Shockwaves were felt when news hit Friday March 10th that a West Coast billion-dollar banking giant was predicted to collapse before the end of the day. This came at the heels of a earlier announcement that a prominent crypto-focused bank was expected to shut down operations.
Not long after, another billion-dollar East Coast banking giant followed suit causing growing concern over the back-to-back bank collapses in just a matter of days. Not just for the those with money in these bank’s accounts, or the many technology companies and young startups with ties to these banks; the fate of all banks across the country was brought into question.
How the recent crisis will impact the banking sector, and the economy as a whole, will continue to play out in the upcoming weeks and months, but there’s already emerging concerns the government regulators can’t protect us from.
Hackers acting on opportunity are using the current market environment to push out an exorbitant number of phishing and typosquatting attacks surrounding the banking, lending, and financial services space. Since Friday when the news began to spread through the tech world, there have been 14 fraudulent Brex domains registered, some placing above the legitimate Brex website on the first page of Google results. Seemingly legitimate Brex domains, like “brex-app.online” and “Brex-app.cloud”, are examples of domains registered in recent days, appearing like a trustworthy site, but deemed malicious based on network scans and analysis.
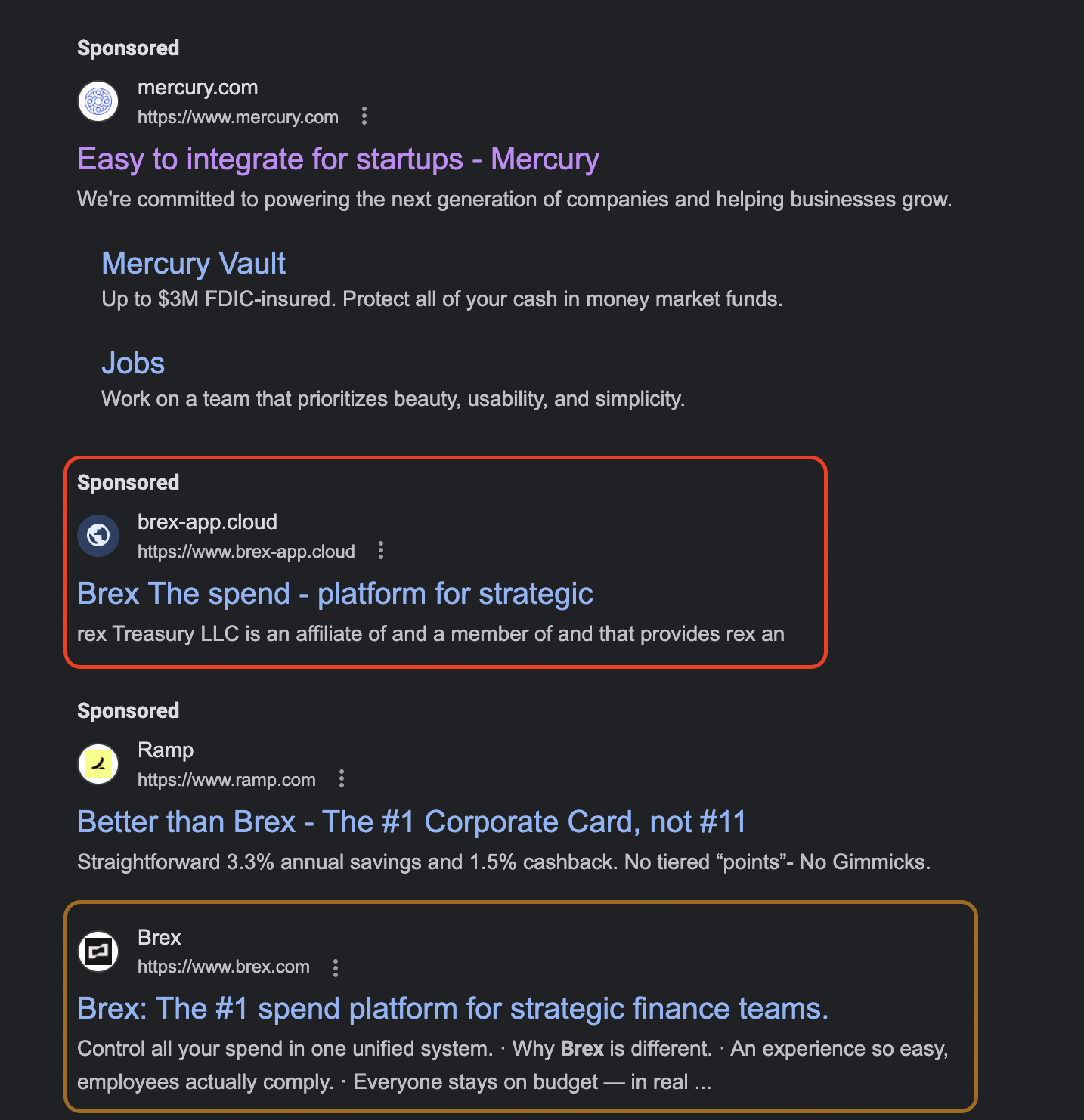
The Brex example is common: fake domains, app-store postings, and social media accounts for business in the startup lending and banking space are rapidly appearing in recent days.
What Our Research Shows
Through Bolster analysis of registered domains and public brand representation online in the last few days since the back-to-back bank collapses, we’ve discovered numerous instances of malicious activity surrounding the vulnerable technology sector. Sponsored websites and advertisements are appearing to mimic bankroll companies, lending organizations, banks, and the general Silicon Valley financial space.
Since the rumblings of the banking crisis, we’ve detected increased domain registrations for startup and banking related terms, including:
- 104 domains with the word capital
- 36 domains with the word investment
- 20 domains with the word founder
- 45 domains with the word startup
- 23 domains with the word investor
These domains are being registered by hackers to trick those impacted by the banking panic into giving up sensitive information and potential capital.
Simple searches for organizations that typically deal with startup bankroll or funding, like Silicon Valley Bank, First Republic Bank, or Capchase, will yield countless ads or sponsored domains that have just recently been registered or otherwise deemed malicious.
Why is This Happening?
If you’re asking why bad actors are jumping on the already messy and unfortunate environment impacting countless startups and tech investors, it comes down to trends we’ve seen too many times: hackers and cybercriminals exploiting highly emotional or fearful times to prey on individuals and businesses alike. When people are scared, or facing financial hardship, they may not exercise the same diligence against cybercrime, letting their guard down when their focus is on other important areas.
We saw this in the COVID-19 pandemic, when hospitals and organizations in the healthcare sector experienced more frequent cybersecurity attacks during periods of increased patient need and financial stress. Bad actors held hospital data for ransom, hacked into systems to promote operational disruption, and inundated healthcare employees and patients with attacks they knew companies would have to pay to fix as quickly as possible.
When industries are facing crises, everyday cybersecurity best-practices, phishing awareness, and reporting suspect activity take a back seat.
What to Look Out For
While staying vigilant against criminal hacker activity might not feel like the most important thing for yourself or your business, falling victim to a phishing attack would only intensify an already difficult situation. Being aware of the most prevalent attack vectors these scammers are utilizing can help prevent you or your business from becoming a victim and initiate the mitigation of malicious activity when it’s detected.
The most common attack vectors we’ve identified for these phishing scams include:
1) BEC: Scammers are utilizing business email phishing techniques to disseminate compromised links to gain access to sensitive company and employee information. With BEC scams, employees might receive an email from what looks to be someone from their company, their CEO, or their payroll or HR software, asking them to click a link or update their information. Employees of organizations experiencing impacts from the recent market disruption should be hyper-aware of emails asking for their information, requesting urgent actions, or including attachments.
2) Google Search Sites: As more and more companies are scrambling to deal with the impacts of bank closures and the confusion about the future, emerging trends show increasing scammer activity targeting Google searches related to banks, bankroll companies, startups, and similar terms. When looking for information online, especially when it comes to financial decisions or startup-related terms, be extra vigilant in choosing which sites to click into. Be extra observant of misspelt URLs or suspicious descriptions and content.
3) Social Media Accounts: In our digital age, consumers and businesses alike are turning to omni-channel online resources for news updates, and information about company’s financial well-being. This is creating a prime environment for social media impersonation scams, where hackers use a business or executive’s image, name, and brand elements to create fake accounts pretending to be them. It’s important to be cautious when interacting with accounts online, and to flag them to the host site if they’re acting unusual or phishy such as asking for money, sending links, or requesting credentials.
While these may be the most common scam tactics we’ve identified in the recent wake of the back-to-back bank collapses, this list does not include many other frequently used hacking methods and phishing techniques.
What to Do if Your Business is Impacted
Utilizing an automated, easy-to-implement technology partner to monitor the internet for impersonations of your organization and people can help prevent hackers from targeting your employees, potential customers, or business partners.
Bolster can help you detect phishing and scam activity across the open web, social media, and app stores, and automate the takedown of those sites, content, and accounts. With the increase in attacker activity targeting organizations that may be impacted by the recent bank collapses, it’s more critical now than ever to invest in your security posture. If you’re interested in how Bolster can help, or what our current data shows for your company’s domains, request a free demo today.