacons
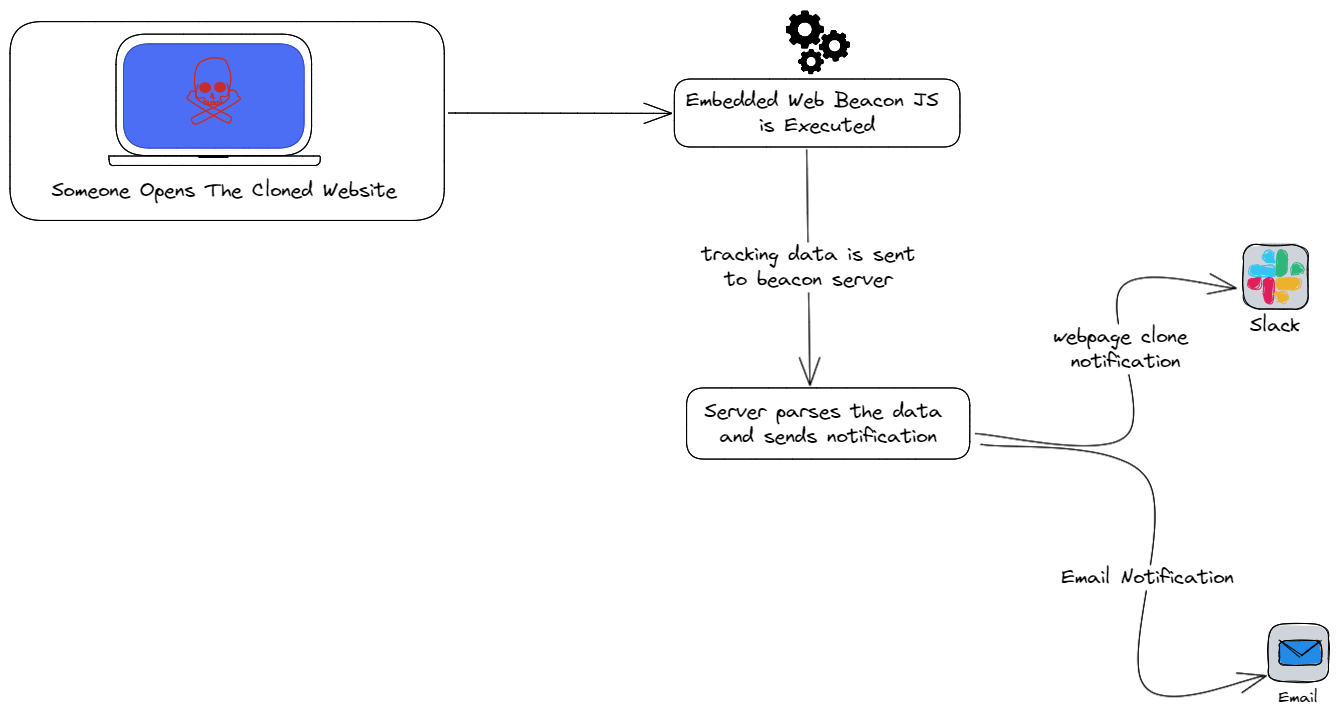
In certain scenarios, cybercriminals may clone your brand’s webpages with the goal of creating phishing and scam pages.
To combat this, you can integrate web beacon JS within your webpage’s Document Object Model (DOM), which will trigger if the webpage is hosted or visited on any domain that is not on your organization’s allow list.
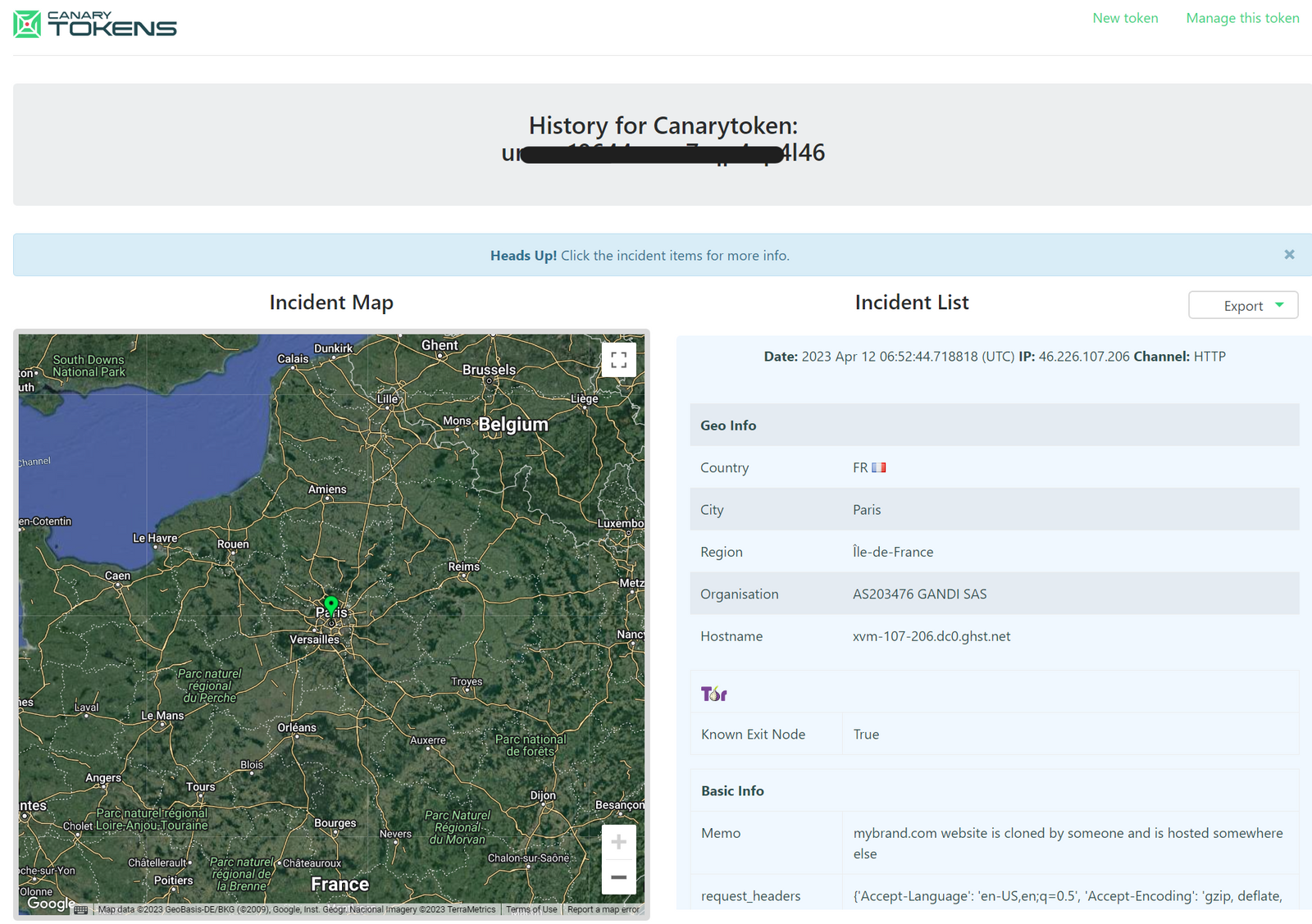
It is possible that the initial triggers of the web beacon will be by threat actors during their testing of the phishing pages. These initial triggers can allow your security team to gather valuable threat intelligence on the IP addresses and geo-location of the threat actors who are targeting your brand.
Are There Open Source Web Beacon Tools?
There are many tools out there for your security team to utilize web beacons to track potential phishing activity, as well as anti-phishing detection and monitoring software.
We’ve highlighted one open source tool open for analyzing web beacon data below:
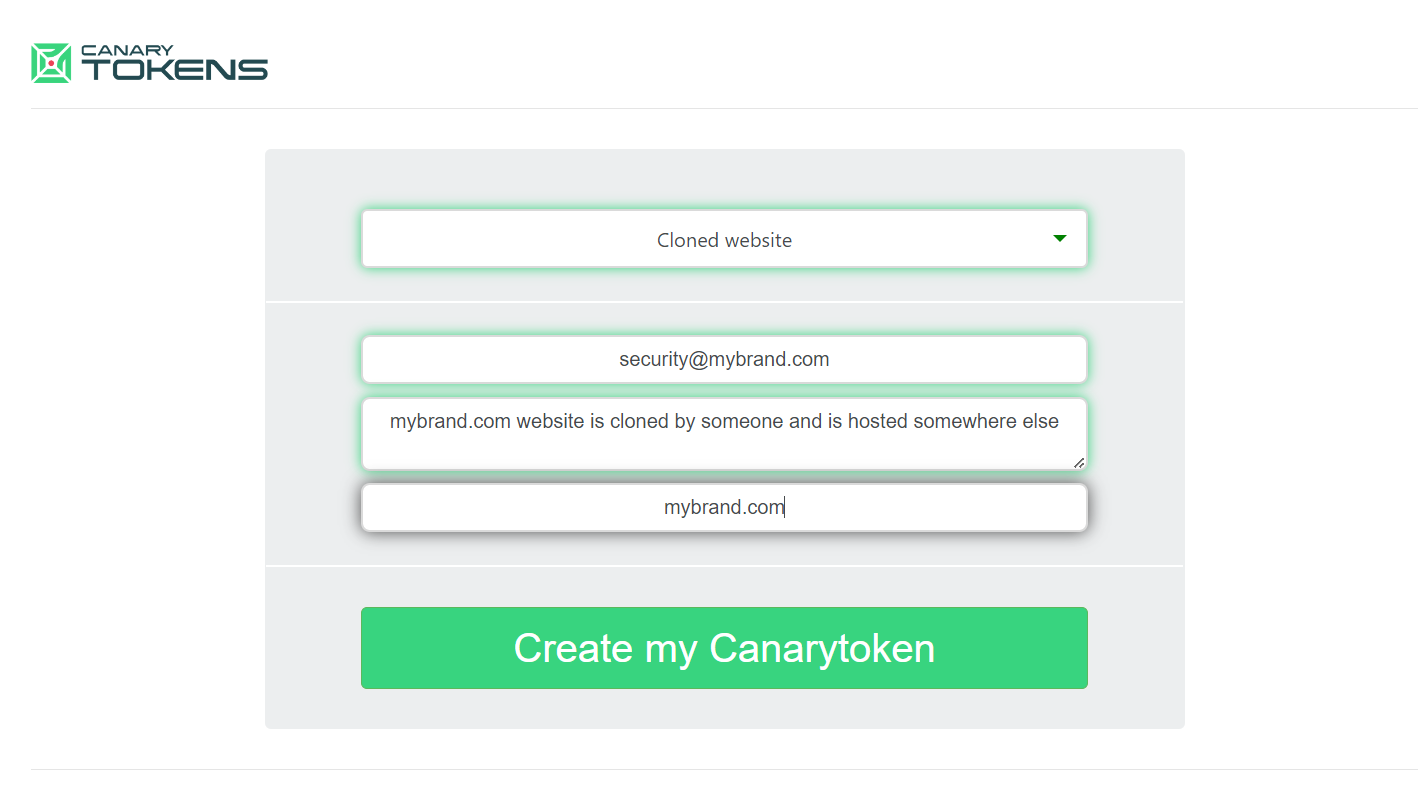
Canary Tokens
Canary Tokens is a freely available open-source web beacon service. Canary Tokens helps users create different kind of tokens, including cloned websites, pdf files, and executables.
What Are the Limitations to Using Web Beacons for Phishing Detection?
While web beacons can be a great tool for identifying suspicious behavior on your website and surrounding your assets, there are some potential gaps in a web beacon’s detection where hackers might go by undetected.
Here are some potential limitations to consider:
- The embedded web beacon JS within your webpage’s DOM will only work if the attacker has cloned your website and has not created a customized page.
- If the threat actor has detected and removed the web beacon JS, then subsequently there will be no way to track your assets.
- The attacker may attempt to overload or conduct a Distributed Denial-of-Service (DDoS) attack on the web beacon endpoint by sending a large volume of spam requests and thereby making it difficult to track suspicious or malicious activity.
One way to minimize the potential risk of these limitations is to use a JavaScript obfuscation tool, such as javascriptobfuscator.com, to obscure the web beacon JS code and thus making it harder for attackers to detect. By obfuscating the web beacon, organizations looking to protect their sites have a higher chance of successful detection and tracking.
However, it is important to note that obfuscation is not a foolproof method and determined attackers may still be able to identify and remove the web beacon JS, or find other ways to disable it.
Monitor and Take Down Phishing Attempts Today
Overall, web beacons can be an effective, proactive measure to safeguard your brand’s reputation and detect potential phishing and scam attempts that utilize a website clone. Since implementing web beacons doesn’t require significant manpower or finances, organizations can set up beacons quicjly without straining resources.
In the event that a cloned website is detected, web beacons allow you to take timely action to protect your brand and minimize the potential impact of the threat by issuing takedownsagainst the domains involved.
Bolster offers web beacon solutions to its customers as an added security measure to detect and mitigate phishing and scam attempts. We offer real-time detection and takedown of phishing, scams, and brand impersonation websites. If you are interested in exploring our offerings, start your free trial here.









